
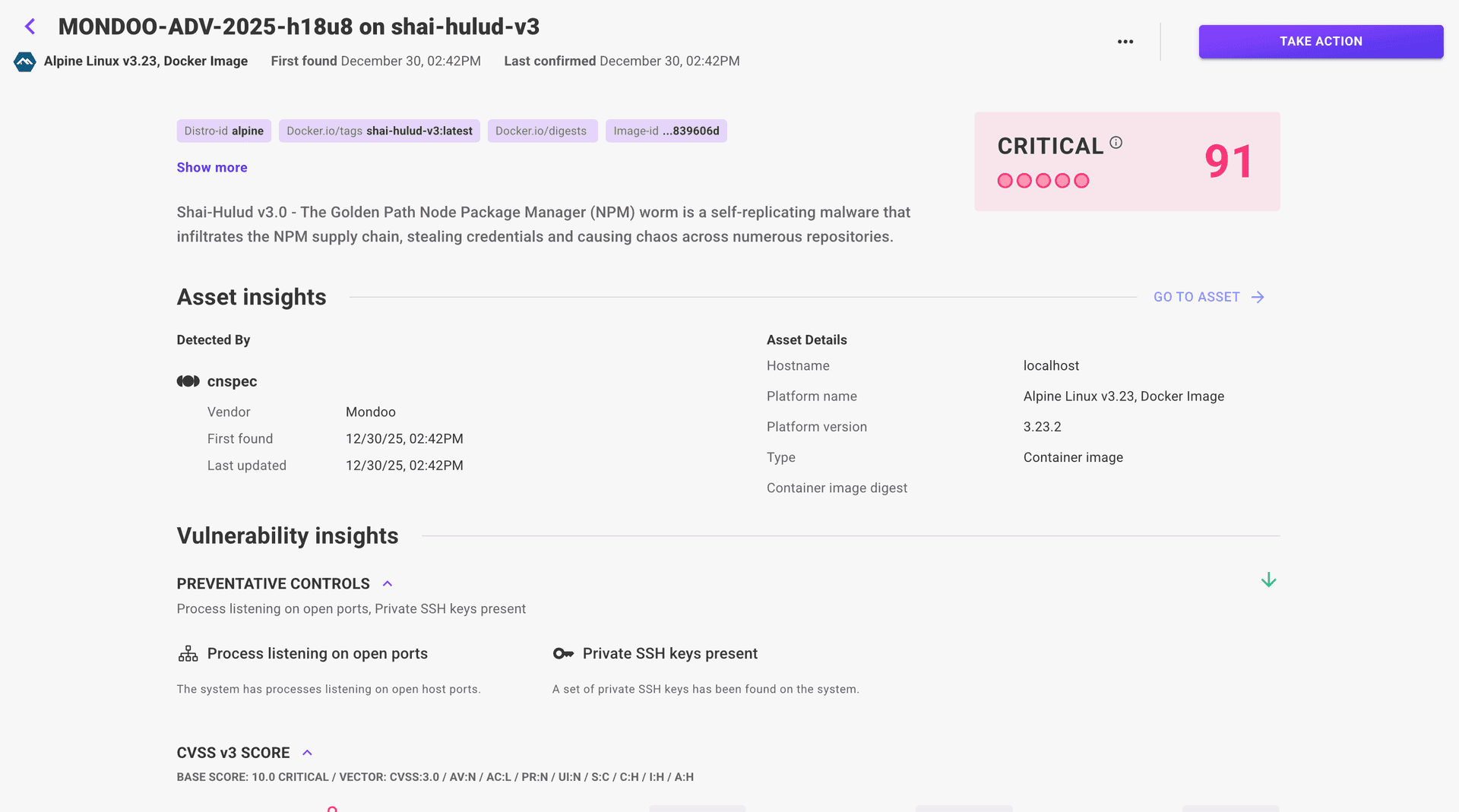
Beyond Shai-Hulud: Why the Era of the Software Supply Chain Worm Has Just Begun
The recent Shai-Hulud NPM attack wasn't just another malicious package, says Patrick Münch, Mondoo's Chief Security Officer. It was a proof-of-concept for a technically elegant and devastating new paradigm of automated, cross-ecosystem warfare targeting developer identity.
Shai-Hulud schlägt zurück, mit v3.0: Die Evolution eines hartnäckigen und gefährlichen NPM-Supply-Chain-Wurms
Patrick Münch, Chief Security Officer bei Mondoo, analysiert die neueste Iteration des Shai-Hulud NPM-Wurms und beschreibt effektive Gegenmaßnahmen.

Shai-Hulud Strikes Back, with v3.0: The Evolution of a Potent and Persistent NPM Supply Chain Worm
Patrick Munch, Mondoo's Chief Security Officer, unpicks the latest iteration of the Shai-Hulud NPM worm and outlines effective mitigation responses.

Shai-Hulud war nur der Anfang: Warum die Ära des Software-Supply-Chain-Wurms gerade erst begonnen hat
Der jüngste Shai-Hulud-NPM-Angriff war nicht nur ein weiteres bösartiges Paket, sagt Patrick Münch, Chief Security Officer bei Mondoo. Es war ein Proof-of-Concept für ein technisch elegantes und verheerendes neues Paradigma automatisierter, ökosystemübergreifender Kriegsführung, die auf die Identität von Entwicklern abzielt.

Application Vulnerabilities: Ready, Steady, Patch
Applications make up a large share of most organizations’ attack surface, yet they remain some of the hardest issues to remediate at scale. A single endpoint can run dozens of applications, each with its own stream of vulnerabilities that quickly compound into meaningful risk. And because even a small flaw can lead to data loss, system compromise, or business disruption, every one of them needs to be tracked and kept current.
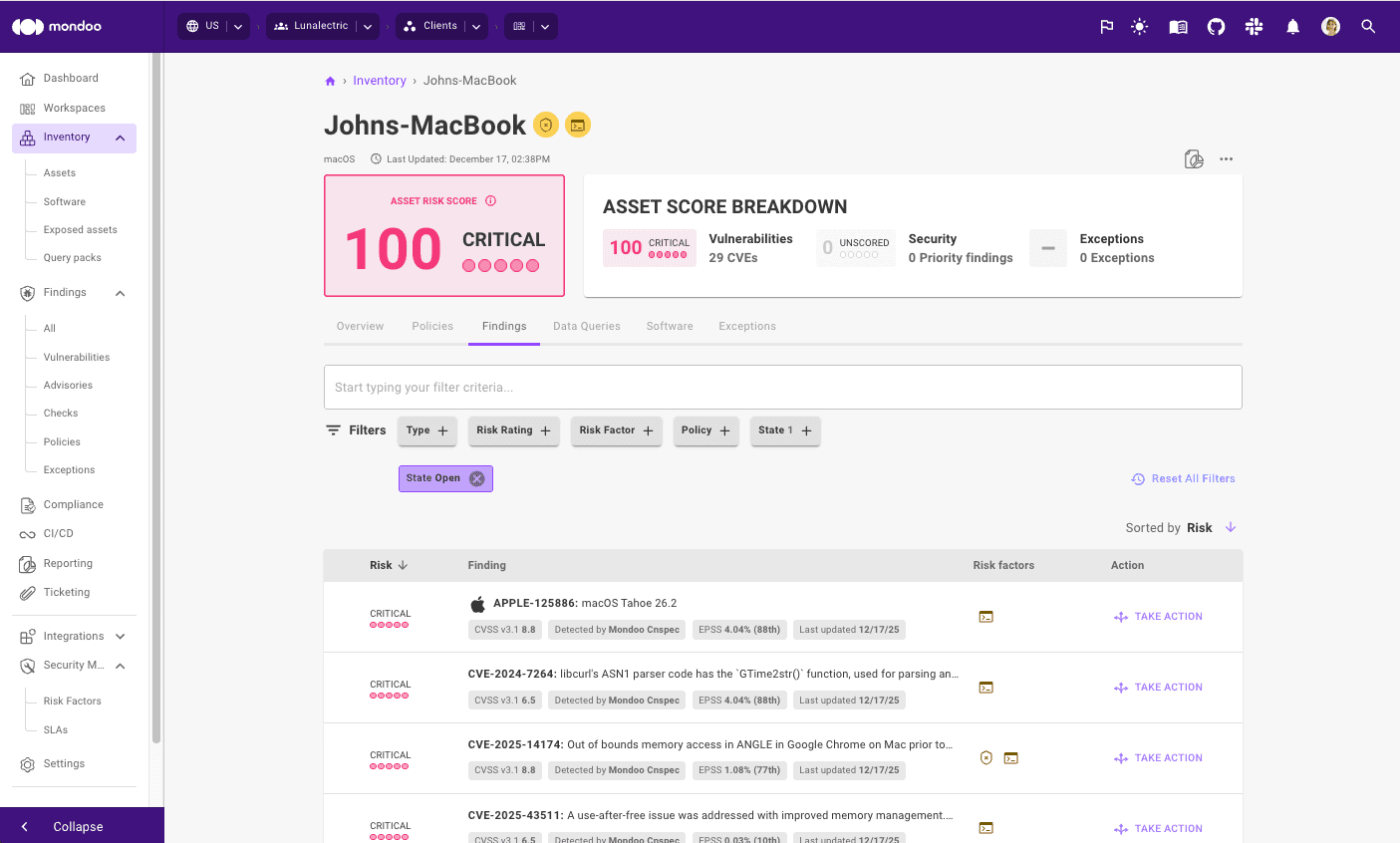
Only 18% Have Updated iOS Despite Active Exploits
Apple has released security patches for two actively exploited WebKit vulnerabilities affecting iPhones, Macs, and iPads. Despite the availability of iOS 26.2, which addresses these flaws, data shows that 82% of iOS systems remain vulnerable because users haven't upgraded.
How to Fix Critical React and Next.js Vulnerabilities (CVE-2025-55182 and CVE-2025-66478)
Two critical, unauthenticated remote code execution (RCE) vulnerabilities were disclosed in the React Server Components (RSC) ‘Flight’ protocol and in Next.js’ use of it, tracked as CVE-2025-55182 (React) and CVE-2025-66478 (Next.js). These flaws are rated critical (CVSS 10.0) and affect default deployments in many projects. Due to the criticality and ease of exploitation, we strongly advise organizations to patch immediately or put mitigating controls in place if patching is not possible yet. Read on to find out if you’re affected and how to fix the issue.

How to Fix 7-Zip Vulnerability with PoC Exploit (CVE-2025-11001)
A newly discovered vulnerability by the Zero Day Initiative affects the widely-used open-source tool 7‑Zip. The vulnerability, CVE‑2025‑11001, is a serious security flaw that is caused by improper handling of symbolic links in ZIP files and can enable arbitrary code execution. To make matters worse, the UK NHS now reports that a security researcher has published a proof of concept exploit, making it more likely that attackers will try to exploit it some time soon.Therefore, immediate patching is advised.
2025 State of Vulnerability Remediation Report: Manual Processes and Low Confidence
Mondoo has released the 2025 State of the Vulnerability Remediation Report, which provides important insights into the current state of remediation processes, pain points and areas for improvement. The report shows that confidence in vulnerability remediation is relatively low, and despite all the advancements in AI, Infrastructure as Code (IaC), and pipeline automation, the majority of vulnerability remediation processes are still manual.

Mondoo Raises $17.5M to Pioneer Agentic Vulnerability Management
In the fast-paced world of cybersecurity, where new vulnerabilities emerge daily and attackers leverage AI to exploit them in hours, staying ahead requires more than just alerts - it demands action. That's why we're thrilled to share that Mondoo has secured $17.5 million in additional funding to accelerate the rollout of the world's first Agentic Vulnerability Management platform. This isn't just about categorizing risks; it's about eliminating them before they can be exploited.

Introducing Agentic Vulnerability Patching Using Ansible
At a time when threat actors are using AI to launch attacks faster than ever, there's a concerning gap between the time when vulnerabilities are detected and when they’re remediated. Also, even after vulnerabilities are fixed, they can often reoccur for various reasons. This leaves organizations at increased risk. Realistically, the only way to reduce this gap is by using more automation in your remediation workflow. However, many organizations are hesitant to deploy automated patching because of fear of breaking systems and giving up control. The solution: a fully transparent system based on tried and tested, easy to use, open source technologies that allow engineers to see exactly what is happening and easily rollback if necessary.
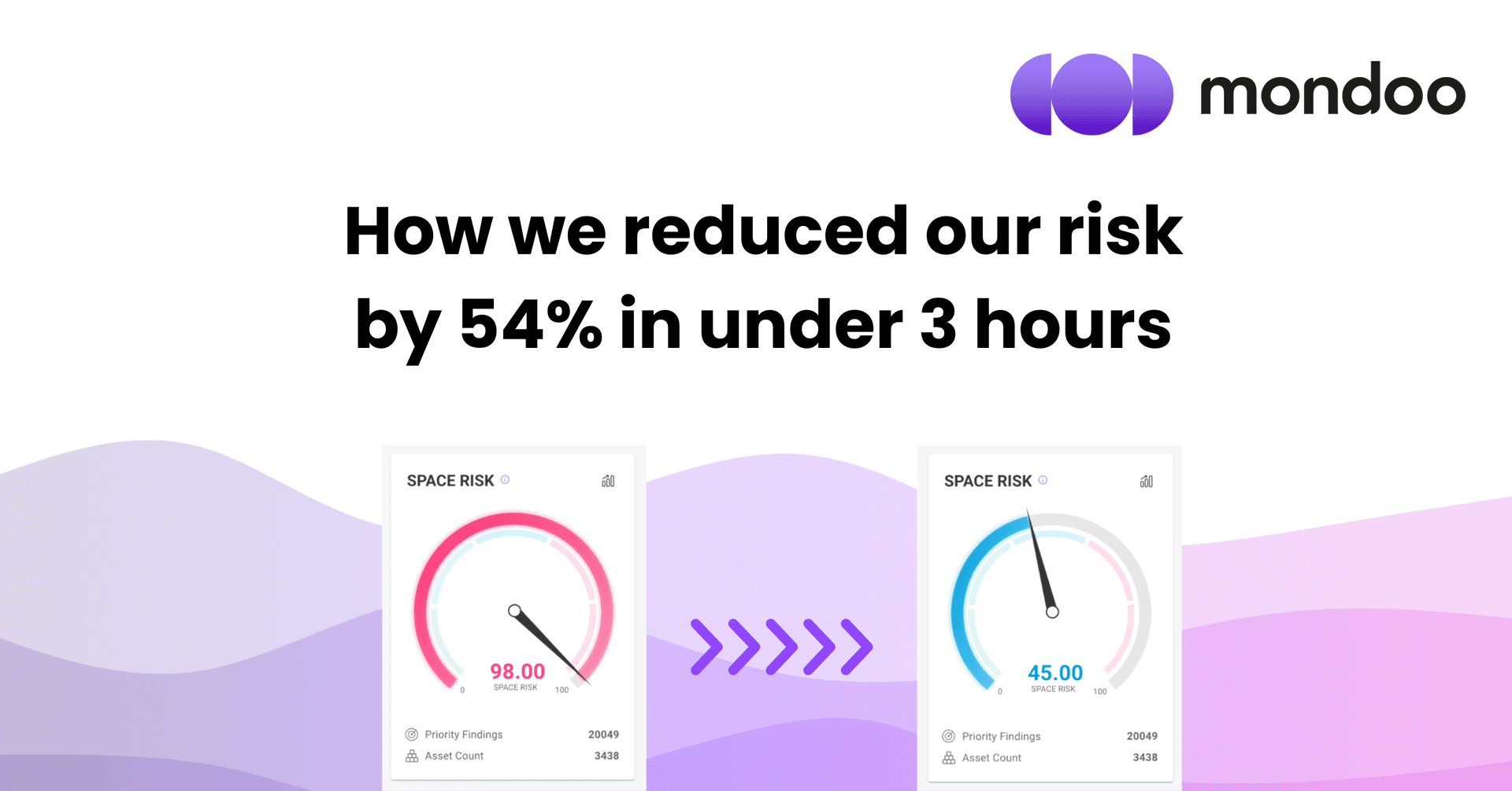
How We Reduced Our Risk By 54% In Under Three Hours
Security teams today are drowning in data. With tens of thousands of findings, the biggest challenge isn't finding problems—it's figuring out which ones to fix first. Prioritizing by generic severity scores or raw asset counts leads to wasted time on low-impact tasks, while the true risks remain. Mondoo’s ‘Move the Needle’ dashboard is designed to solve this. It provides a clear, data-driven path to reducing risk by showing you the exact, quantifiable impact of every action. In this blog, we’ll walk you through a real-world scenario where we were able to reduce our space risk by 54% in under three hours, with the help of Move the Needle and Mondoo’s fast remediation.
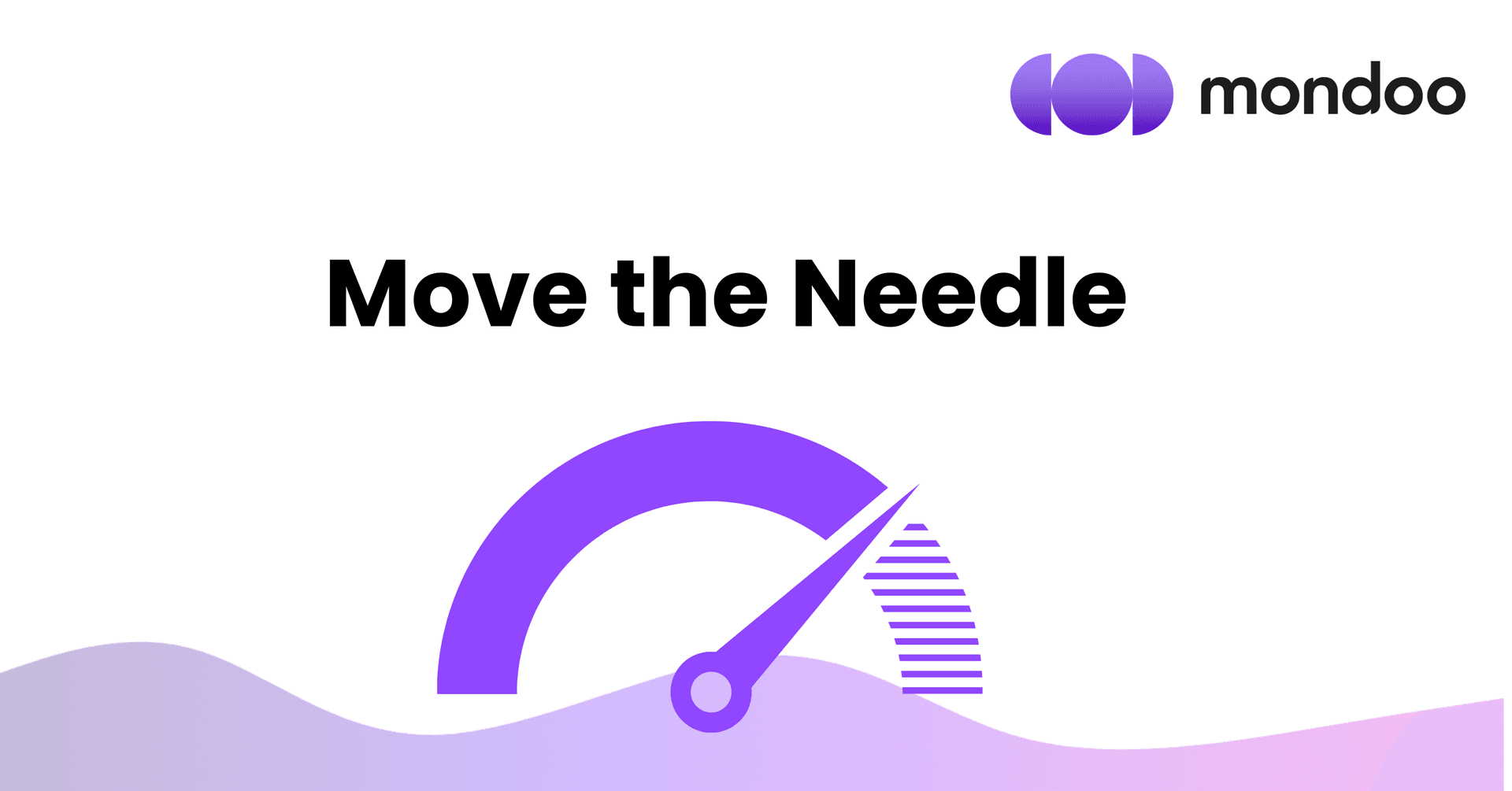
Industry-First Remediation Prioritization that Considers Impact and Effort
Our customers were coming to us with the following problem: “My IT team only has 15 mins per week to dedicate to vulnerability management. How can I make sure that I use those 15 mins to get the biggest improvement in my security posture?” You may be thinking ‘risk-based prioritization’: Remediate the risks that are the most critical, right? Yes, but this goes beyond that. Once your most critical and exposed risks are fixed, you must figure out which remediations will give you the biggest wins: in other words deliver the biggest security improvement for the lowest effort. We’re pleased to share that we’ve just released the ‘Move the Needle’ dashboard, an industry-first solution that calculates all of this for you.
Action Required: Microsoft SharePoint On-prem ToolShell Vulnerabilities (CVE-2025-53770 and CVE-2025-53771)
Over the weekend, more than 50 organizations have already been compromised by attackers exploiting two new CVEs in on-prem Microsoft SharePoint Servers, tracked as CVE-2025-53770 (CVSS 9.8) and CVE-2025-53771 (CVSS 6.3), dubbed 'ToolShell'. Exploitation of these CVEs can result in unauthenticated Remote Code Execution (RCE) and pose significant risk to organizations. It's important to immediately mitigate and patch these critical vulnerabilities since they're already being actively exploited. Read on to understand more about the vulnerabilities, who is affected, and how to quickly remediate.
Sudo Vulnerability CVE-2025-32463: A Case of High Severity Versus Low Risk
Cybersecurity researchers recently disclosed a critical flaw in the sudo command-line utility for Linux and Unix-like operating systems, CVE-2025-32463 (CVSS score 9.3). This critical vulnerability could enable local attackers to escalate their privileges to root. Judging solely by CVSS severity, it needs to be addressed with priority, right? Hold on, not so fast. The CVSS score is just one factor to consider when deciding which vulnerabilities to patch first. In a world where hundreds of CVEs need your attention, and you only have finite resources, it's important to consider severity, risk, and environment when prioritizing. In this blog, we discuss the various risk and contextual factors that must be considered before determining that a vulnerability warrants your focus above others.

Actively Exploited Chromium Zero-Day: CVE-2025-6554 Affects Chrome, Edge, and Opera
Google, Microsoft, and Opera have released emergency security updates to fix a high-severity type confusion vulnerability in Google’s V8 JavaScript engine that affects their browsers. Google’s Threat Analysis Group (TAG) recently discovered and reported the vulnerability, tracked as CVE-2025-6554 with a CVSS score of 8.1. The vulnerability affects all browsers that use the Chromium codebase, and allows a remote attacker to perform arbitrary read/write via a crafted HTML page. What makes this vulnerability especially dangerous is that it’s not only widespread, but actively exploited in the wild — prompting an urgent call to patch all affected browsers.
How Mondoo Helps You Remediate 3x Faster
Got a remediation problem? You’re not alone. Most security platforms are pretty good at detecting vulnerabilities and misconfigurations in your environment, but less are actually able to get you from detection to remediation. This is exactly where Mondoo is different from other platforms. We don’t consider the job done until the issues are actually remediated, and we help security teams and platform engineers get there as fast as possible. Here’s how we do it.

Future Proofing MITRE CVE Troubles
Shockwaves went through the cybersecurity community yesterday, with the announcement by Yosry Barsoum, VP of non-profit research organization MITRE, that U.S. government funding for their Common Vulnerabilities and Exposures (CVE) and Common Weakness Enumeration (CWE) programs was expiring today. Even though disaster was averted by CISA announcing the extension of CVE funding, now is the time to further reflect on how to insulate organizations from these types of occurrences, in order to remain confident in the ability of their security tools to detect vulnerabilities.

Mondoo detects and fixes critical IBM AIX Vulnerabilities: CVE-2024-56346 and CVE-2024-56347
Recently, two critical vulnerabilities were detected in IBM AIX systems that pose significant threats to enterprise environments: CVE-2024-56346 and CVE-2024-56347, with CVSS scores 10 and 9.6. These vulnerabilities enable remote attackers to run arbitrary commands on affected systems without authentication or user interaction, potentially leading to complete system compromise. Since IBM AIX is widely used in enterprise IT environments where high availability and security are essential, the vulnerabilities are especially concerning. In this blog we explain more about the vulnerabilities, how to determine if your systems are affected, and how to remediate them.

Mondoo’s Policy as Code Detects IngressNightmare Vulnerabilities on Kubernetes
A series of critical vulnerabilities in Ingress NGINX Controller for Kubernetes has been uncovered by Wiz research, dubbed "IngressNightmare." This combination of five vulnerabilities (CVE-2025-24513, CVE-2025-1097, CVE-2025-1098, CVE-2025-24514 and CVE-2025-1974) forms a critical attack vector with a CVSS score of 9.8. If left exposed and unpatched, vulnerable environments are at immediate risk of takeover. In this blog, we explain how you can use Mondoo’s open source cnspec to find out if you’re affected by these vulnerabilities so you can mitigate and patch as soon as possible.
Patching Made Easy: Introducing Guided Remediation in Mondoo
We’re thrilled to announce the launch of guided remediation in the Mondoo Platform, which makes patching fast and efficient for your DevOps teams.
How to Find the Backdoored XZ Package at Scale
Find the XZ critical vulnerability CVE-2024-3094 in your environment with Mondoo at scale. The open source tools: cnquery and cnspec. With cnquery's cloud-native asset inventory capabilities, you can detect all instances of the vulnerabilities across your entire infrastructure. Apply the patch to all affected assets and then use cnspec to ensure that no installations with this vulnerability ever go to production again.

Embracing Enhanced Security: CIS IBM AIX 7.1 and 7.2 Benchmarks
Mondoo now extends its cutting-edge security solutions to IBM AIX platforms! This marks a significant milestone in our journey towards empowering enterprises to fortify their most critical workloads with confidence. While the cloud and Kubernetes have become the go-to for many, the reality is that numerous enterprises still rely heavily on classic infrastructures for their pivotal business operations. This enhancement is more than just an upgrade; it's our commitment to ensuring that your entire inventory, spanning from the cloud to on-premises systems, remains shielded against the ever-evolving landscape of cyber threats. Welcome to a new era of comprehensive, unwavering security for your IBM AIX environments! 🛡️🚀

Securing Infrastructure Layers: A Comprehensive Approach
In today's complex IT landscape, ensuring robust security across infrastructure layers is a daunting task. Organizations often rely on various tools to monitor and safeguard their on-premises systems, cloud-based applications, and everything in between. This approach, however, has proven to be more burdensome than helpful. In this blog, we'll explore the limitations of this fragmented approach and how Mondoo is changing the game with a comprehensive, full-stack security solution.

From Report-Driven to Data-Driven Security
The current landscape of corporate security and compliance is heavily report-driven. What does this mean? Simply put, security scans are performed on an organization's IT infrastructure, and a report is generated outlining potential vulnerabilities and compliance issues. But there's a crucial piece of the puzzle missing: the raw data.

CIS SecureSuite Certified for GitHub and Supply Chain Security
Mondoo is the first full-stack Security Vendor to receive Center for Internet Security (CIS) certification for GitHub. This significant accomplishment also means that Mondoo is the first security vendor to provide coverage for the entire supply chain, from repositories via Infrastructure as Code (IaC) to runtime. That means Mondoo can protect the entire infrastructure stack like all major Clouds (AWS, GCP, Azure), Kubernetes (AKS, EKS, GKE, OpenShift, Tanzu), including workloads, Windows, Linux, macOS, VMware, Terraform, etc.

CISO Guide: Key Steps to Robust Security Posture
In the face of escalating cybersecurity threats and a rapidly changing regulatory environment, a Chief Information Security Officer (CISO) must build a robust security posture. This requires a clear understanding of various critical factors. Let's delve into these essential elements and explore how they contribute to fortifying your organization's defenses.

Addressing CVE-2023-32434: Continuous Security for Apple's Kernel
Apple's recent kernel vulnerability, CVE-2023-32434, poses a serious threat to macOS, iOS, and iPadOS systems, highlighting the importance of cybersecurity in the digital age. Prompt installation of the provided kernel update is crucial to mitigate potential exploits, emphasizing the ongoing need for vigilance and proactive security measures in the face of evolving cyber threats.

Fix Critical Word RTF Font Table Heap Bug CVE-2023-21716: Open Source Solution
Microsoft Word is an essential tool used by individuals and businesses globally. However, it has recently been discovered that Microsoft Word is susceptible to a critical vulnerability known as RTF Font Table Heap Corruption, which can allow attackers to execute arbitrary commands with the victim's privileges via malicious RTF files.

Understanding the Differences Between xSPM and CSPM: Which Solution is Right for Your Organization?
In today's digital landscape, organizations need to ensure the security and compliance of their entire infrastructure, including on-premises, cloud-native applications, and SaaS services. Two solutions that have emerged to address this need are extensible security posture management (xSPM) and cloud security posture management (CSPM). Both xSPM and CSPM help organizations assess, improve, and maintain their security posture, but they approach this task in slightly different ways. In this article, we will explore the key differences between xSPM and CSPM and help you determine which solution is the best fit for your organization.

Maximizing Security with xSPM: Separation of Powers
Separation of powers in infrastructure security is crucial to reducing the risk of a single point of failure or vulnerability. This is achieved by assigning different aspects of the infrastructure, such as availability, scalability, and security to different teams or individuals.

Securing Your Infrastructure: A Guide to Extensible Security Posture Management (xSPM)
Are you looking to improve your organization's security posture? Look no further than extensible security posture management (xSPM).

A Complete Guide to Easy VMWare Patch Management
Patch management is the process of distributing and applying updates to software, crucial for security, compliance, and system uptime. Mondoo offers a solution to identify missing patches and facilitate their deployment across your infrastructure, ensuring a robust security posture.
Critical Linux Vulnerability (ZDI-22-1690, ZDI-CAN-17816): Find and Fix with cnquery
The Zero Day Initiative issued on 22 December 2022 a new critical Linux Kernel vulnerability ZDI-22-1690.

Agent-Based or Agentless Cloud Security Scanning
Have you ever asked a group of security or operations engineers which is better: agent-based or agentless vulnerability scanning? You might as well ask whether pineapple belongs on pizza or what’s the best Linux distro. It’s a topic that inspires strong opinions, and our community doesn’t seem to grow tired of the debate.

How to Fix the PrintNightmare (CVE-2021-34527 / KB5004948) Vulnerability
This article lets you walk in a hacker's shoes. It provides step-by-step instructions for using the known PrintNightmare vulnerability to gain unpermitted access to a Windows system. It also shows you how to keep attackers from exploiting this and other vulnerabilities to steal, destroy, or ransom your business-critical data.

Should Your Infrastructure Security Shift Left or Right?
A darling of conference talks, videos, and articles, shift left security has generated some excitement in the IT community. Industry analysts claim that shift left is the future. Evangelists tell you that this change can save resources and better protect your infrastructure. And what about shift right? The shift right movement might not have as much traction, but opponents of shift left are speaking out and making their case. What do these terms really mean? What drives the strong opinions about each? And should your infrastructure security shift left, shift right, or stay right where it is?

High OpenSSL Vulnerabilities (CVE-2022-3602 & CVE-2022-3786): Find, Fix, and Enforce Through Open Source
Find the OpenSSL high vulnerabilities (CVE-2022-3602 and CVE-2022-3786) in your environment with Mondoo's new open source tools: cnquery and cnspec. With cnquery's cloud-native asset inventory capabilities, you can detect all instances of the vulnerabilities across your entire infrastructure. Apply the patch to all affected assets and then use cnspec to ensure that no installations with this vulnerability ever go to production again.

How to Handle a Ransomware Incident
A ransomware incident stresses an IT organization to its very limits and brings a company to its knees. After the initial panic, there are steps you can take to resolve the situation as quickly as possible, avoid escalating the conflict, and prevent future successful infrastructure breaches.
What in the World Is a CNAPP (and Do I Need One)?
You’ve heard your CISO talking about CNAPPs (along with CSPM, CWPP, and so on). What is a CNAPP, and what does it mean to you as a security engineer?

Exposing What's Under the Hood of Ransomware Attacks
Ransomware is devastating to a company because it damages critical data. During an attack, ransomware scans for important files, encrypts them, and destroys backups. This can cripple an organization faster than other malicious applications. In this second part of a blog series about ransomware, we’ll discuss well-known cybercriminals and the harm they do.

CVEs: Close the Gaps That Let in Attackers
IT organizations are making cybercrime too easy. Projects like the National Vulnerability Database and Common Vulnerabilities and Exposures (CVE) warn about the doorways that hackers use to penetrate infrastructure. Software providers rush to provide patches for their vulnerable products. However, most IT teams don’t patch their systems when they learn about a problem.
Preventing Ransomware Attacks: Hacker Procedure (Part 1)
Ransomware attackers often follow very similar patterns or sequences when they ransom an organization’s IT infrastructure. Only those who know the attack patterns can effectively protect themselves against them. In this first part of a blog series about ransomware, we’ll explore typical approaches to holding IT operations hostage.

5 Reasons Why Cloud Security Policy Fails
In the past year, devastating cloud security breaches have dominated technology headlines. These big news stories are only the tip of the iceberg in cybercrime—we don’t hear about the thousands of successful attacks that cripple worldwide businesses every day.

Exploit and Detect Dirty Pipe Vulnerability - CVE-2022-0847
The Dirty Pipe vulnerability in Linux Kernel 5.8 or higher allows attackers to modify files, potentially gaining root access and compromising systems, including Android smartphones. Mondoo provides a query to detect affected systems and offers a comprehensive security solution to identify and assess vulnerabilities across various environments.
Ready to Transform Your Security?
See how Mondoo can help you find and fix vulnerabilities faster.