Many vulnerability management tools are good at finding these issues, but they rarely offer the practical guidance teams need to fix them. That’s why we’re expanding Mondoo’s remediation coverage to include the most widely used applications, giving customers clear, actionable steps rather than static findings.
Application vulnerability pain points
All the usual pain points that plague vulnerability management in operating systems and OS-native applications also apply to third-party applications. Alert fatigue, siloed tools, missing context, weak prioritization, and lack of visibility.
But third-party applications introduce additional complexity, making detection and remediation even harder. Common issues are:
- Many false positives: This happens because vulnerability scanners don’t detect backported remediations and instead just focus on a software version number. This means that if packages have been fixed without updating the version number, vulnerability scanners will still flag it as vulnerable.
- Patches aren’t always available or timely: Operating systems generally receive patches quickly, but application vendors vary widely in their responsiveness. Some vendors are slow at releasing fixes, others do so inconsistently, and some not at all.
- Vulnerability management tools stop at detection: Many vulnerability management tools simply surface advisory data. Teams are left on their own to research and fix.
Application vulnerability management in Mondoo
To help address these challenges, we’ve made some major enhancements to Mondoo’s application vulnerability management capabilities, enhancing coverage, detection, and guidance:
- Expanded coverage: Mondoo now tracks vulnerabilities across a broad set of commonly used applications on Windows, macOS, and Linux. This includes software such as Adobe products, Notepad++, 7-Zip, Dropbox, TeamViewer, Microsoft 365, Google Chrome, Firefox, Microsoft Edge, and many more.
- Granular vulnerability detection: Mondoo recognizes when a vendor has backported a security fix, and avoids overreporting on vulnerabilities that have already been addressed.
- Complete remediation guidance: But here’s the thing: we don’t just detect vulnerabilities; we provide you with full remediation steps and ready-to-run code (e.g., PowerShell, Ansible, Terraform, and Shell). In addition to using CVE data sources and vendor advisories, the Mondoo research team investigates the issue to provide practical guidance, even when vendor advisories fall short.
Use case #1: 7-Zip vulnerability
Using a recent 7-Zip zero-day, we’ll demonstrate how Mondoo provides the necessary remediation information and helps you fix the issue with one click.
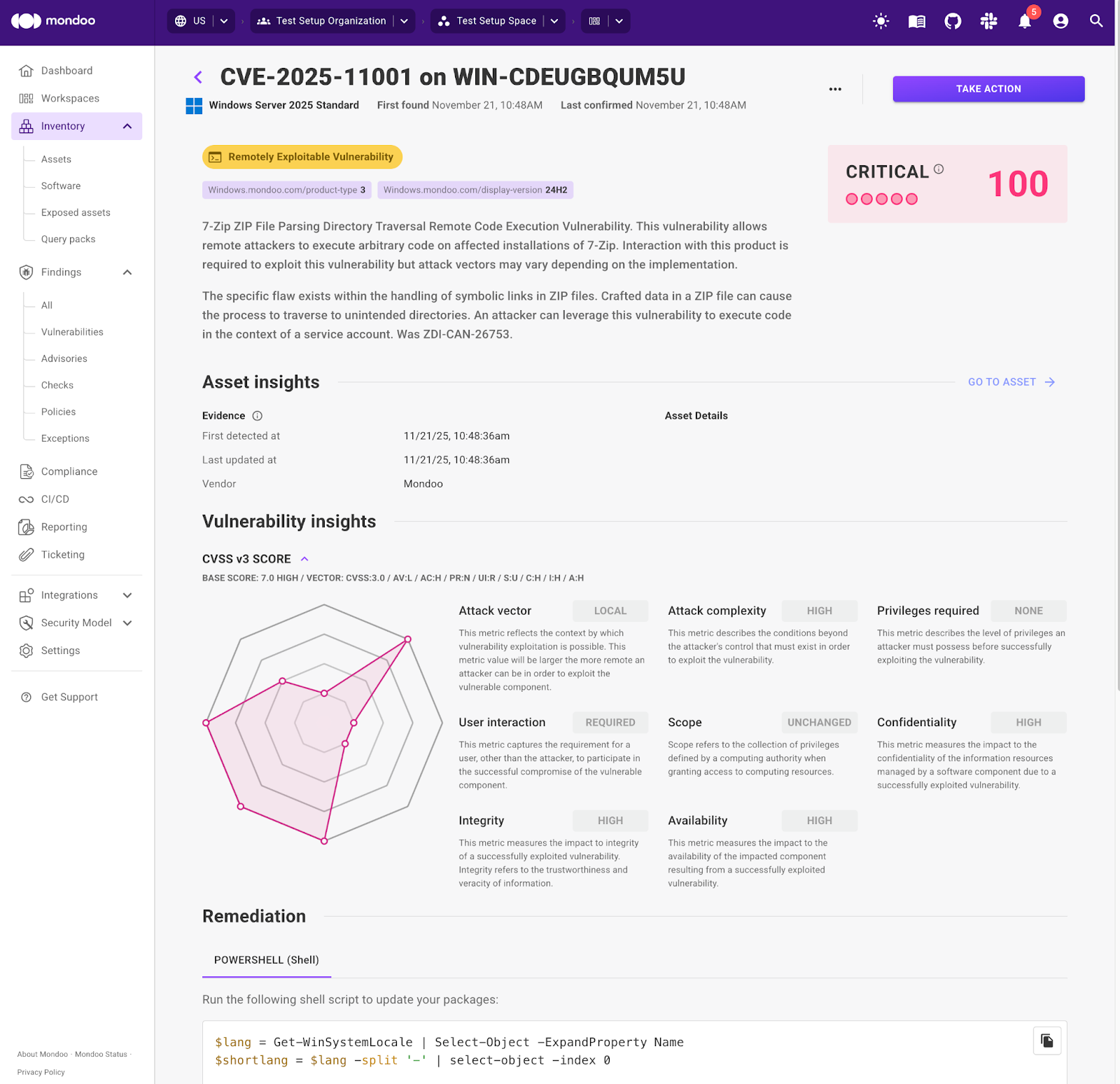
CVE‑2025‑11001: A recently disclosed zero-day vulnerability in the widely used open-source utility 7-Zip allows arbitrary code execution. A proof-of-concept exploit has been published, making rapid patching essential.
- Discover and prioritize: Mondoo scans the environment, identifies affected assets running vulnerable versions of 7-Zip, and surfaces the issue with the asset context needed to assess risk.
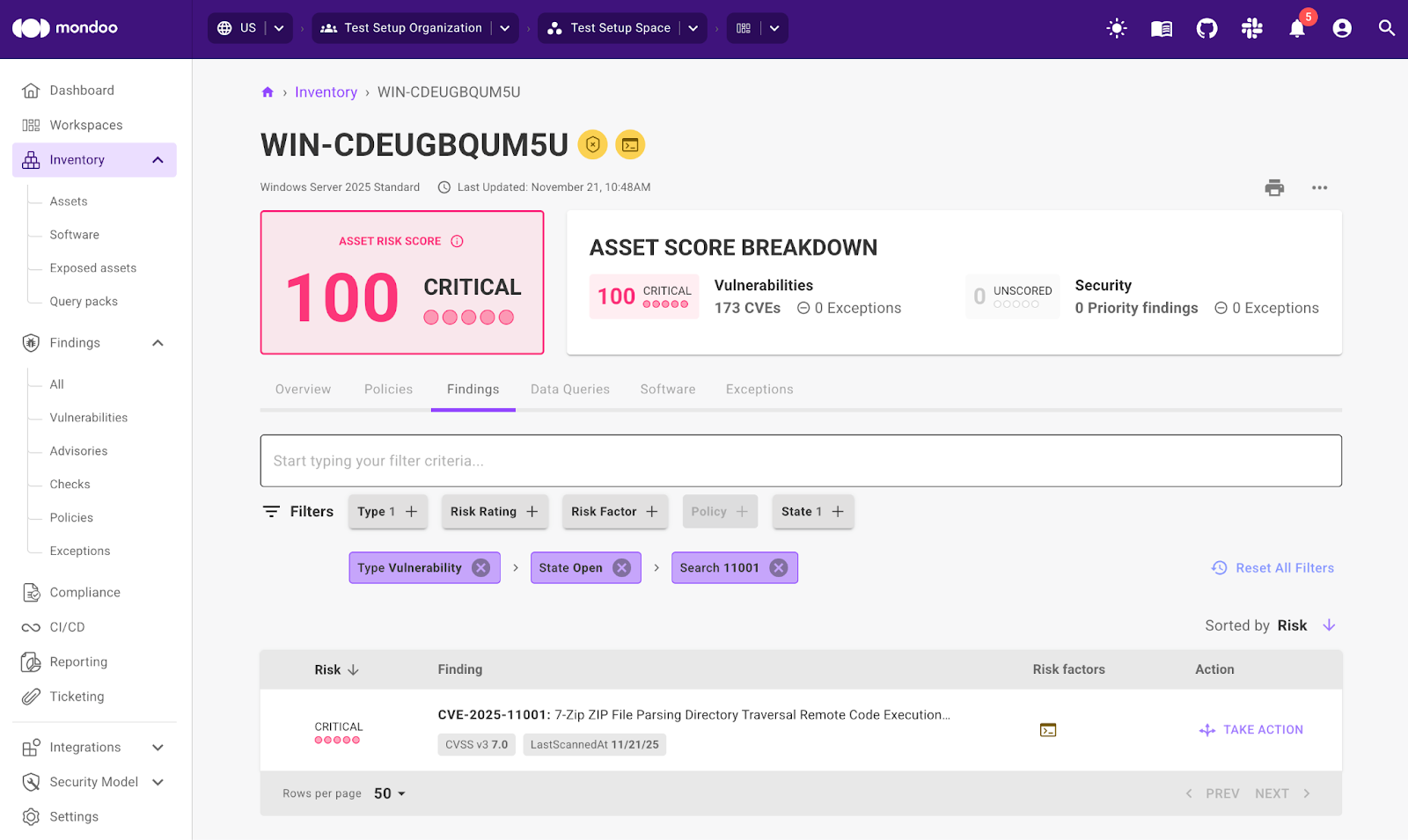
- Get context and guided remediation: Mondoo provides clear remediation guidance, including a pre-tested PowerShell script that updates 7-Zip to a safe version. Engineers can review, copy, and apply the fix immediately without hunting through vendor advisories.
- Hand off to IT Ops with full context: To bridge security and operations, Mondoo integrates with ITSM systems to create tickets that include asset details, remediation steps, and code snippets.
- Verify fix: Once the fix is applied, Mondoo re-scans the asset, verifies remediation, and automatically closes the ticket.
Use case #2: VMWare Tools vulnerability
VMware Tools often runs quietly in the background and is easy to overlook during routine patching. In VM-dense environments, it’s common for guest tools to drift out of sync with host updates, leaving long-lived exposure that’s difficult to track manually. By treating VMware Tools like any other application and tying detection directly to guided and automated remediation, Mondoo helps teams close a class of vulnerabilities that frequently persists unnoticed.
CVE-2025-22230: A high-severity authentication bypass vulnerability in VMware Tools for Windows that allows a local, non-administrative user to gain elevated privileges within a guest virtual machine (VM).
- Discover and prioritize: Mondoo scans the environment, identifies machines running vulnerable versions of VMware Tools, and surfaces the issue with asset and severity context to support prioritization.
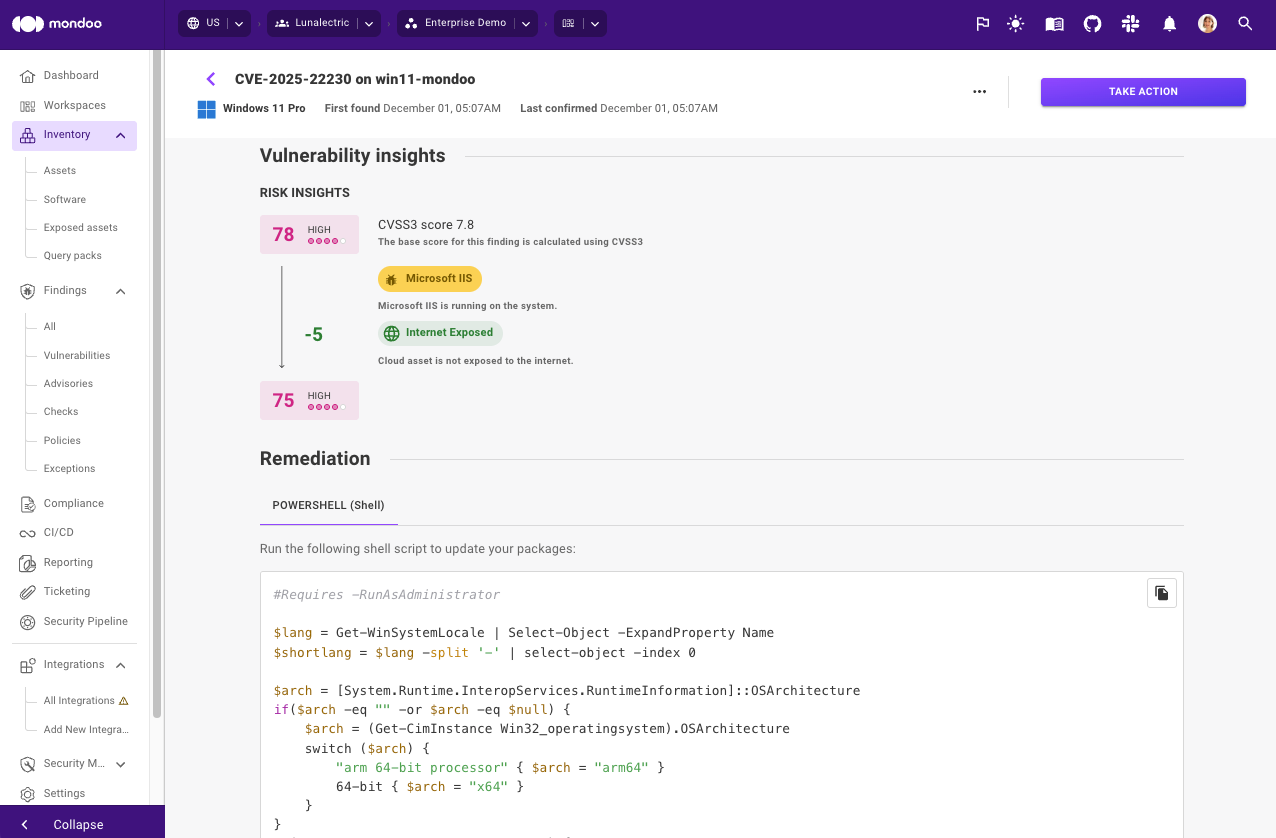
- Get context and guided remediation: Mondoo provides clear remediation guidance for VMware Tools, including the required upgrade steps and supporting scripts where applicable. This removes ambiguity around which version is safe and how the update should be applied.
- Coordinate remediation across teams: Mondoo can create ITSM tickets with full context, including affected machines, remediation steps, and validation criteria. This allows security teams to hand off the issue cleanly to IT operations or virtualisation teams without losing critical details.
Closing the application vulnerability gap
Application vulnerabilities account for a growing share of real-world risk, yet most organisations still lack a clear path from detection to remediation. By expanding coverage for widely used applications and pairing it with guided and automated fixes, Mondoo helps teams reduce risk faster and with less operational overhead.
Stay tuned
Mondoo has some further exciting additions in the works, including our agentic vulnerability patching for third party applications.
Find and fix the security risks that pose the biggest threat to your business.
Problembehebung dreimal schneller mit Mondoo Unified Exposure Management
Learn more about Mondoo
Mondoo eliminates vulnerabilities, not just categorizes them. Global enterprises trust Mondoo to prioritize risks by business impact and exploitability through its patented AI-native security model that collects structured, context-aware data from the entire IT infrastructure. Mondoo’s customers have reduced vulnerabilities and policy violations by 50% and significantly reduced MTTR. With seamless ITSM integrations and transparent security pipelines, Mondoo enables autonomous remediation and continuous compliance. Mondoo bridges the gap between security and engineering, delivering intelligent recommendations and actionable insights to fix the vulnerabilities that matter most to the business.
Want to learn more? Schedule a demo today.









