Assess Google Workspace Security with cnspec
Set up cnspec to perform security scans of Google Workspace
Rely on cnspec to ensure your Google Workspace environment follows security best practices, such as enforcing strong passwords, verifying 2-step verification enrollment, auditing admin roles, reviewing third-party app tokens, and checking user account status across your organization.
Before you begin
Be sure you have:
- cnspec installed
- Super administrator access to Google Workspace Admin Console
- Administrator access to Google Cloud Console
Create a Google Cloud service account
These steps for configuring Admin SDK API access to your Google Workspace environment rely on Google Cloud (GCP) even if you aren't otherwise using GCP.
Step A: Create a Google Cloud Project
-
Go to Google Cloud and sign in as a super administrator. If it's your first time signing into the console, agree to the terms of service.
-
From the Google Cloud menu, select IAM & Admin > Manage Resources.
-
At the top, select Create Project and enter a project name (such as Mondoo Security Scan).
If you want, you can add the project to a folder: For Location, select Browse, navigate to the folder, and choose Select.
-
Select Create.
Step B: Enable the required APIs to scan Google Workspace
-
From the Google Cloud menu, select APIs & Services > Library.
-
For each of these APIs, select the API name and then select Enable:
- Admin SDK
- Google Calendar API
- Contacts API
- Gmail API
- Groups Migration API
- Cloud Identity API
- Google Drive API
If you don't see the API you need, type its name in the search box.
Step C: Set up the OAuth consent screen
-
From the Google Cloud menu, select APIs & Services > OAuth consent screen.
-
For User Type, select Internal.
-
Select Create.
-
For App name, enter "Mondoo Security Scanner" or another name that makes sense for your organization.
-
For Authorized Domains, select + ADD DOMAIN and enter your domain configured in Google Workspace.
-
Select a User support email for users to contact with questions.
-
For Developer contact information, enter email addresses so Google can contact you about changes to your project.
-
Select Save and Continue > Save and then select Continue > Back to Dashboard.
Step D: Create the service account
-
From the Google Cloud menu, select APIs & Services > Credentials.
-
Select Create Credentials > Service account.
-
For Service account name, enter "mondoo-security-scanner" or another name that makes sense for your organization.
If you want, you can also add a Service account description.
-
Select Create and select Continue.
-
Select Done > Save.
-
At the top, select Key > Add Key > Create new key.
-
Make sure the key type is set to JSON, then select Create. You see a message that the service account's private key JSON file was downloaded to your computer. Note the file name and where your browser saves it. You need it for later steps.
-
Select Close.
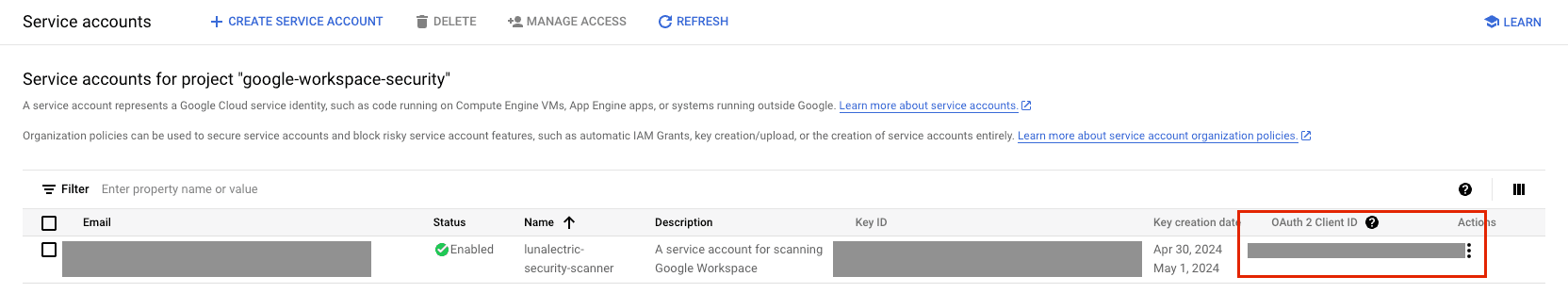
-
Record the OAuth 2 / Client ID from the list of service accounts. You need that for the next step.
Configure domain-wide delegation in Google Workspace Admin Console
In this next section you configure domain-wide delegation in Google Workspace Admin console to give your new service account the access it needs to the Google Workspace APIs.
-
Log into the Google Workspace Admin Console.
-
In the left-side navigation, select Security > Access and data control > API controls.
-
Select Domain-wide Delegation and then select Add new.
-
For the Client ID, enter the client ID you recorded in Step D above.
-
For OAuth Scopes, paste this comma-delimited list to add all required OAuth scopes:
https://www.googleapis.com/auth/admin.chrome.printers.readonly,https://www.googleapis.com/auth/admin.directory.customer.readonly,https://www.googleapis.com/auth/admin.directory.device.chromeos.readonly,https://www.googleapis.com/auth/admin.directory.device.mobile.readonly,https://www.googleapis.com/auth/admin.directory.domain.readonly,https://www.googleapis.com/auth/admin.directory.group.member.readonly,https://www.googleapis.com/auth/admin.directory.group.readonly,https://www.googleapis.com/auth/admin.directory.orgunit.readonly,https://www.googleapis.com/auth/admin.directory.resource.calendar.readonly,https://www.googleapis.com/auth/admin.directory.rolemanagement.readonly,https://www.googleapis.com/auth/admin.directory.user.alias.readonly,https://www.googleapis.com/auth/admin.directory.user.readonly,https://www.googleapis.com/auth/admin.directory.userschema.readonly,https://www.googleapis.com/auth/admin.reports.audit.readonly,https://www.googleapis.com/auth/admin.reports.usage.readonly,https://www.googleapis.com/auth/admin.directory.user.security,https://www.googleapis.com/auth/cloud-identity.groups.readonly,https://www.googleapis.com/auth/calendar.readonly,https://www.googleapis.com/auth/calendar,https://www.googleapis.com/auth/calendar.events,https://www.googleapis.com/auth/calendar.events.readonly,https://www.googleapis.com/auth/calendar.settings.readonly -
Select Authorize.
Super admin role email
To use your Google Cloud service account with domain-wide delegation, you must specify a super admin role email to impersonate when authenticating to the API.
In the Google Workspace Admin Console, navigate to Account > Admin Roles and select Super Admins. Record the email address for the Super Admin you want to use when authenticating.
To learn more about super admin roles, read Prebuilt administrator roles in the Google Workspace documentation.
Record your Google Workspace customer ID
Navigate to Account > Account Settings and record the Customer ID. You need the customer ID to configure hosted scanning in Mondoo Platform, or to use locally with cnspec or cnquery.

Connect cnspec to Google Workspace
To test your configuration, open a cnspec shell and verify the connection:
cnspec shell google-workspace --customer-id YOUR_CUSTOMER_ID --impersonated-user-email admin@domain.com --credentials-path /path/to/credentials.jsoncnspec> googleworkspace.users { primaryEmail }
googleworkspace.users: [
0: { primaryEmail: "alice@example.com" }
1: { primaryEmail: "bob@example.com" }
]| For... | Substitute... |
|---|---|
--customer-id | The customer ID you recorded above |
--impersonated-user-email | The email address of a user that has super admin privileges |
--credentials-path | The path to the downloaded JSON credentials file |
To scan your Google Workspace environment:
cnspec scan google-workspace --customer-id YOUR_CUSTOMER_ID --impersonated-user-email admin@domain.com --credentials-path /path/to/credentials.jsonInstead of --credentials-path, you can set any of these environment variables (listed in order of precedence): GOOGLE_APPLICATION_CREDENTIALS, GOOGLEWORKSPACE_CREDENTIALS, GOOGLEWORKSPACE_CLOUD_KEYFILE_JSON, or GOOGLE_CREDENTIALS.
Understand scan output
When a scan completes, cnspec prints a summary of all the checks it ran, grouped by policy. Each check shows a pass or fail result. For example:
✓ Pass: Ensure all users are enrolled in 2-step verification
✕ Fail: Ensure no suspended users exist
✓ Pass: Ensure all domains are verifiedAt the end of the output, cnspec shows a risk score from 0 (no risk) to 100 (highest risk). Failed checks include remediation guidance to help you fix issues.
By default, cnspec applies the Mondoo Google Workspace Security policy, which covers password strength, 2-step verification, admin roles, third-party app tokens, and more. You can also create your own policies or specify a particular policy bundle with --policy-bundle.
Example checks
Run cnspec shell google-workspace (with the required flags above) to open the cnspec interactive shell. From there you can make checks like the examples below.
Ensure all users have strong, compliant passwords
googleworkspace.users {
usageReport.account {
_['passwordStrength'] == "STRONG"
_['passwordLengthCompliance'] == "COMPLIANT"
}
}Ensure all users are enrolled in 2-step verification
googleworkspace.users { isEnrolledIn2Sv == true }List users and their admin status
googleworkspace.users { primaryEmail isAdmin lastLoginTime }Ensure no suspended users exist
googleworkspace.users.where( suspended == true ) { primaryEmail suspensionReason }Ensure all domains are verified
googleworkspace.domains { domainName verified == true }Ensure 2-step verification is enforced (not just enrolled)
googleworkspace.users { primaryEmail isEnforcedIn2Sv == true }Continuously scan your fleet
To move beyond one-off scans, set up a Google Workspace integration in Mondoo Platform. You get continuous monitoring across your Google Workspace environment, a dashboard to track security posture over time, and integration with ticketing systems to manage remediation.
Learn more
-
To learn more about how the MQL query language works, read Write Effective MQL.
-
To learn more about the information Mondoo can retrieve from Google Workspace, explore the complete Mondoo Google Workspace Resource Pack Reference.