Scan Using AWS Systems Manager
Configure AWS Systems Manager (SSM) to scan EC2 instances for security misconfigurations without installing agents.
Use AWS Systems Manager (SSM) to securely scan EC2 instances. You don't need to deploy cnspec to instances in your environment. Any time Mondoo scans an instance, it automatically installs cnspec for the duration of the scan and then uninstalls cnspec when the scan finishes.
How Mondoo scans with SSM
When Mondoo performs an SSM scan, these steps occur:
- SSM Run Command calls the AWS-RunShellScript SSM document.
- The latest version of cnspec is installed and configured to authenticate with your Mondoo Platform account.
- The EC2 instance runs
cnspec scanto execute policy checks. - cnspec publishes results of the scan to Mondoo Platform.
- cnspec is uninstalled from the EC2 instance.
Configuring AWS SSM
This section covers a new setup of AWS SSM to manage EC2 instances in AWS. If you are brand new to AWS SSM, read the AWS documentation for additional implementation details.
Create an IAM role and instance profile for SSM
Before you can manage EC2 instances using SSM you need to perform these steps either in the AWS Console or the AWS CLI:
- Set up an IAM Role with a trust policy for EC2.
- Attach the AWS managed AmazonSSMManagedInstanceCore policy to the IAM role.
- Create an instance profile (if you're using the AWS CLI).
- Attach the IAM role to the instance profile (if you're using the AWS CLI).
Select your preferred method for configuring SSM, and follow the steps.
Requirements
- AWS console access to any account you plan to integrate with Mondoo
- Administrator privileges in those accounts
Create an IAM role for EC2 instances with AmazonSSMManagedInstanceCore policy
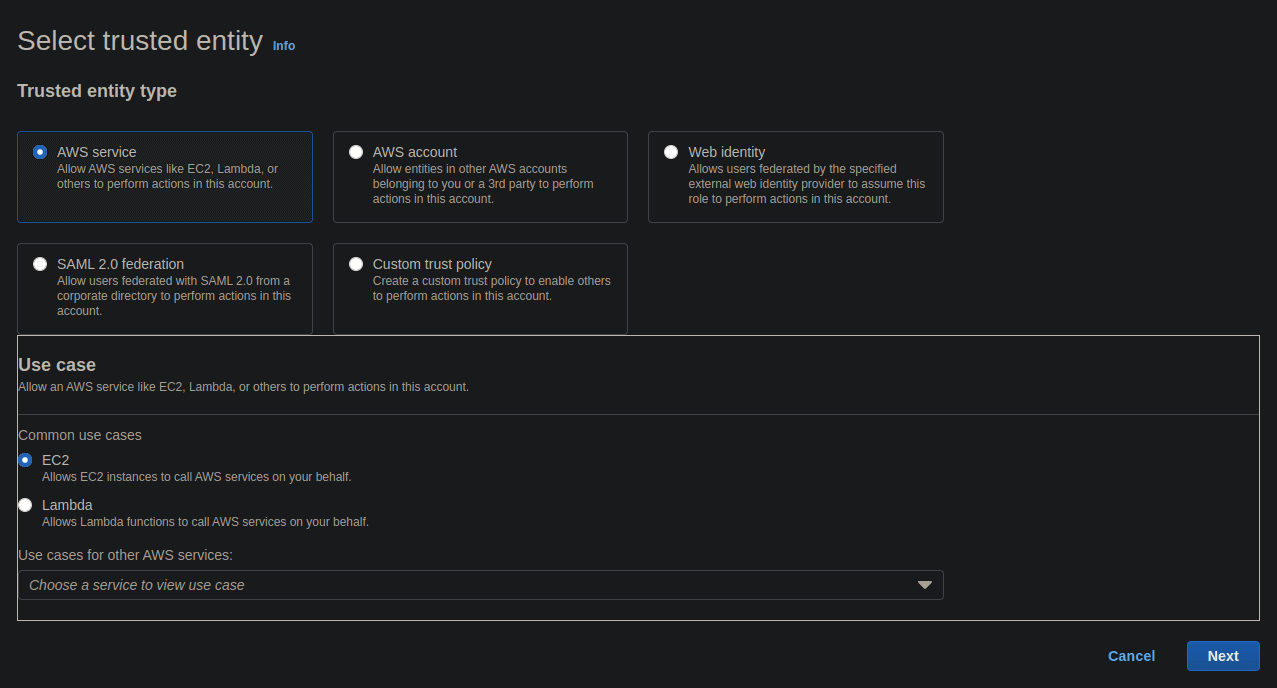
- Log in to the AWS Console.
- Navigate to IAM.
- Select Roles.
- Select Create Role.
- For the Trust entity type, select AWS service and for the Use case, select EC2. Then select the Next button.
- Search for SSM in the Filter policies box, select AmazonSSMManagedInstanceCore, and then select the Next button.
- Under Role details, give the role a name (such as EC2_SSM_ROLE), tags, and a description (if you want), and then select Create role.
Your new role is ready for use and can be attached to existing EC2 instances, or to new EC2 instances as an instance profile when launching new instances.
Launch a new EC2 instance with the newly created instance profile
Follow the steps below to launch a new EC2 instance using the AWS console, attach the SSM role created in the last section, and then validate the instance is under management in the AWS SSM console.
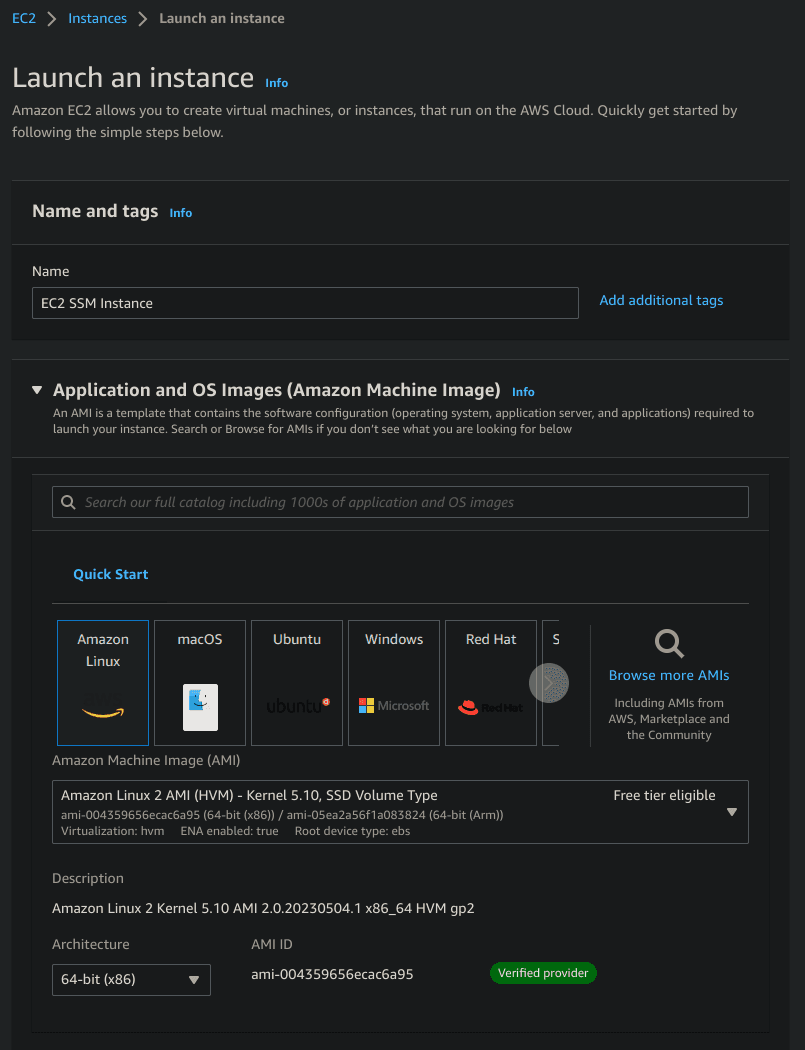
- Log in to the AWS Console.
- Navigate to EC2.
- Select Launch Instance.
- Under Name and tags, in the Name field, enter EC2 SSM Instance.
- Under Application and OS Images (Amazon Machine Image), select Amazon Linux 2 AMI (HVM), SSD Volume Type, which defaults to 64-bit (x86).
- Under Instance type select t2.micro.
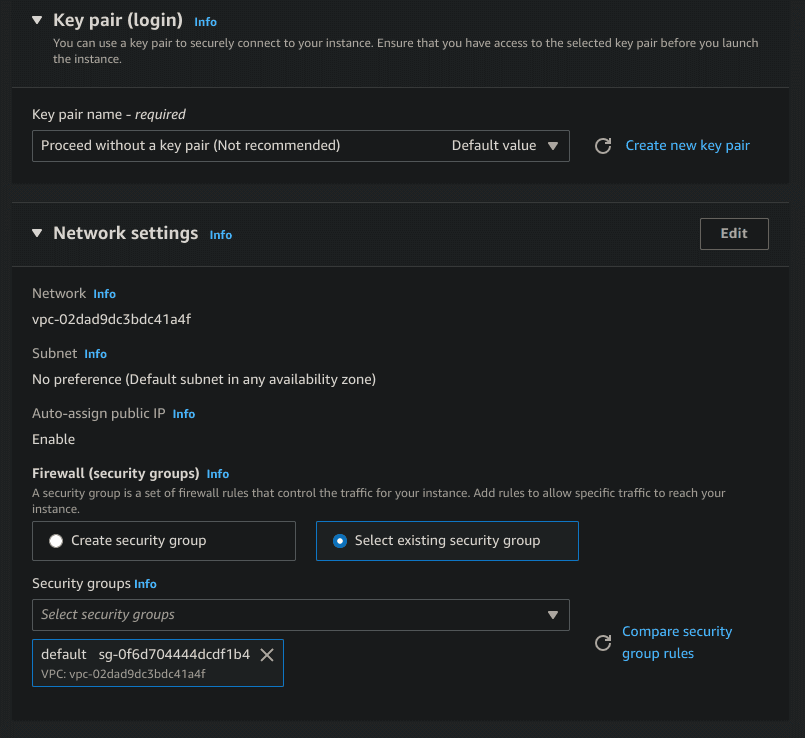
- Under Key pair (login), you can either add or create a new key pair, but in this instance it's safe to select Proceed without a key pair (Not recommended). If you want remote access to the instance, you can add an SSH key. This is not required.
- Under Network settings - Firewall(security groups), select Select existing security group and choose the default security group.
- Open the block Advanced details and under IAM instance profile, select the role you created in the instructions above.
- Review the details then select Launch.
- Copy the instance ID. You need it in the next steps.
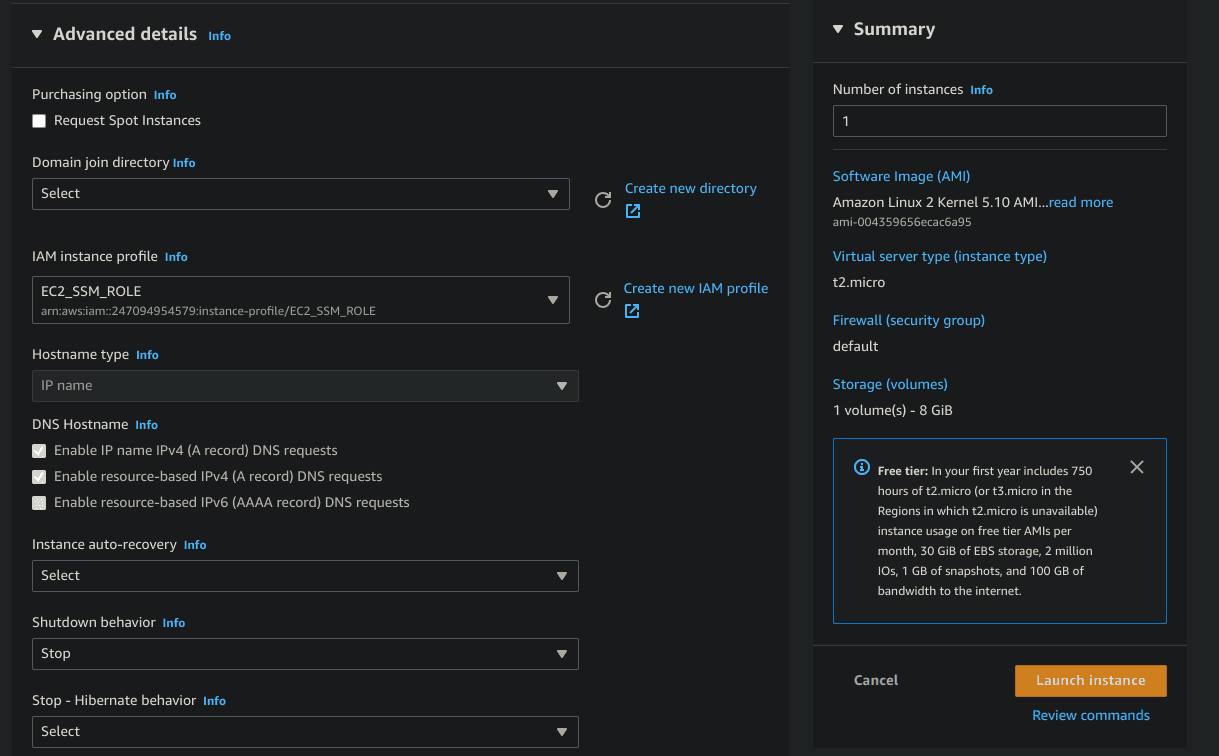
Validate that the instance is under management of AWS Systems Manager
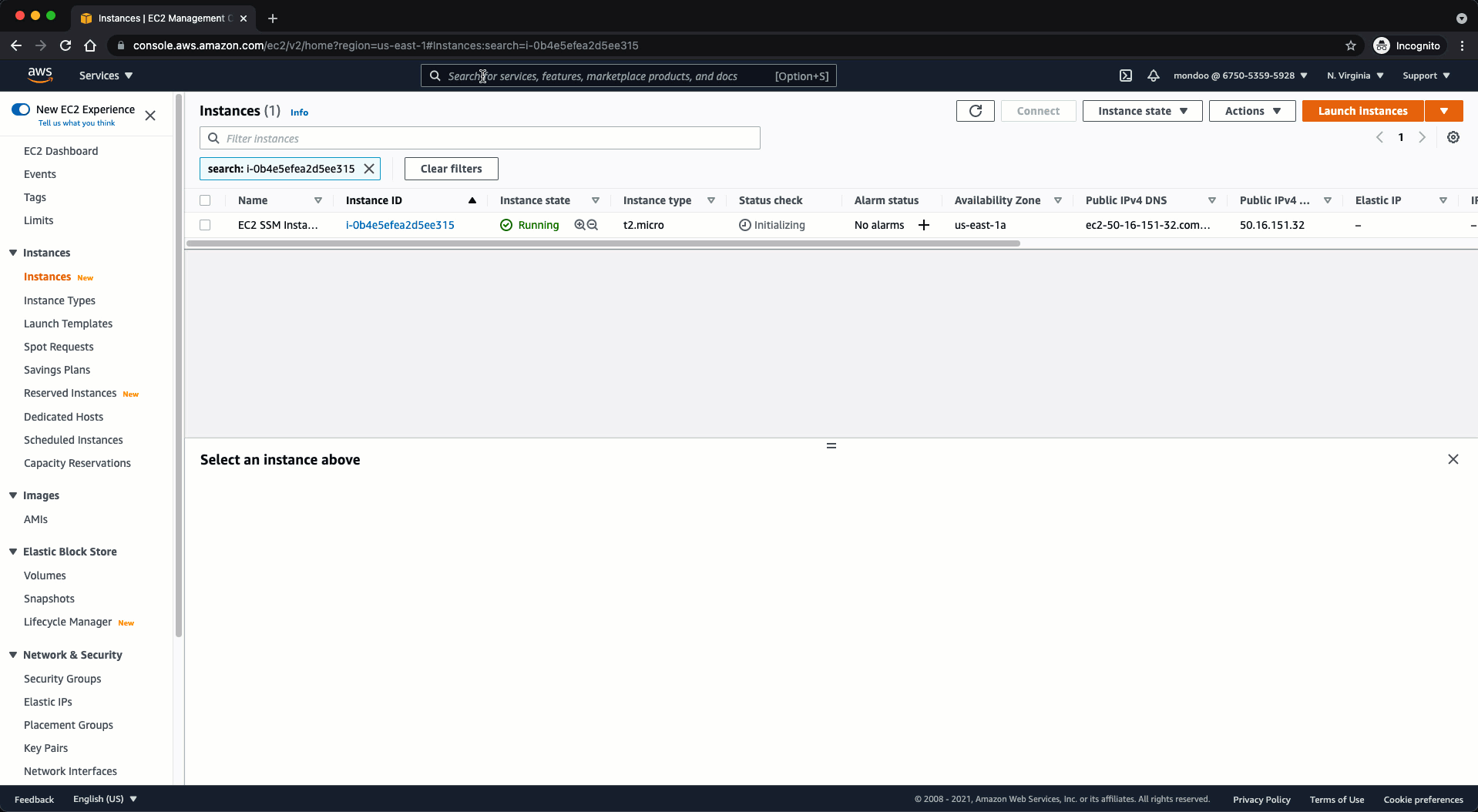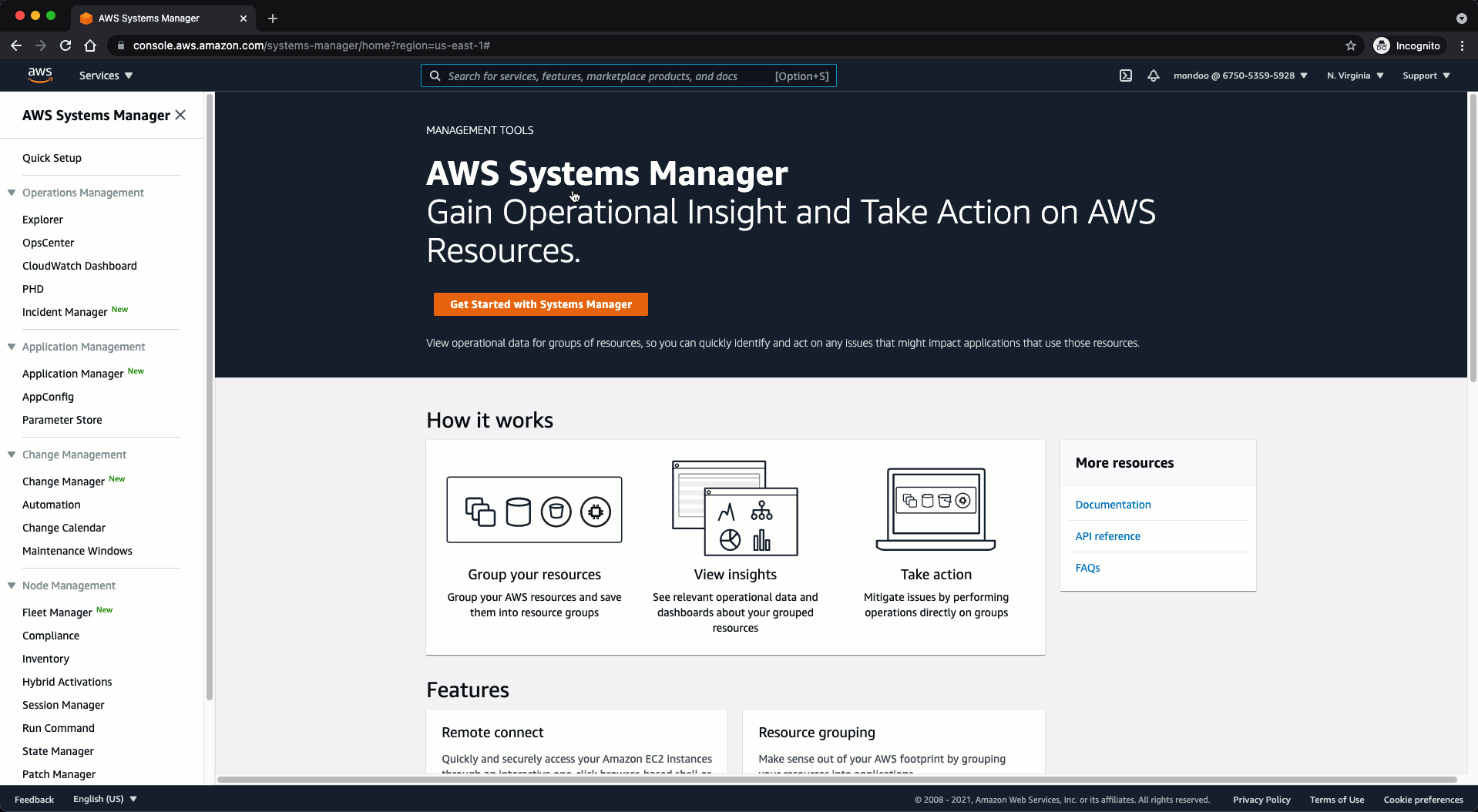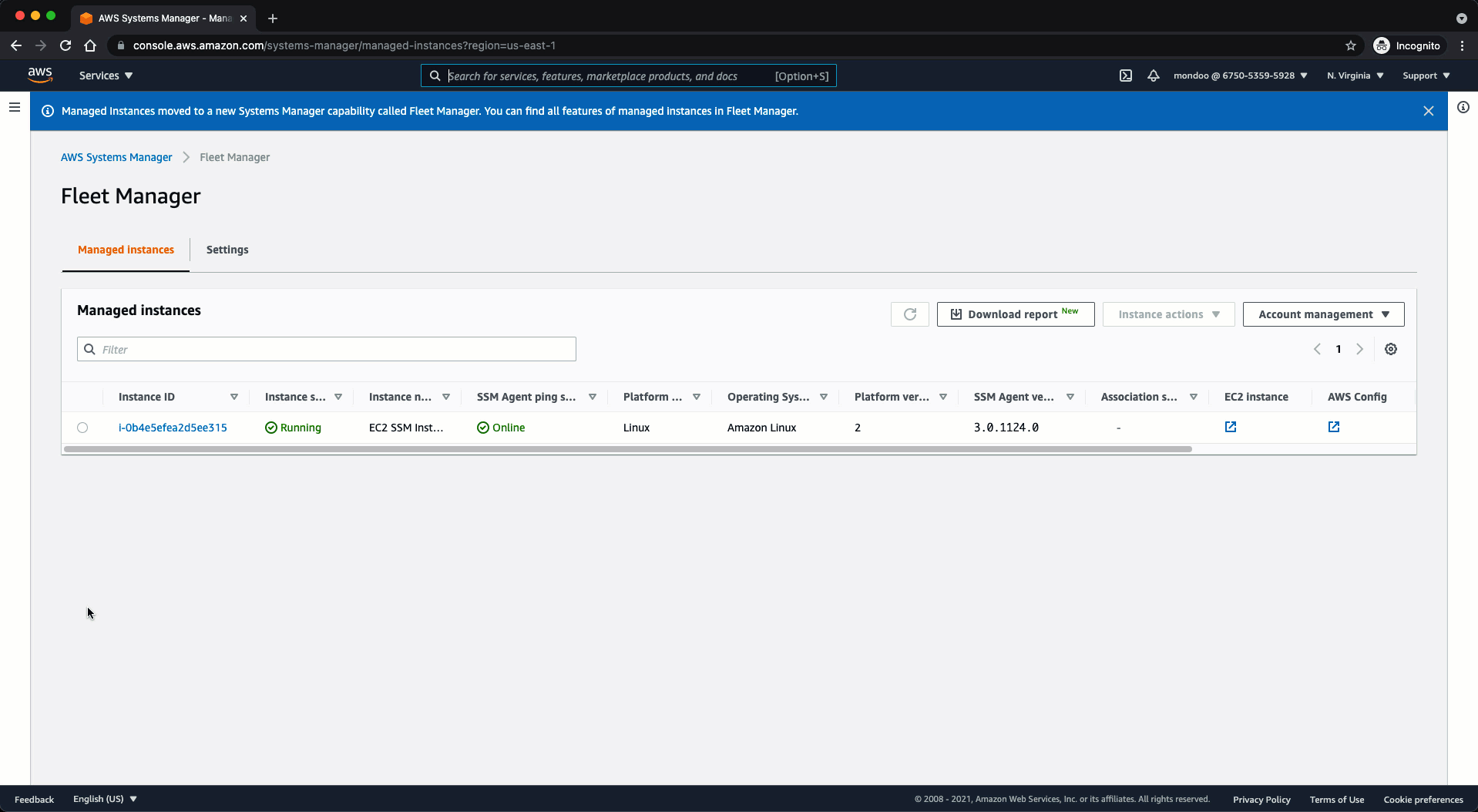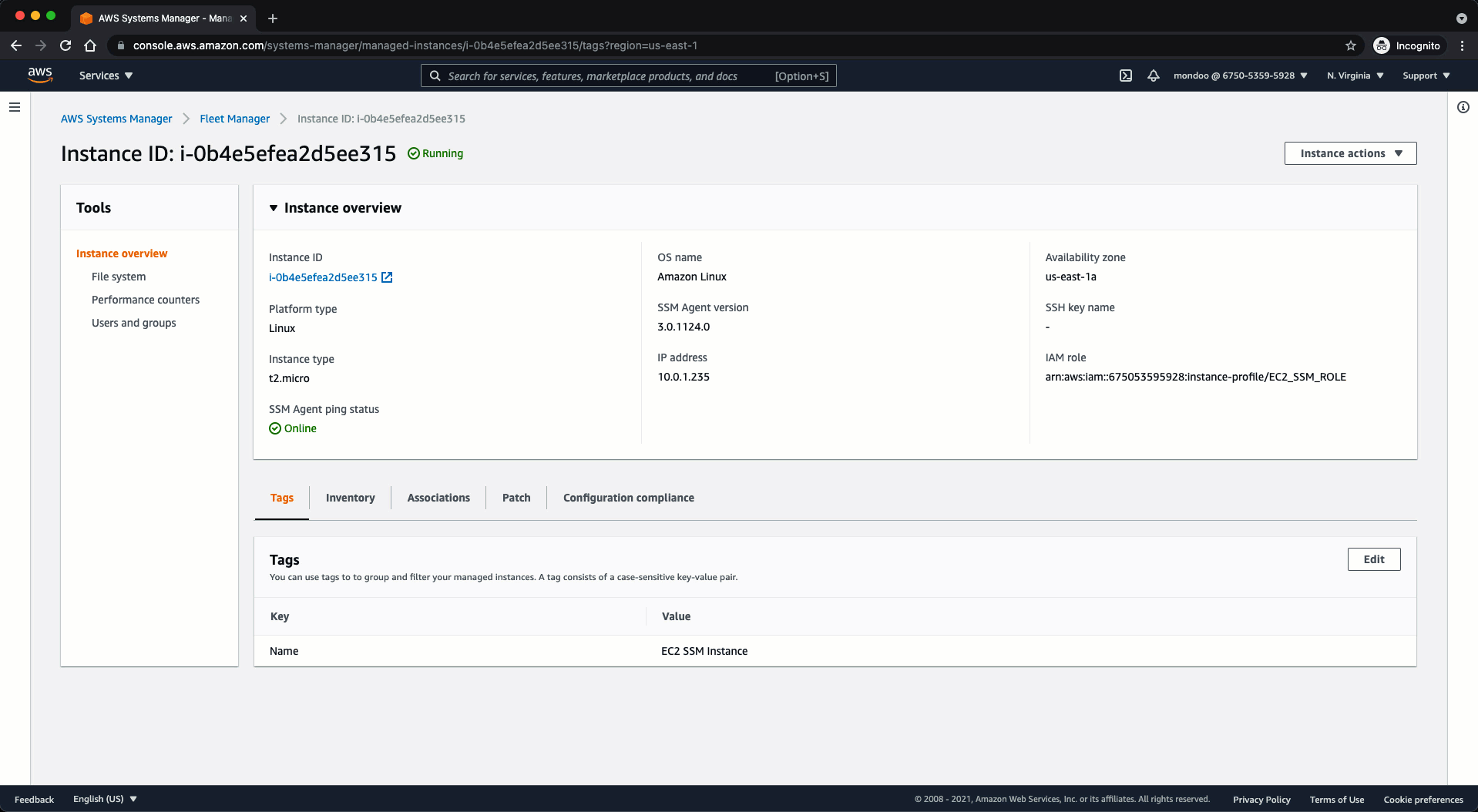
To validate that the EC2 instance is under the management of SSM:
- Log in to the AWS console.
- Navigate to Systems Manager.
- Select Fleet Manager.
- Locate the instance ID of the instance you launched in the section above and select it to bring up the Instance Overview.
This confirms the instance is under the management of SSM. Mondoo can use it to perform continuous scans of the asset.
Requirements
- You must have the AWS CLI installed and configured for your account.
- You must be a part of the Administrators group.
Get the ARN of the SSM policy for the IAM role AmazonSSMManagedInstanceCore
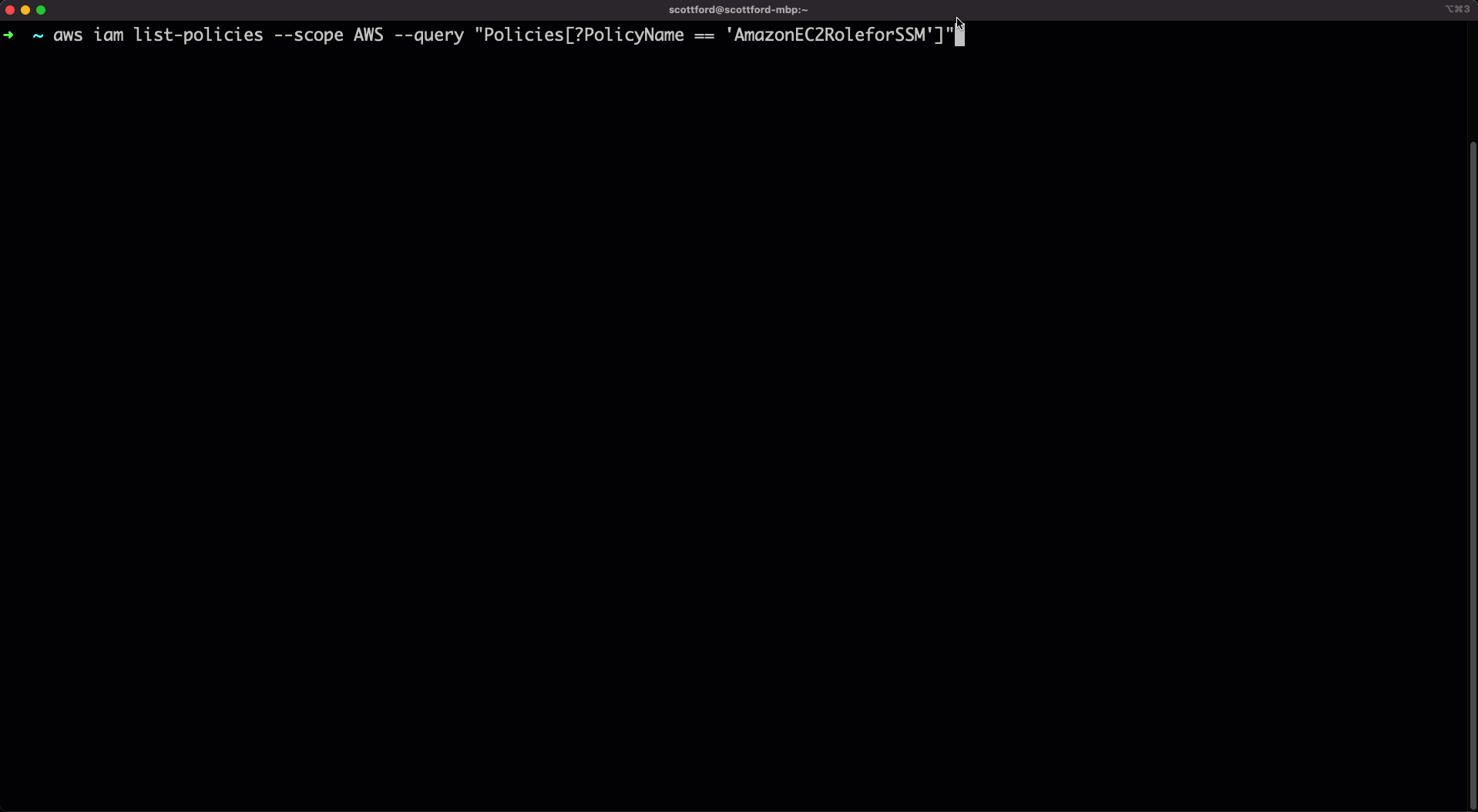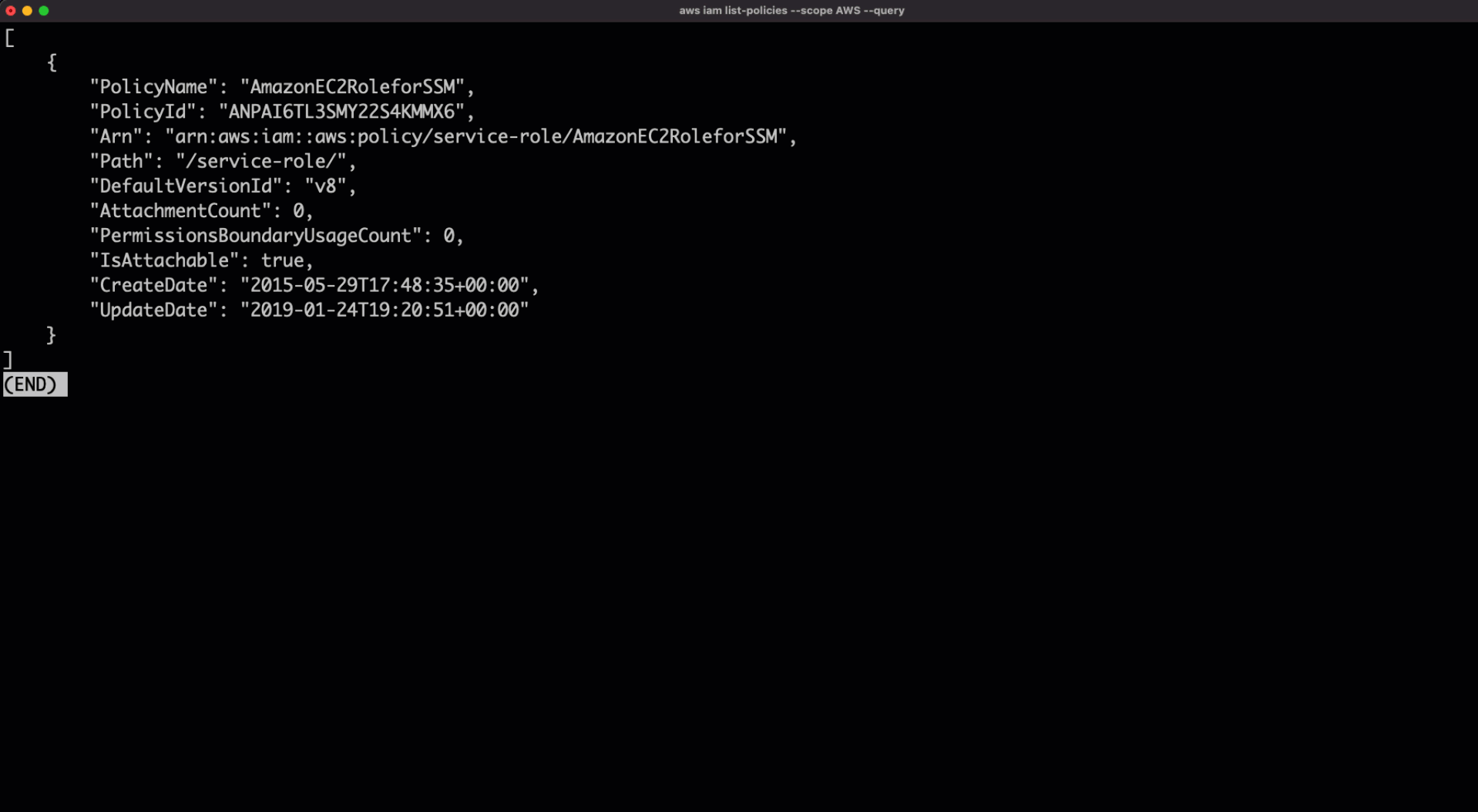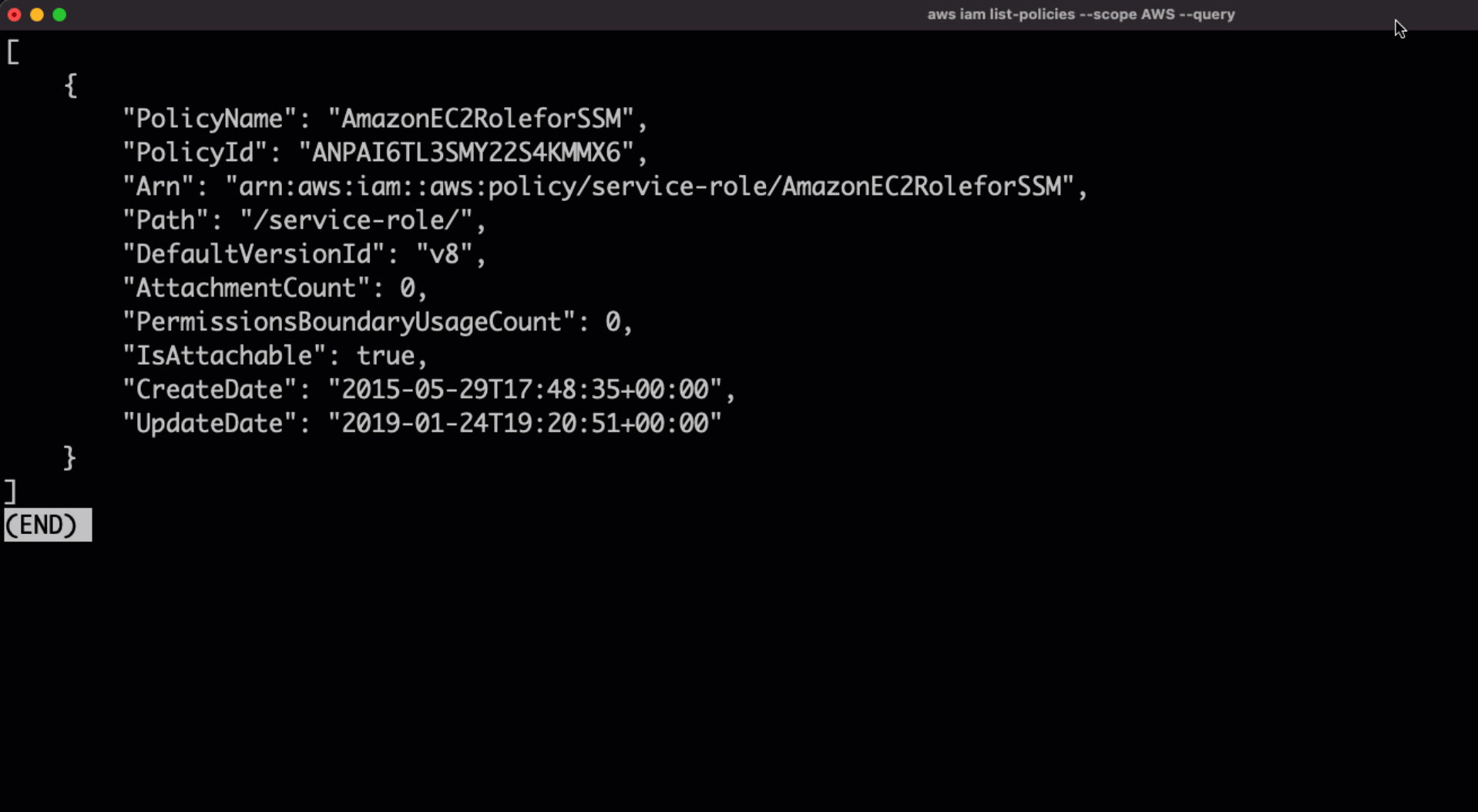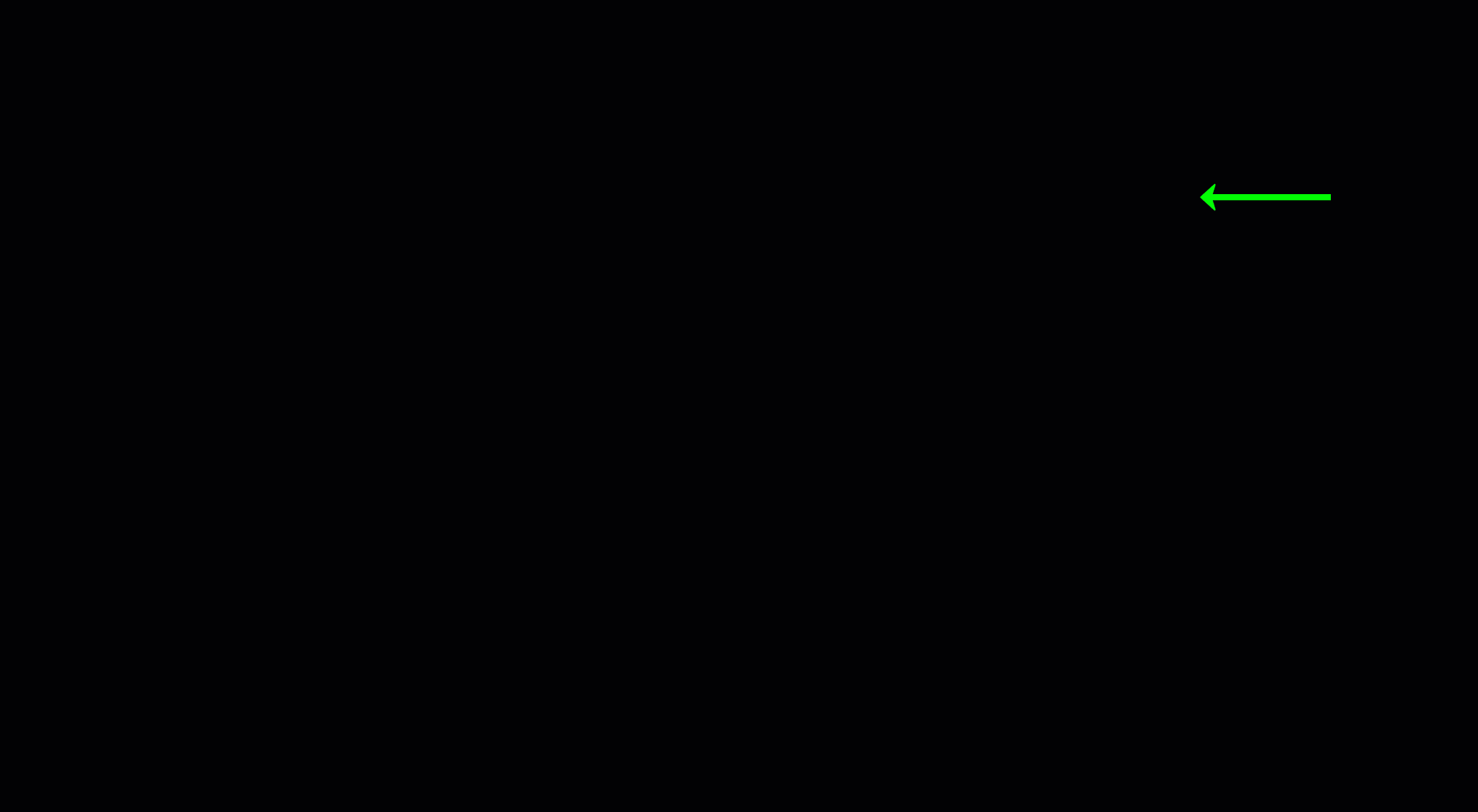
aws iam list-policies --scope AWS --query "Policies[?PolicyName == 'AmazonSSMManagedInstanceCore']"Create an AssumeRole policy
- Create a new file named
ec2-trust.json. - Copy this code snippet:
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Principal": { "Service": "ec2.amazonaws.com" },
"Action": "sts:AssumeRole"
}
}- Paste the code snippet into the
ec2-trust.jsonfile. - Save the file.
Create IAM SSM role and attach the role policy document
aws iam create-role --role-name EC2_SSM_ROLE --assume-role-policy-document file://ec2-trust.jsonaws iam attach-role-policy --role-name EC2_SSM_ROLE --policy-arn <SSM-POLICY-ARN>Launch an Amazon Linux 2 EC2 instance with the instance profile
With the instance profile you created, you can now launch EC2 instances that are configured for use with AWS SSM.
Not all AMIs have the SSM agent installed by default. For a complete list of AMIs that come with SSM agent pre-installed, read About SSM Agent in the AWS documentation.
Follow these steps to launch an Amazon Linux 2 EC2 instance in a default VPC using the new instance profile in the previous step:
- Get the subnet ID:
aws ec2 describe-subnets --query "Subnets[?Tags[?Value == 'SubnetA'] ].SubnetId | [0]"- Get the security group ID:
aws ec2 describe-security-groups \
--filters Name=group-name,Values=SG \
--query "SecurityGroups[?GroupName == 'SG'].GroupId | [0]"- Get the Amazon Linux 2 AMI ID (SSM agent preinstalled)
aws ec2 describe-images \
--filters "Name=architecture,Values=x86_64" "Name=description,Values=*Amazon Linux 2 AMI 2.0.2019*gp2" "Name=owner-id,Values=137112412989" "Name=image-type,Values=machine" \
--query "sort_by(Images, &CreationDate)[::-1].ImageId | [0]"- Launch a new EC2 instance with the EC2_SSM_ROLE:
aws ec2 run-instances --associate-public-ip-address \
--security-group-ids <SECURITY-GROUP-ID> \
--iam-instance-profile Arn=<INSTANCE-PROFILE-ARN> \
--instance-type t2.micro \
--image-id <AMI-ID> \
--subnet-id <SUBNET-ID> \
--tag-specifications "ResourceType=instance,Tags=[{Key=Name,Value=SSMTestInstance}]"Confirm that the instance is managed by AWS Systems Manager
- Get the instance ID of the new instance:
aws ec2 describe-instances --filters Name=tag:Name,Values=SSMTestInstance --query "Reservations[].Instances[].InstanceId"- Confirm that the instance ID shows up in SSM:
aws ssm describe-instance-information --query "InstanceInformationList[?InstanceId == '<INSTANCE-ID>']"Learn more
| To learn about... | Read... |
|---|---|
| Snapshot scanning | Scan an EBS Snapshot |
| Continuous AWS scanning | Continuously Scan AWS |
| cnspec | The cnspec documentation |