
Mondoo Platform
Prevent breaches
before they happen
Intelligent AI agents that prioritize by business impact, remediate at machine speed, and orchestrate workflows end-to-end.
Why Mondoo
Built Different
Three core principles that set Mondoo apart from traditional security tools.
Unified
One platform for cloud, on-premises, SaaS, endpoints, network devices, and the SDLC. Replace 5-10 siloed tools with complete visibility across your entire IT infrastructure.
AI-Native
Patented AI model maps relationships between assets, configurations, and vulnerabilities to enable fast and accurate decision-making.
Transparent
Built on open source cnspec and cnquery. Every policy, every check, every fix is auditable. Full rollback capability for all automated changes.
The Problem
Siloed Tools Create Blind Spots
Traditional security tools were built for siloed environments. Cloud scanners miss on-prem. Vulnerability scanners lack configuration context. The result: a fragmented view that leaves critical gaps.
Mondoo Unified Platform
Single pane of glass across cloud, on-prem, SaaS, endpoints, network devices, and the SDLC
Correlated findings with full asset and configuration context
Continuous monitoring with real-time drift detection
One policy engine, one query language, one remediation workflow
Complete Coverage
Secure Your Entire IT Infrastructure
From cloud to on-prem to code, Mondoo provides security posture management across your entire technology stack, with the same depth of coverage everywhere.
Cloud Security
AWS, Azure, GCP, OCI
On-prem Security
Physical workloads and servers
Endpoint Security
On-prem and remote endpoints
Network Device Security
Firewalls, switches, routers, etc.
SaaS Security
Business-critical SaaS applications
SDLC Security
Shift-left security in pipelines
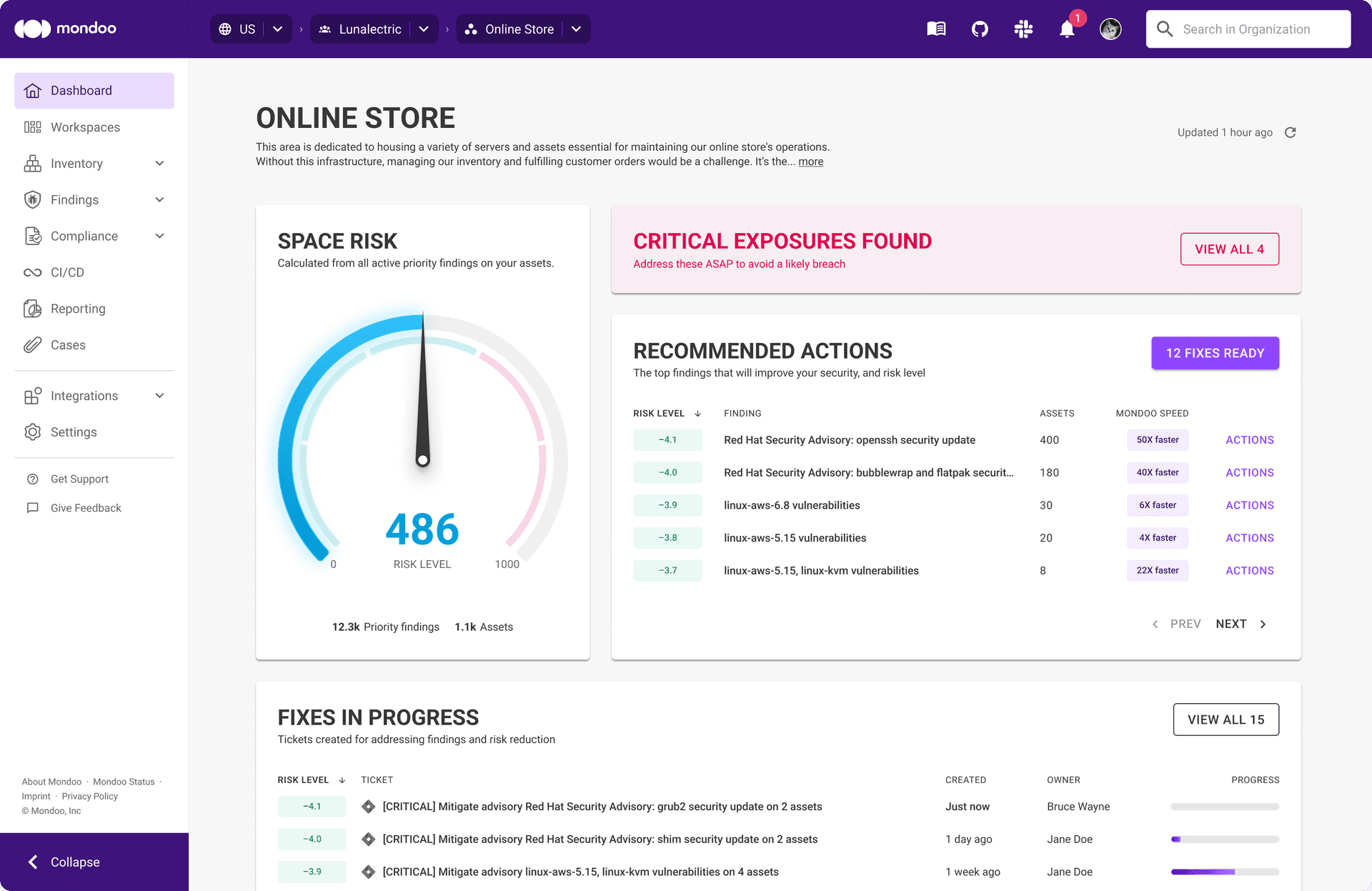
AI-Native Architecture
The Mondoo Intelligent Model
Powered by our groundbreaking Mondoo Intelligent Model and AI-native collector, Mondoo maps the hidden relationships between assets, configurations, and vulnerabilities - so our agents make decisions based on deep, contextual understanding rather than siloed data points.
Contextual Understanding
See how vulnerabilities relate to configurations, assets, and business impact across your entire infrastructure.
Risk-Based Prioritization
AI agents analyze the full context to prioritize what matters most, not just CVSS scores.
Fits Into Your Workflow
Access Mondoo intelligence through GUI, CLI, CI/CD pipelines, ticketing system, or chat.
The Mondoo Flow
Five Steps to Security
From discovery to remediation in five automated steps.
Discover
Full fleet visibility across cloud, on-prem, SaaS, network devices, endpoints, and the SDLC.
Scope
Customize with workspaces, asset tagging, SLAs, and compliance frameworks.
Prioritize
AI-powered risk scoring with CVSS, EPSS, and business impact.
Fix
Guided remediation with code snippets and ITSM integration.
Report
Security progress measurement and compliance reporting.
Capabilities
Everything You Need for Vulnerability Management
Comprehensive security management at scale.
Centralized Findings
Stop switching consoles. Eliminate duplicate alerts. Get one unified, prioritized view of all your assets and vulnerabilities.
Risk-Based Prioritization
AI-powered risk assessment considering exploitability and business context.
Continuous Compliance
300+ compliance templates and CIS benchmarks with automated evidence.
Fast Remediation
Guided remediation and pre-tested code snippets, with ITSM ticketing integrations such as Jira and ServiceNow.
Agentic Patching
Autonomously create pull requests in GitHub and apply with one-click.
Executive Reporting
Create and schedule compliance reports, vulnerability reports and SLA tracking.
The Mondoo Difference
Teams reduce daily security review time from
"3+ hours sifting through 15 tools"
to
"Less than 10 minutes"
See It In Action