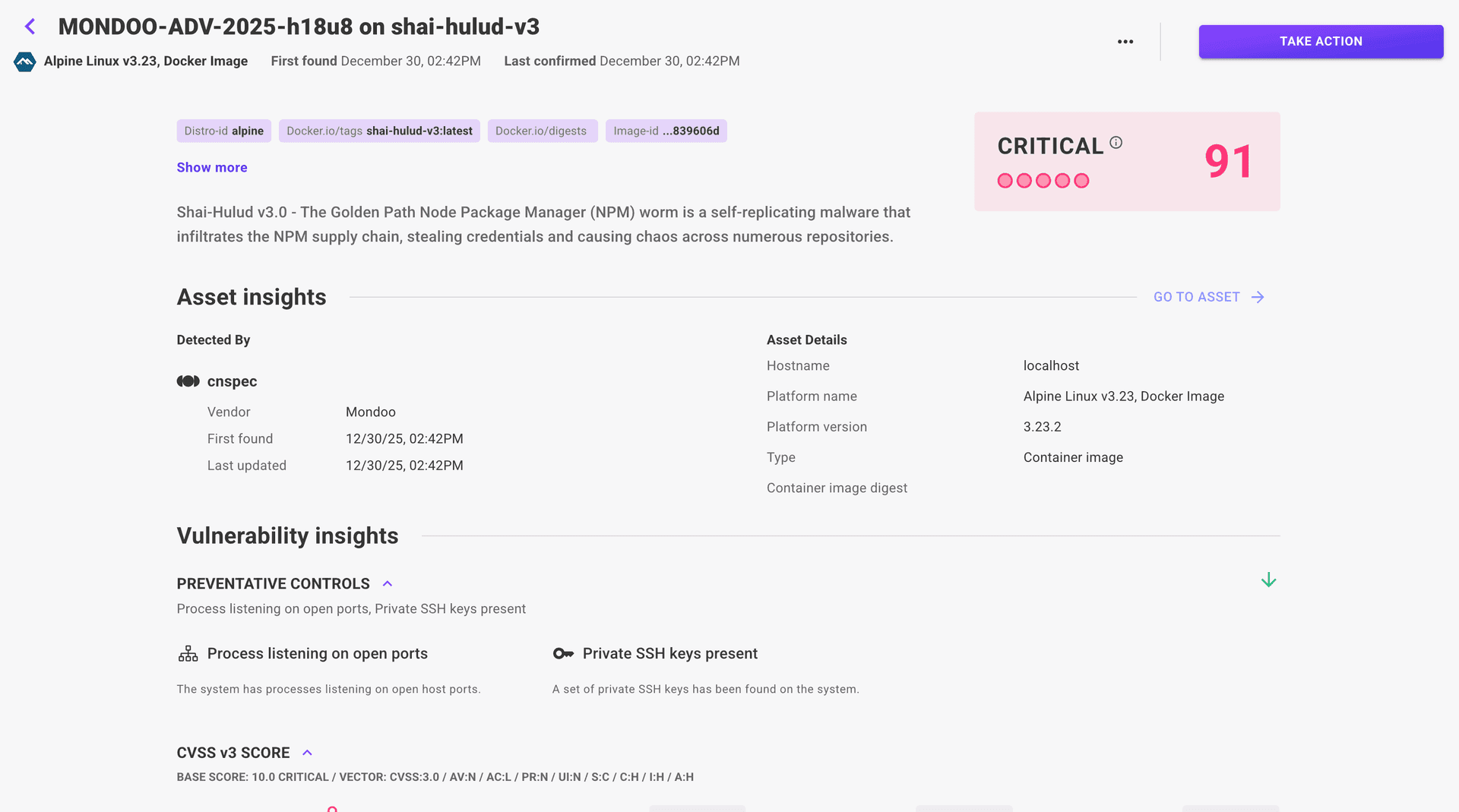
Die digitalen Dünen haben sich erneut verschoben und signalisieren die Rückkehr einer der hartnäckigsten Bedrohungen im npm-Ökosystem: dem Shai-Hulud-Wurm. Diese neue Variante, die als „Shai-Hulud 3.0" bezeichnet wird, wurde kürzlich bei der Verbreitung über ein schädliches Paket, @vietmoney/react-big-calendar@0.26.2, entdeckt – jedoch mit heimlicheren und widerstandsfähigeren Fähigkeiten. Wer dies als nur ein weiteres zu patchendes, anfälliges Softwarepaket abtut, handelt auf eigene Gefahr.
Während das Kernziel gleich bleibt – das Stehlen sensibler Daten aus Entwickler- und CI/CD-Umgebungen – zeigt die neueste Evolution das Engagement der Angreifer für eine längere Lebensdauer und größere Reichweite, was robuste Software-Supply-Chain-Sicherheit wichtiger denn je macht.
Wichtige Neuerungen im neuen Wurm
Die Analyse von Shai-Hulud 3.0 zeigt eine Reihe technischer Weiterentwicklungen, die auf verbesserte Zuverlässigkeit und Erkenungsvermeidung abzielen:
- Verbesserte Verschleierung: Die neue Variante verfügt über eine verstärkte Code-Verschleierung, die statische Analyse und manuelle Code-Reviews erschwert. Der Bedrohungsakteur scheint Zugang zum ursprünglichen Quellcode zu haben, was auf eine kontinuierliche, gut ausgestattete Kampagne hindeutet.
- Höhere Zuverlässigkeit: Die Malware hat ihre Fehlerbehandlung verbessert, insbesondere für das Secrets-Harvesting-Tool TruffleHog, sodass Timeouts nun eleganter ablaufen. Entscheidend ist, dass sie nun explizit Windows-Umgebungen unterstützt, indem sie die Plattform prüft und bun.exe aufruft, was die potenzielle Angriffsfläche verbreitert.
- Der Totmannschalter ist verschwunden: Im Gegensatz zu früheren Versionen, die eine Funktion zum Stoppen des Angriffs enthielten, scheint diese Variante den „Totmannschalter" entfernt zu haben, was auf einen Wunsch nach anhaltender, fortlaufender Exfiltration hindeutet. Dies ist eine wahllose „Fire and Forget"-Waffe ohne Möglichkeit, den Angriff abzubrechen.
- Neue Artefakte und Metadaten: Die Malware verwendet aktualisierte Dateinamen für ihre Payload (bun_installer.js und environment_source.js) und exfiltrierte Daten (3nvir0nm3nt.json, cl0vd.json, c9nt3nts.json). Sie verwendet auch die markante GitHub-Repository-Beschreibung „Goldox-T3chs: Only Happy Girl" für ihre Command-and-Control-Infrastruktur.
Wie der Angriff funktioniert
Der Angriffsvektor bleibt eine klassische und hocheffektive Supply-Chain-Taktik:
-
Ausführung bei der Installation: Das schädliche Paket enthält ein preinstall-Skript in seiner package.json. Dieses Skript wird automatisch bei der Installation in einer NPM-Umgebung ausgeführt, was es zu einer „Zero-Click"-Bedrohung macht, die ausgelöst wird, bevor Entwickler oder automatisierte Scanner eingreifen können.
-
Payload-Ausführung: Das Skript startet bun_installer.js, das dann die primäre Payload, environment_source.js, lädt.
-
Secrets-Harvesting: Die Hauptfunktion der Payload besteht darin, TruffleHog zu verwenden, um das lokale System nach wertvollen Geheimnissen zu durchsuchen, darunter:
- API-Tokens (z.B. npm-Tokens)
- Cloud-Zugangsdaten
- CI/CD-Secrets
Die gesammelten Geheimnisse werden auf die Festplatte geschrieben und dann an die vom Angreifer kontrollierte GitHub-Infrastruktur exfiltriert.
![]()
Empfehlungen zur Risikominderung: Härtung Ihrer Software Supply Chain
Reaktive Maßnahmen sind nicht ausreichend und fast immer zu spät, um einen bedeutenden Unterschied zu machen. Organisationen müssen proaktive Kontrollen implementieren, um ihre Umgebung gegen diesen und zukünftige Supply-Chain-Angriffe zu schützen. Sofort zu ergreifende Maßnahmen sind:
- Prüfen und Entfernen: Überprüfen Sie Ihre Umgebungen sofort auf das Paket @vietmoney/react-big-calendar@0.26.2 und entfernen Sie es aus allen Projekten.
- Zugangsdaten rotieren: Gehen Sie davon aus, dass jede Umgebung, die das Paket installiert hat, kompromittiert ist. Rotieren Sie alle Secrets und Zugangsdaten, die von diesen betroffenen Build-, Entwickler- oder CI/CD-Systemen zugänglich waren (Cloud, Git, npm usw.).
- Artefakte prüfen: Überwachen Sie Repositories und Systeme auf das Vorhandensein der neuen exfiltrierten Datenartefakte wie 3nvir0nm3nt.json oder c9nt3nts.json.
Mondoo hilft Ihnen beim Aufbau langfristiger Verteidigungsmaßnahmen
Mondoo überprüft Ihre gesamte Infrastruktur auf Kompromittierungsindikatoren, die mit dieser Bedrohung zusammenhängen. Durch die Integration der in den Quellen gefundenen IoCs (Indicators of Compromise) in einen Scanning-Workflow können Sie Ihre Umgebung absichern:
-
Infrastrukturweite Prüfung: Mondoo scannt Ihre gesamte Infrastruktur, einschließlich virtueller Maschinen, Container und Cloud-Umgebungen, um Dateien zu erkennen, die von Shai Hulud v3.0 verwendet werden, wie bun_installer.js oder 3nvir0nm3nt.json.
-
Konfigurationsdurchsetzung: Mondoo prüft Ihre Entwicklungsumgebungen, um sicherzustellen, dass ignore-scripts korrekt auf true gesetzt ist. Dies blockiert die postinstall- und preinstall-Hooks, die die primären Infektionsvektoren für diese Variante sind.
-
Secrets-Management und Sicherheitslage: Stellen Sie sicher, dass Secrets nicht in Umgebungen oder Quellcode offengelegt werden. Mondoos tiefgreifende Scanning-Fähigkeiten helfen dabei, Ihre CI/CD-Pipelines, Container-Images und Infrastructure-as-Code kontinuierlich auf hartcodierte oder falsch konfigurierte Secrets zu prüfen und so die potenzielle Beute für jeden Wurm zu begrenzen, der Ihre Verteidigung durchbricht.
Die Evolution von Shai-Hulud ist eine deutliche Erinnerung daran, dass die Software Supply Chain weiterhin ein primäres Ziel bleibt. Wir erwarten einen Anstieg ähnlicher, wirkungsvoller Angriffe über mehrere Software-Entwicklungs-Ökosysteme hinweg.
Durch die Einführung eines kontinuierlichen Security Posture Management-Ansatzes können Organisationen von reaktivem Patchen zu proaktiver Verteidigung übergehen und den Sandwurm effektiv zähmen, bevor er den goldenen Pfad zu Ihren Geheimnissen durchbricht.
Bereit, Mondoo in Aktion zu sehen?
Vereinbaren Sie eine Demo noch heute.