Stay ahead of SLAs
Service Level Agreements (SLAs) for security findings are a fact of life, but keeping on top of findings before they violate their SLA sometimes feels like a full time job. In our 2025 State of Vulnerability Remediation Report, we found that only 60% of respondents measure SLAs, and of those that do, 65% need to track them manually in spreadsheets. Take the pain away with a new SLA experience that lets you prioritize which issues to tackle first to stay on top of SLAs.
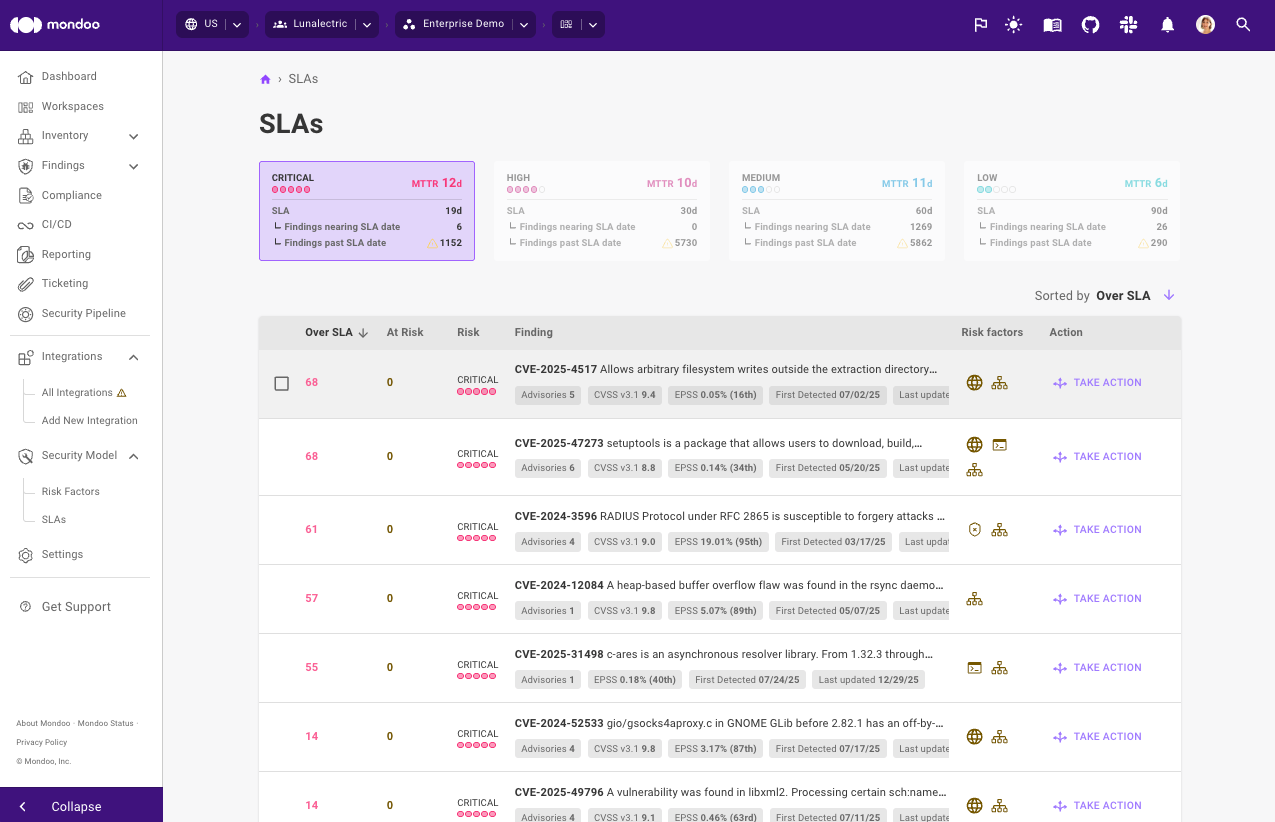
Now, you can click directly into SLA warnings on your Space or Workspace dashboard to instantly view the individual findings that are causing the failures. From this centralized findings view, you can take direct action to quickly remediate the issues:
- Easily create tickets in your issue tracker
- Set exceptions for findings that are not relevant
- Create Pull Requests (PRs) to automatically fix the problem
This new capability streamlines your workflow for addressing security compliance and helps ensure that your environments meet defined SLAs.
Expanded platform support
This month, we further enhanced our industry-leading platform support to cover all the latest and greatest systems. We added CVE and vendor advisory support for newly released operating systems such as Red Hat Enterprise Linux (RHEL) 10.1, SUSE Linux Enterprise Server (SLES) 16, openSUSE 16, and Windows 25H2. We also improved support for openEuler systems and ARM architecture systems such as the Raspberry Pi, keeping your infrastructure secure from cloud to IoT.
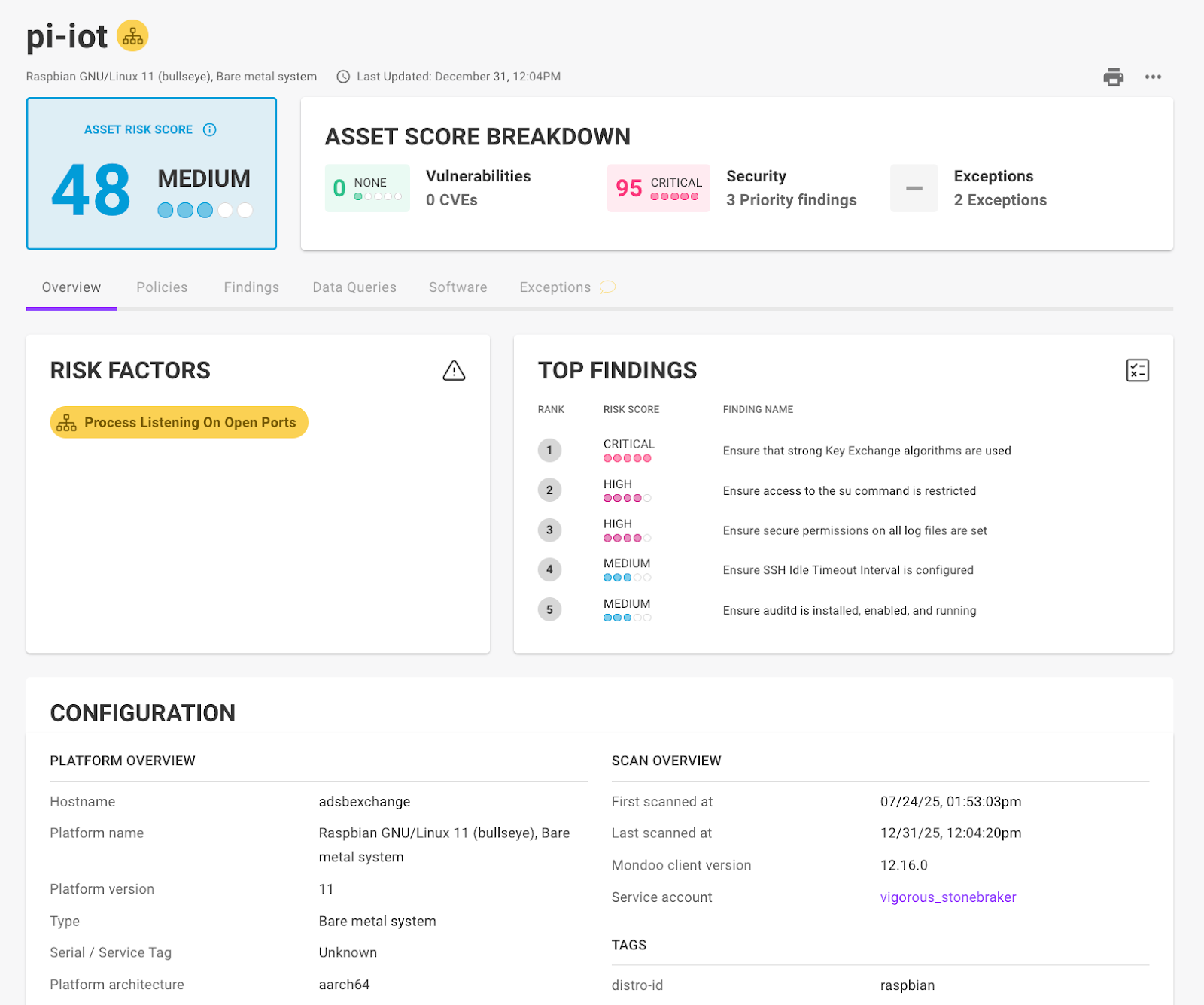
Policies, policies, and more policies
Security guidance only works if it’s up-to-date and supports the latest platforms and releases. That’s why we focus on continuously updating industry-standard security policies, giving you reliable, actionable insights into securing your infrastructure. This gives you the confidence to adopt new operating systems and cloud technologies from day one.
This month was a particularly busy month with updates for the new RHEL and macOS operating systems as well as a large number of new policies that include updated checks and improved remediation steps.
New policies:
- CIS Oracle Linux 10 v1.0
- CIS AlmaLinux 10 v1.0
- CIS Linux Mint 22 v1.0
- CIS macOS 26 Tahoe v1.0
Updated policies:
- CIS Oracle Linux 8 v3.0 -> v4.0
- CIS Red Hat Enterprise Linux 8 v3.0 -> v4.0
- CIS Azure Foundations v3.0 -> v5.0
- CIS macOS 15 v1.1 -> v2.0
- CIS macOS 14 v2.1 -> v3.0
- CIS macOS 13 v3.1 -> v4.0
- CIS GitHub v1.0 -> v1.1
- CIS Amazon EKS v1.6 -> v1.7
- CIS Microsoft AKS v1.6 -> v1.7
In addition to updates to CIS benchmarks, we focused on improvements to Mondoo’s proprietary cloud and Linux policies ensuring they detect the latest threats and support both real-world asset scanning and IaC code scanning:
- Expanded Mondoo AWS Security policy with 11 new checks including new checks for the AWS Security Gateway, IAM, and S3.
- Expanded Mondoo AWS Security and Mondoo GCP Security policies with additional Terraform checks to catch issues early in CI.
- Expanded Mondoo Linux Security policy with new checks for kernel hardening as well as improved support for ARM systems.
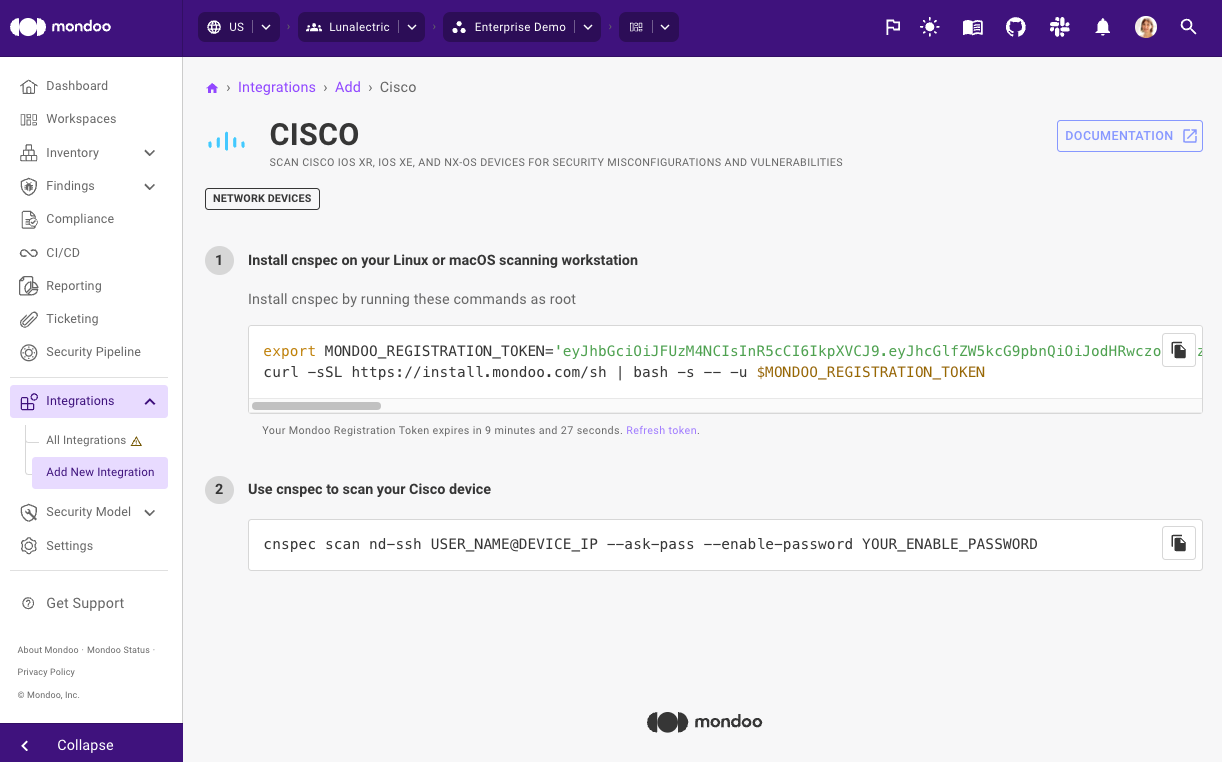
Simpler network device setup
Now it’s easier than ever to set up an integration to scan network devices such as Cisco, FortiOS, and PAN-OS for security vulnerabilities. Simply go to Integrations > Add and select your network device vendor. Copy and paste the code snippets to install Mondoo cnspec and start scanning.
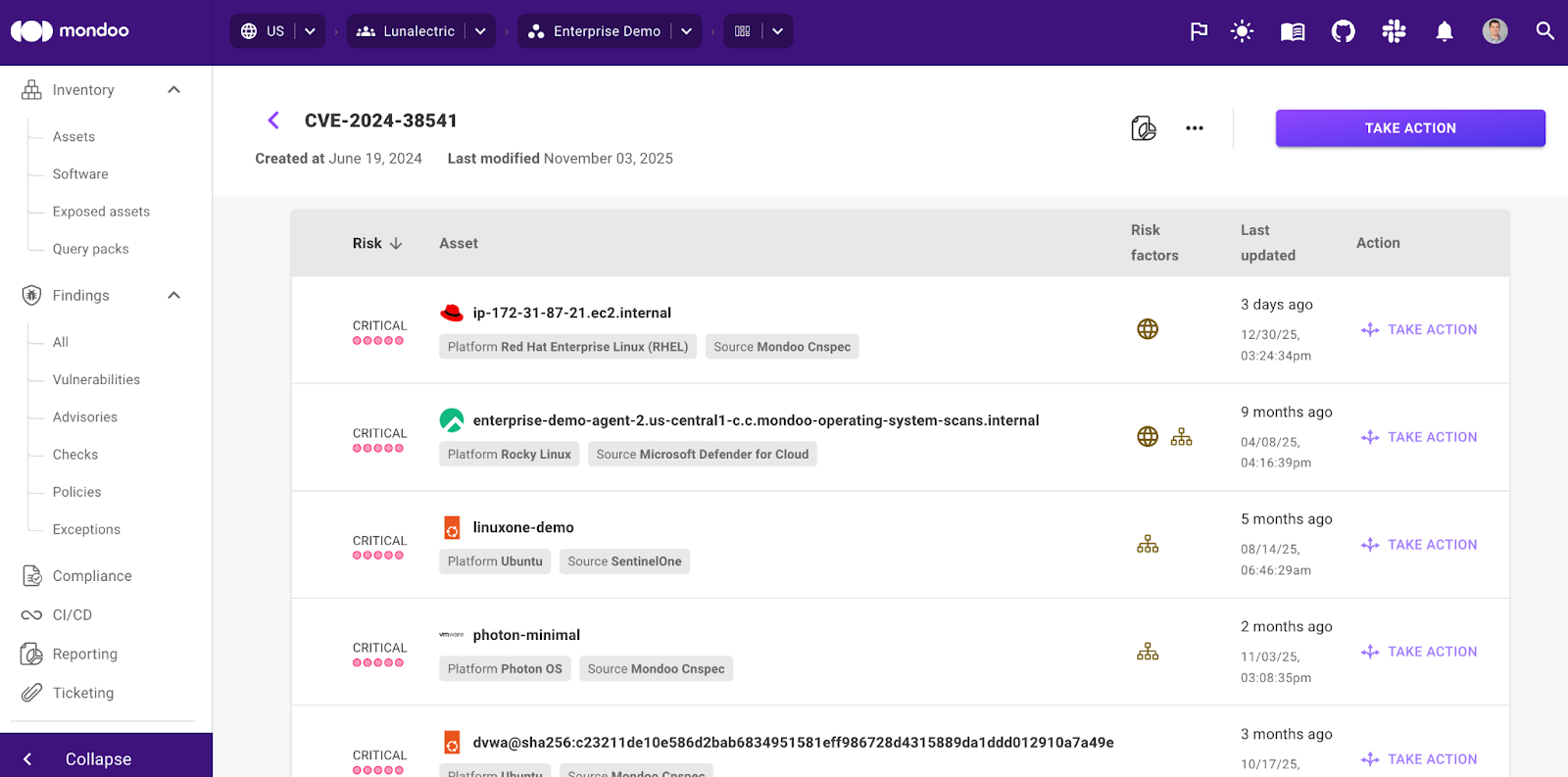
Enhanced vulnerability management features
We added a number of improvements to our vulnerability management features:
- Added remediation steps for findings on snap and apk packages.
- Improved NPM remediation steps when a package has available updates that resolve the CVE.
- Added more external links for CVEs with information about findings.
- Added CVSS scores to GitHub advisories.
- Show which scanning engine discovered vulnerabilities on an asset to better expose third party scanner results.
That’s it for December and a wrap on 2025! We can’t wait to share the many new exciting capabilities we’re releasing in January. Check back next month!








