Scan an EBS Snapshot
Scan EBS volume snapshots to evaluate the security and compliance of Linux-based EC2 instances without requiring agent access.
Mondoo can scan your EBS volume snapshots to evaluate the security and compliance of Linux-based EC2 instances. It doesn't require an agent or any connection to the instance that could impact your business applications.
Snapshot scanning with Mondoo relies on cnspec, Mondoo's CLI security tool.
What you'll set up
This workflow creates a dedicated scanner EC2 instance that can attach and scan EBS snapshots from other instances in your account. You'll:
- Create a scanner VM — A small EC2 instance with cnspec installed
- Create an IAM policy — Permissions for EBS snapshot and volume operations
- Create an IAM role — An EC2 role with the scanning policy attached
- Attach the role and scan — Connect the role to your scanner VM and run scans
Prerequisites
- Access to the AWS console with permissions to create IAM policies, roles, and EC2 instances
- A Mondoo Platform account (for reporting results)
Step 1: Create a scanner VM
- Spin up a small EC2 instance (for example an Amazon Linux instance with the type
t3.micro) where you'll attach the EBS snapshot.
Step 2: Create an IAM policy for EBS volume scanning
- Log into the AWS console.
- Navigate to IAM.
- In the side navigation, select Policies.
- Select the Create policy button.
- Under Specify permissions select JSON, add the following block and select "Next":
{
"Version": "2012-10-17",
"Statement": [
{
"Action": ["ec2:AttachVolume", "ec2:DetachVolume", "ec2:DeleteVolume", "ec2:DeleteSnapshot"],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"ec2:CreateSnapshot",
"ec2:CreateVolume",
"ec2:CopySnapshot",
"ec2:CreateTags",
"ec2:DescribeInstances",
"ec2:DescribeVolumes",
"ec2:DescribeSnapshots",
"kms:Decrypt",
"kms:ReEncryptTo",
"kms:GenerateDataKeyWithoutPlaintext",
"kms:DescribeKey",
"kms:ReEncryptFrom"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
},
"Action": "kms:CreateGrant",
"Resource": "*",
"Effect": "Allow"
}
]
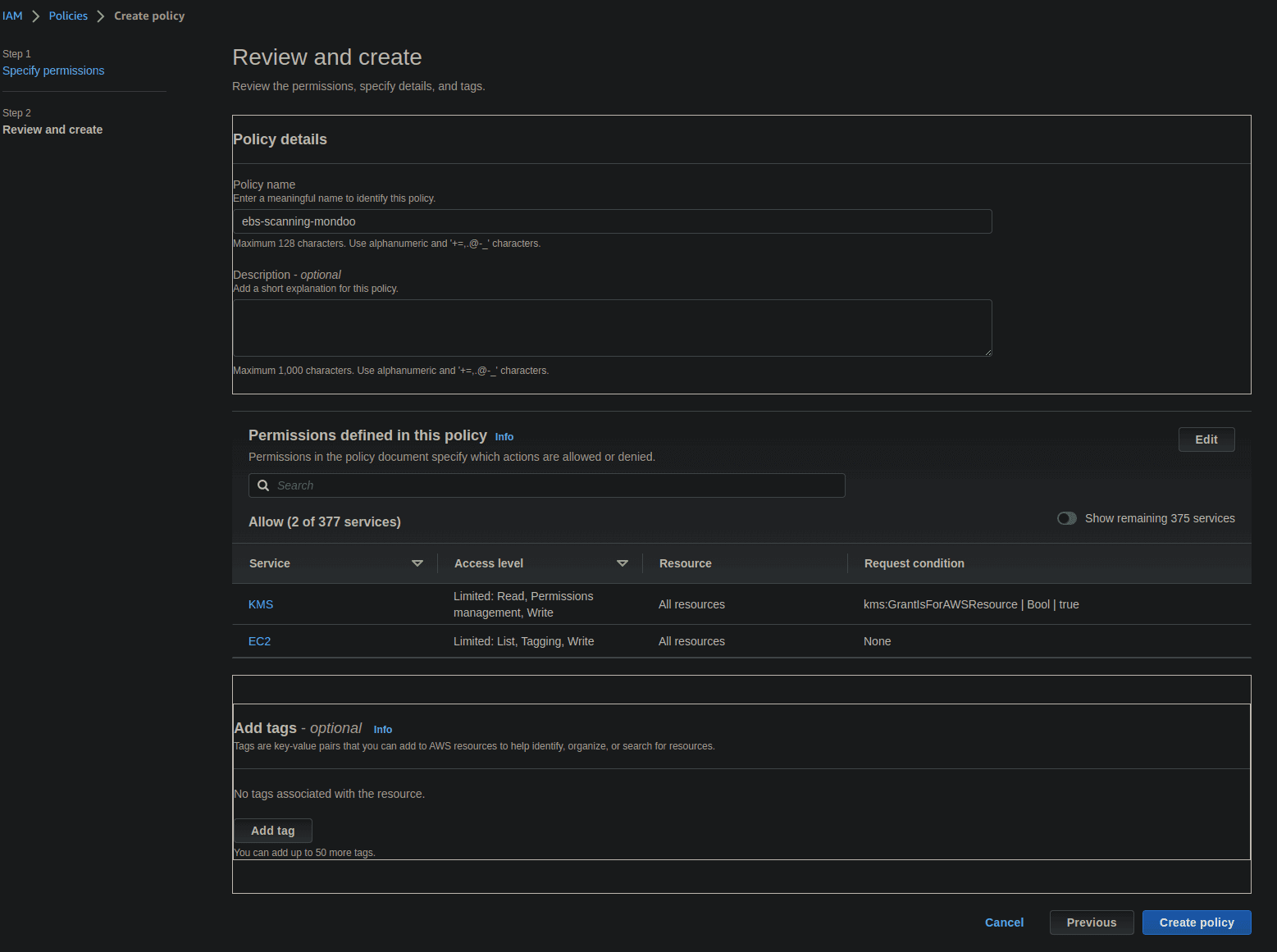
}- Under Policy details -> Policy name give the policy a name such as ebs-scanning-mondoo, assign tags and a description to the role (if you want), and then select Create policy.
Step 3: Create an IAM role for EBS volume scanning
- Log into the AWS console.
- Navigate to IAM.
- Select Roles.
- Select Create Role.
- For the Trust entity type, select AWS service and for the Use case, select EC2, then select the "Next" button.
- Search for ebs in the Filter policies box, select the policy you just created ebs-scanning-mondoo, and then select the "Next" button.
- Under Role details in the field "Role name" give the role a name ebs, assign tags and a description to the role (if you want), and then select Create role.

Step 4: Attach the role and scan
Attach the new IAM role (ebs) to your scanner EC2 instance. The role can be attached to existing EC2 instances, or to new EC2 instances as an instance profile when launching new instances.

Once the role is attached:
-
Log into your scanner EC2 instance.
-
Scan a snapshot:
cnspec scan aws ec2 ebs snapshot SNAPSHOT_IDFor SNAPSHOT_ID, substitute the ID of the snapshot, for example snap-123456b123a123da2.
Learn more
| To learn about... | Read... |
|---|---|
| Scanning with AWS SSM | Scan Using AWS Systems Manager |
| Scanning from a workstation | Scan from a Workstation |
| Continuous AWS scanning | Continuously Scan AWS |
| cnspec | The cnspec documentation |