According to data from the Mondoo platform, 82% of all iOS systems are pre iOS 26.2, making them vulnerable to CVE-2025-14174 and CVE-2025-43529. The vast majority (68%) are running iOS 26.0 or iOS 26.1, but have not yet upgraded to the latest version. The rest are using versions prior to 26. We strongly advise iPhone, Mac, and iPad users to upgrade their devices and recommend organizations to push the updates through their centralized endpoint management system without delay.
What is CVE-2025-14174?
This is a high-severity memory corruption vulnerability affecting the ANGLE graphics layer used in web engines, including Google Chrome on macOS and Apple’s WebKit browser engine. The flaw stems from out-of-bounds memory access triggered by specially crafted HTML content, allowing a remote attacker to corrupt memory and potentially execute arbitrary code simply by luring a user to a malicious webpage. It has been added to the CISA Known Exploited Vulnerabilities catalog.
What is CVE-2025-43529?
This vulnerability is a critical use-after-free bug in Apple’s WebKit browser engine that can lead to arbitrary code execution when processing maliciously crafted web content. It has also been added to the CISA Known Exploited Vulnerabilities catalog. This flaw affects Apple devices across iOS, iPadOS, macOS, tvOS, watchOS, visionOS, and Safari, and was actively exploited in highly targeted attacks before an emergency security update was issued. Apple’s patches for this and related WebKit zero-days have been released to address ongoing threats that do not require additional user interaction beyond visiting a hostile webpage.
Who is affected?
These CVEs affect users of Apple devices (iPhone, iPad, Mac, Apple TV, Vision Pro) running older software, specifically impacting the WebKit browser engine and leading to potential memory corruption, allowing remote code execution via malicious websites, and were actively exploited in targeted attacks before Apple patched them in updates like iOS 26.2, macOS Sequoia 15.7.3, and macOS Sonoma is 14.8.3.
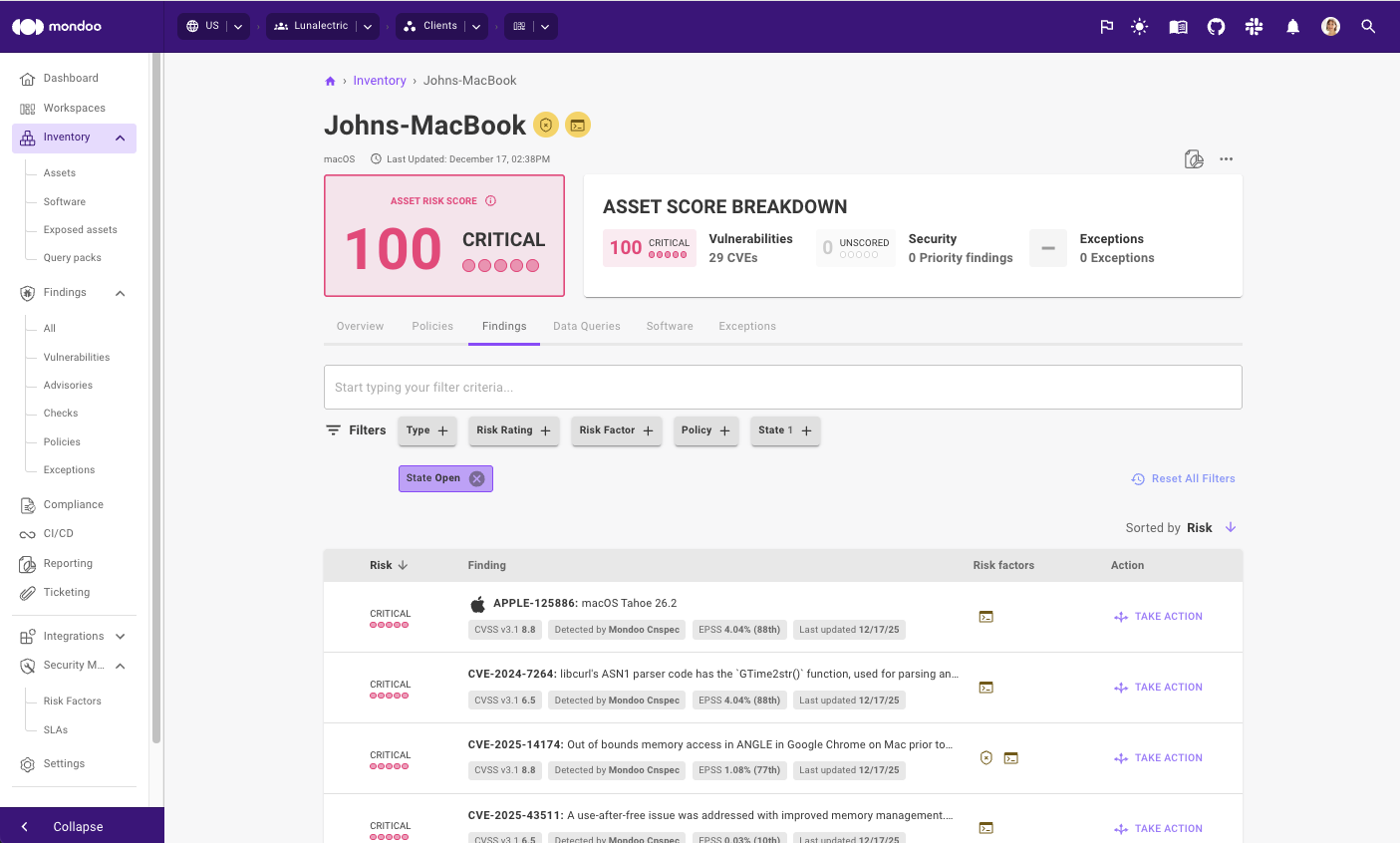
How can Mondoo help?
By scanning your entire IT infrastructure, including endpoints, cloud, and on-prem, Mondoo alerts if any of your Apple systems are vulnerable and need updating.
Find and fix the security risks that pose the biggest threat to your business.
Problembehebung dreimal schneller mit Mondoo Unified Exposure Management
Learn more about Mondoo
Mondoo eliminates - not just categorizes - vulnerabilities. Global enterprises trust Mondoo to prioritize risks by business impact and exploitability through its patented AI-native security model that collects structured, context-aware data from the entire IT infrastructure. Mondoo’s customers have reduced vulnerabilities and policy violations by 50% and significantly reduced MTTR. With seamless ITSM integrations and transparent security pipelines, Mondoo enables autonomous remediation and continuous compliance. Mondoo bridges the gap between security and engineering - delivering intelligent recommendations and actionable insights to fix vulnerabilities that matter most to the business.
Want to learn more? Schedule a demo today.








