Assess Oracle Cloud Infrastructure (OCI) Security with cnspec
cnspec assesses your full Oracle Cloud Infrastructure (OCI) environment for misconfigurations that put your organization at risk. You can scan your OCI tenancy for compliance with security policies created by Mondoo or the community, or create your own policies. You also can write individual tests to run on the fly or include in automated tasks.
cnspec can test any aspect of your OCI configuration. For a list of OCI resources you can test, read Mondoo Oracle Cloud Infrastructure (OCI) Resource Pack Reference and Mondoo Core Resource Pack Reference.
Connect cnspec with your OCI environment
Requirements
To test your OCI environment with cnspec, you must have:
-
Access to an OCI tenancy
Configure command-line access to OCI
For cnspec to communicate with your OCI tenancy, you need to configure secure access from the command line. You download a private API key and create a config file to automatically authenticate you with Oracle.
-
In the top-right corner of the Oracle Cloud Infrastructure Console, select your profile icon and select My profile.
-
Under Resources, select API keys.
-
Select the Add API key button.
-
Leave Generate API key pair selected and select the Download private key button.
-
Create a new directory on your workstation,
~/.oci/, and move the downloaded private key file into the new directory. -
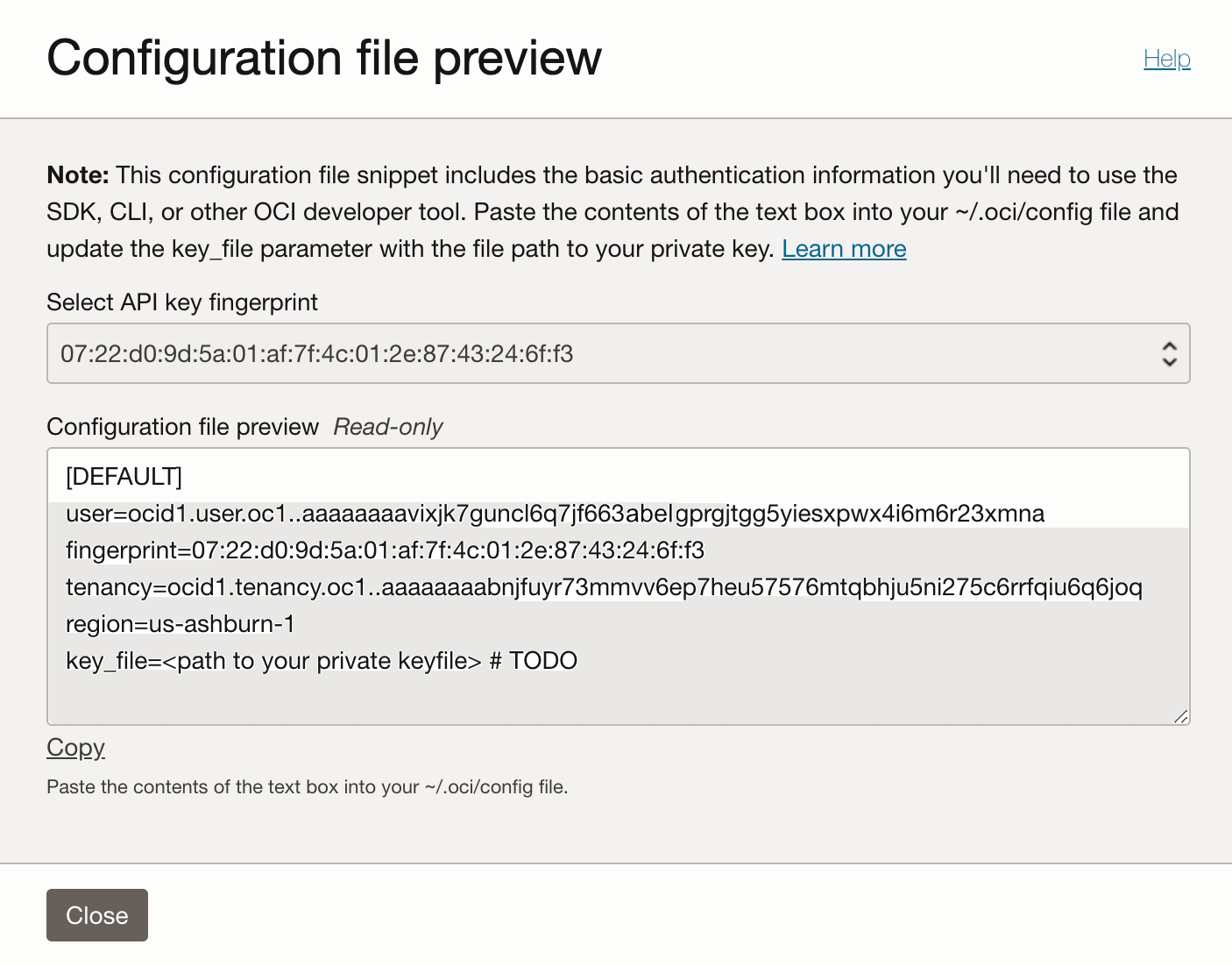
Select the Add button. OCI generates a config file for you. Copy the contents of the Configuration file preview box.
-
In the new directory, create a file named
configand paste the content you copied in step 6. Replace thekey_fileplaceholder on the last line with the path and file name of your private key file.[DEFAULT]
user=ocid1.user.oc1..aaaaaaaavixjk7guncl6q7jf663vyeygprgjtgg5yiesxpwx4i6m6r23xmna
fingerprint=c9:1d:c8:e1:54:26:b7:82:2c:7d:b5:be:0a:62:b7:b8
tenancy=ocid1.tenancy.oc1..aaaaaaaabnjfuyr73mmvv6ep7heu57576abelhju5ni333c6rrfqiu6q6joq
region=us-ashburn-1
key_file=/Users/stella/.oci/stella@lunalectric.com_2023-05-31T22_43_19.044Z.pem
Verify with a quick OCI check
To quickly confirm that cnspec has access to your OCI environment, run this check from your terminal:
cnspec run oci -c 'oci.tenancy { id!="foo" }'
It asserts that your tenancy does not have the ID foo.
cnspec indicates that the check is true, that your tenancy is not named foo:
oci.tenancy: {
id != "foo": true
}
You've successfully used cnspec to run your first check on your OCI environment. Now you're ready to explore. The method you choose depends on your goals:
-
For widescale assessment of your OCI infrastructure, scan using policy bundles. These collections of tests work together to present a broad picture of your OCI security posture.
-
To run ad hoc checks against your OCI environment, use cnspec's interactive shell. It has auto-complete to guide you, which is especially helpful when you're new to cnspec and learning MQL.
Assess OCI security with policy-based scanning
The CIS Oracle Cloud Infrastructure Foundation Benchmark policy is available to all in Mondoo's cnspec-policies GitHub repo. This collection of tests evaluates how well your environment follows fundamental OCI security best practices. It checks for misconfigurations across your entire OCI infrastructure.
To scan using the OCI Security by Mondoo policy, run:
cnspec scan oci
This scans the tenancy to which your OCI account gives you access.
cnspec follows these steps to load policies on which it bases the scan:
- cnspec tries to read a config file, mondoo.yml, which includes the certificate and private key for authenticating with Mondoo Platform. If it finds the config, it loads the policies enabled for the OCI integration in the Mondoo space this OCI environment belongs to. You can enter
cnspec statusto see if the config file exists and cnspec is registered.
- If there is no config file (you have not registered cnspec or you've removed the mondoo.yml file), then cnspec loads Mondoo's open source policies and scans based on those.
If cnspec is registered but you want to use the open source policies (and not share results with Mondoo Platform), you can scan in incognito mode:
cnspec scan oci --incognito
You can also specify a particular policy bundle. cnspec uses only the bundle you specify:
cnspec scan oci --policy mondoohq/oracle-cloud-infrastructure-foundation-level-1
You can also create your own policies to meet your specific needs. To learn more about policies, read Policies.
Test OCI with the cnspec shell
The cnspec shell is handy for quick checks and tests, or for developing your MQL skills. Its auto-complete and help features guide you in writing checks.
To launch a shell into your OCI environment, enter:
cnspec shell oci
Discover capabilities with the help command
Once inside the shell, use the help command to learn what OCI resources you can test. This command lists all the OCI resources:
help oci
From the resulting list, you can drill down further. For example, enter this command to list all the OCI Object Storage resources you can test:
help oci.objectStorage
From the resulting list, you can drill down even further. You can also learn about available OCI resources in the Mondoo OCI Resource Pack Reference.
Run tests in the cnspec shell
Now that you know how to discover what's possible with cnspec, let's run some actual tests in the shell.
Assess MFA for console users
This test assures that multi-factor authentication (MFA) is enabled for all users with console access:
oci.identity.users.all( mfaActivated )
If the test passes, that means all users have MFA enabled. If the test fails, cnspec lists all the user accounts that don't have MFA enabled.
[failed] [].all()
actual: [
0: oci.identity.user {
name: "mwezi@lunalectric.com"
mfaActivated: false
}
1: oci.identity.user {
name: "stella@lunalectric.com"
mfaActivated: false
}
2: oci.identity.user {
name: "tsuki@lunalectric.com"
mfaActivated: false
}
3: oci.identity.user {
name: "cosmo@lunalectric.com"
mfaActivated: false
}
]
Assess audit log retention
This test asserts that audit logs remain in storage for 365 days:
oci.tenancy.retentionPeriod == 365 * time.day
cnspec returns ok or failed and the actual retention time.
Exit the cnspec shell
To exit the cnspec shell, either press Ctrl + D or type exit.
Learn more about querying OCI
-
To learn more about how the MQL query language works, read Write Effective MQL.
-
For a list of all the OCI resources and fields you can query, read the Mondoo OCI Resource Pack Reference.