Note that this is an evolving situation, we’ll update this blog as soon as more information becomes available. July 21st, 2025 update: Patch released for Microsoft SharePoint Enterprise Server 2016 (see below).
What are CVE-2025-53770 and CVE-2025-53771?
Here’s a breakdown of each SharePoint CVE:
- CVE-2025-53770 is a critical unauthenticated remote code execution vulnerability caused by the deserialization of untrusted data in on-premise versions of Microsoft SharePoint Server. This CVE has been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
- CVE-2025-53771 is a medium-severity server spoofing vulnerability due to improper limitation of a pathname to a restricted directory.
These vulnerabilities are critical because they allow an attacker to fully access SharePoint content, including file systems, configurations, and execute arbitrary code over the network, without authentication.
Microsoft has also stated that CVE-2025-53770 and CVE-2025-53771 are related to two previous SharePoint vulnerabilities CVE-2025-49704 and CVE-2025-49706, which could also result in remote code execution. Microsoft released a patch for these vulnerabilities as part of the July 2025 Patch Tuesday update.
Microsoft said that ‘The update for CVE-2025-53770 includes more robust protections than the update for CVE-2025-49704, and the update for CVE-2025-53771 includes more robust protections than the update for CVE-2025-49706.
Who is affected by CVE-2025-53770 and CVE-2025-53771?
The ToolShell CVEs affect on-premises installations of Microsoft SharePoint Server, including SharePoint Server 2016, 2019, and Subscription Edition. Note that SharePoint Online in Microsoft 365 is not impacted.
How to remediate ToolShell
As mentioned it’s important to patch or mitigate these vulnerabilities immediately:
- If you haven’t done so already, install July 2025 Security Updates.
- Patch your SharePoint servers:
- If you have Microsoft SharePoint Server Subscription Edition: KB5002768
- If you have Microsoft SharePoint Server 2019 Core: KB5002754
- If you have Microsoft SharePoint Enterprise Server 2016: KB5002759 and KB5002760
- Rotate machine keys.
- If you cannot patch (for instance if you have SharePoint Enterprise Server 2016), and your SharePoint Server is exposed to the Internet, temporarily disconnect Internet access.
- Ensure the Antimalware Scan Interface (AMSI) is turned on and enable Full Mode for optimal protection, along with an appropriate antivirus solution.
- Check for indicators of compromise (see below).
Indicators of Compromise for CVE-2025-53770
To find out if your system has been compromised, check the following:
- Check for the presence of spinstall0.aspx: This file is a key indicator of post-exploitation activity.
- Look for suspicious file activity within the _layouts folders of SharePoint (e.g., Microsoft Shared\Web Server Extensions\16\TEMPLATE\LAYOUTS or Microsoft Shared\Web Server Extensions\15\TEMPLATE\LAYOUTS).
- Check if there are any unusual file names within the SharePoint installation directories or related web application directories.
Find and fix the security risks that pose the biggest threat to your business.
Problembehebung dreimal schneller mit Mondoo Unified Exposure Management
How Mondoo can help
Mondoo scans your Microsoft SharePoint servers for vulnerabilities and alerts if it detects CVE-2025-53770 or CVE-2025-53771. If either of these CVEs are found you can take fast action and create a remediation ticket straight from the platform.
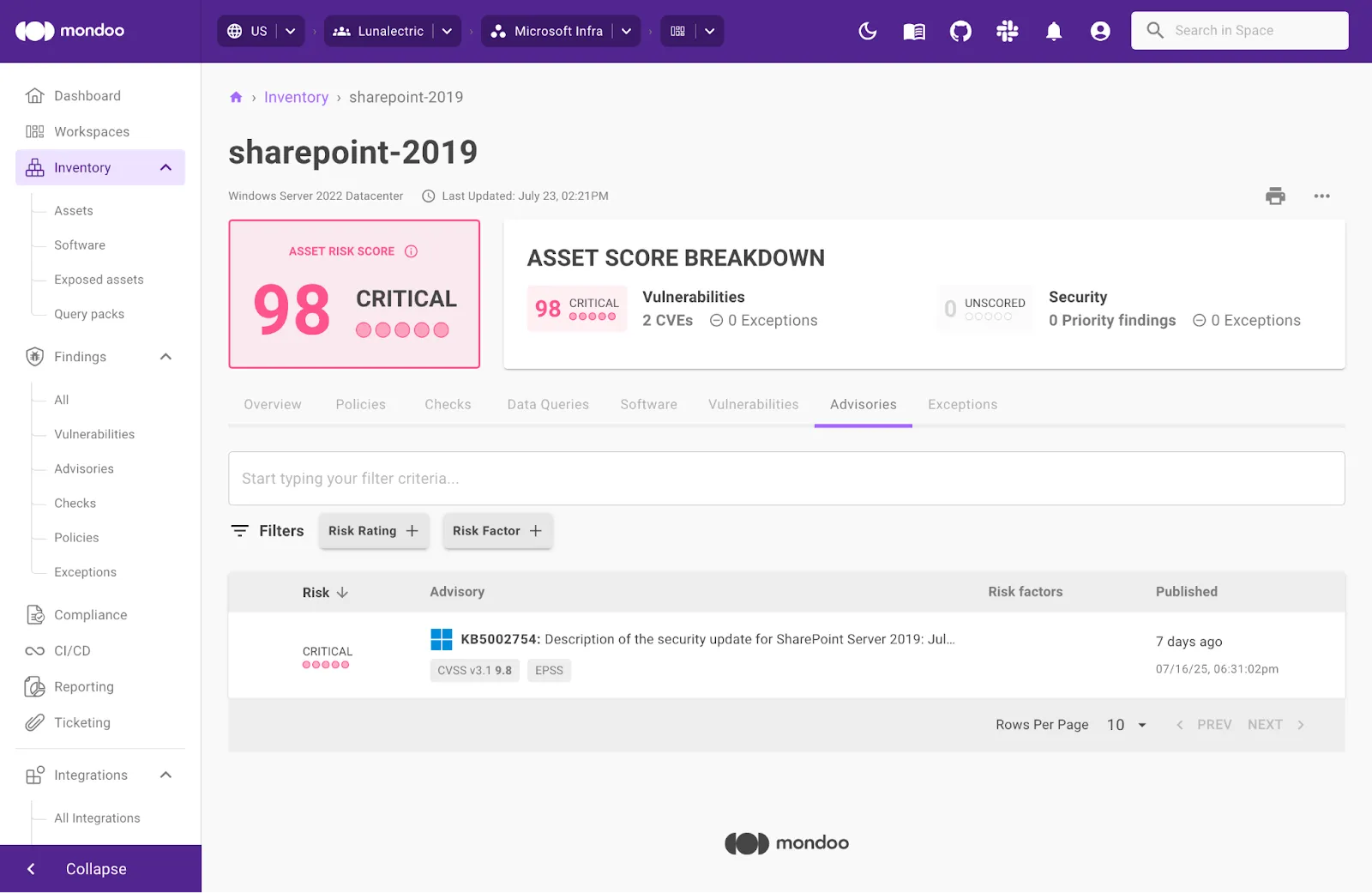
We’re actively monitoring the situation at Mondoo and will be updating the blog accordingly. If you need any help remediating these CVEs, please do not hesitate to contact us.
About Mondoo
Mondoo is an exposure management platform that identifies, prioritizes, and remediates vulnerabilities and misconfigurations in your entire IT infrastructure and SDLC from a single interface — including on-prem, cloud, SaaS, and endpoints. Unlike siloed approaches, Mondoo enables you to quickly understand your most urgent risks and initiate fast remediation, ensuring optimized security efforts and significantly improving security posture.









