Agentic Vulnerability Management
We don’t just tell you what’s wrong. We actually fix it.

Reduce vulnerabilities by 50% or more and speed up remediation with our Agentic Vulnerability ManagementTM that autonomously identifies, prioritizes, and remediates vulnerabilities and policy violations in your entire IT infrastructure - covering cloud, on-prem, SaaS, endpoints, and the SDLC.
What is agentic vulnerability management?
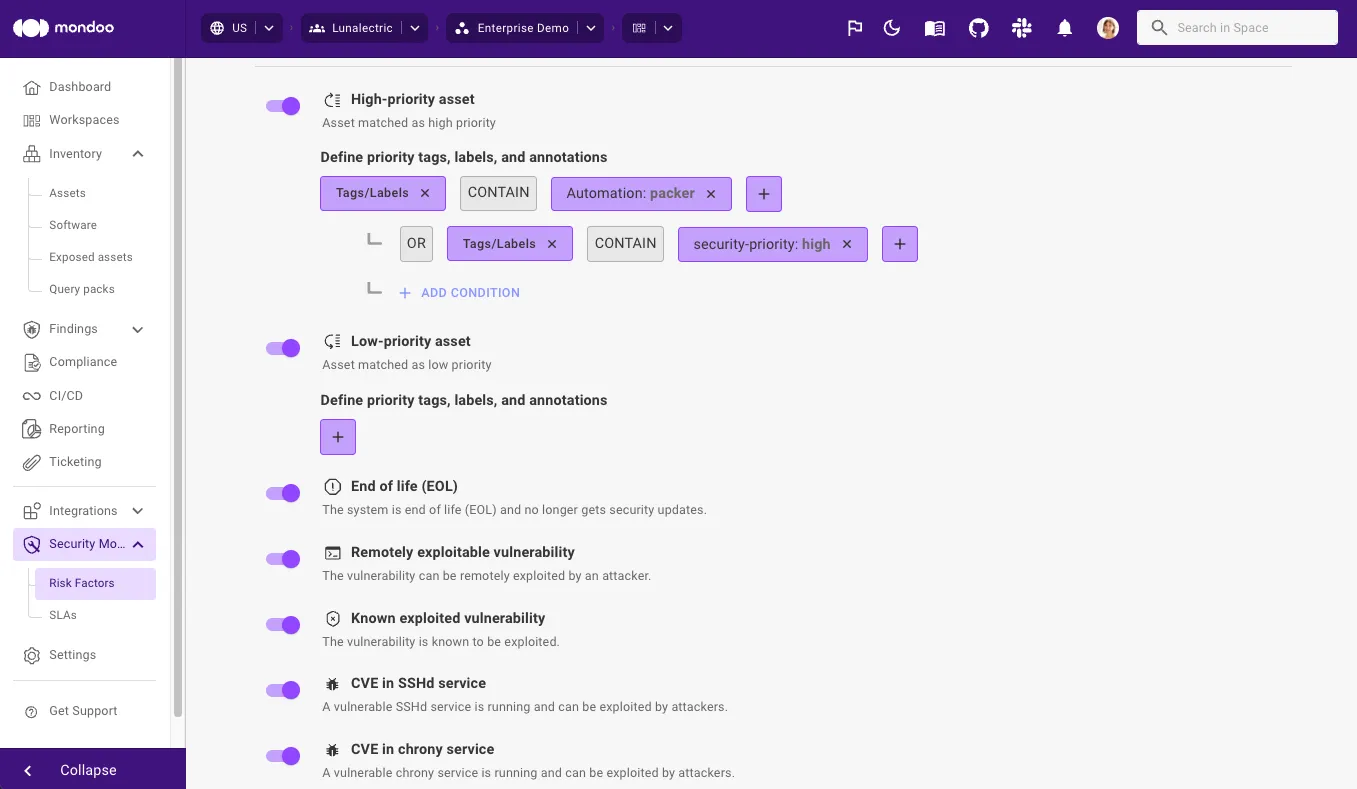
Unlike traditional vulnerability management which relies heavily on manual processes, agentic systems autonomously detect vulnerabilities, analyze contextual risk factors and business priorities to effectively prioritize risk, suggest and execute remediations, and verify resolution. This results in faster Mean Time to Remediation (MTTR), improved security posture, and stronger compliance, while leaving security teams more time to focus on strategic initiatives and high-value decision-making.
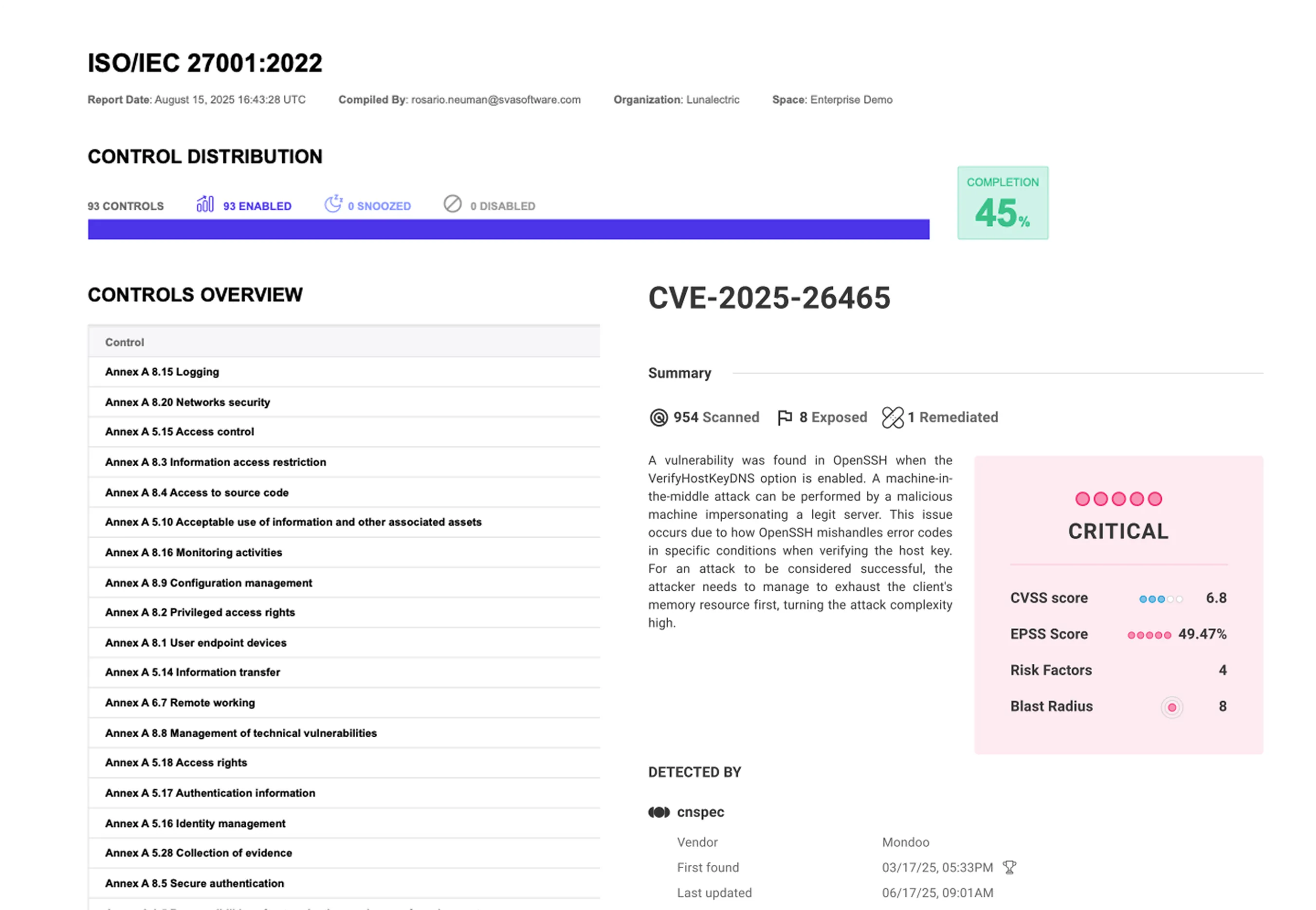
What is CTEM and exposure management?
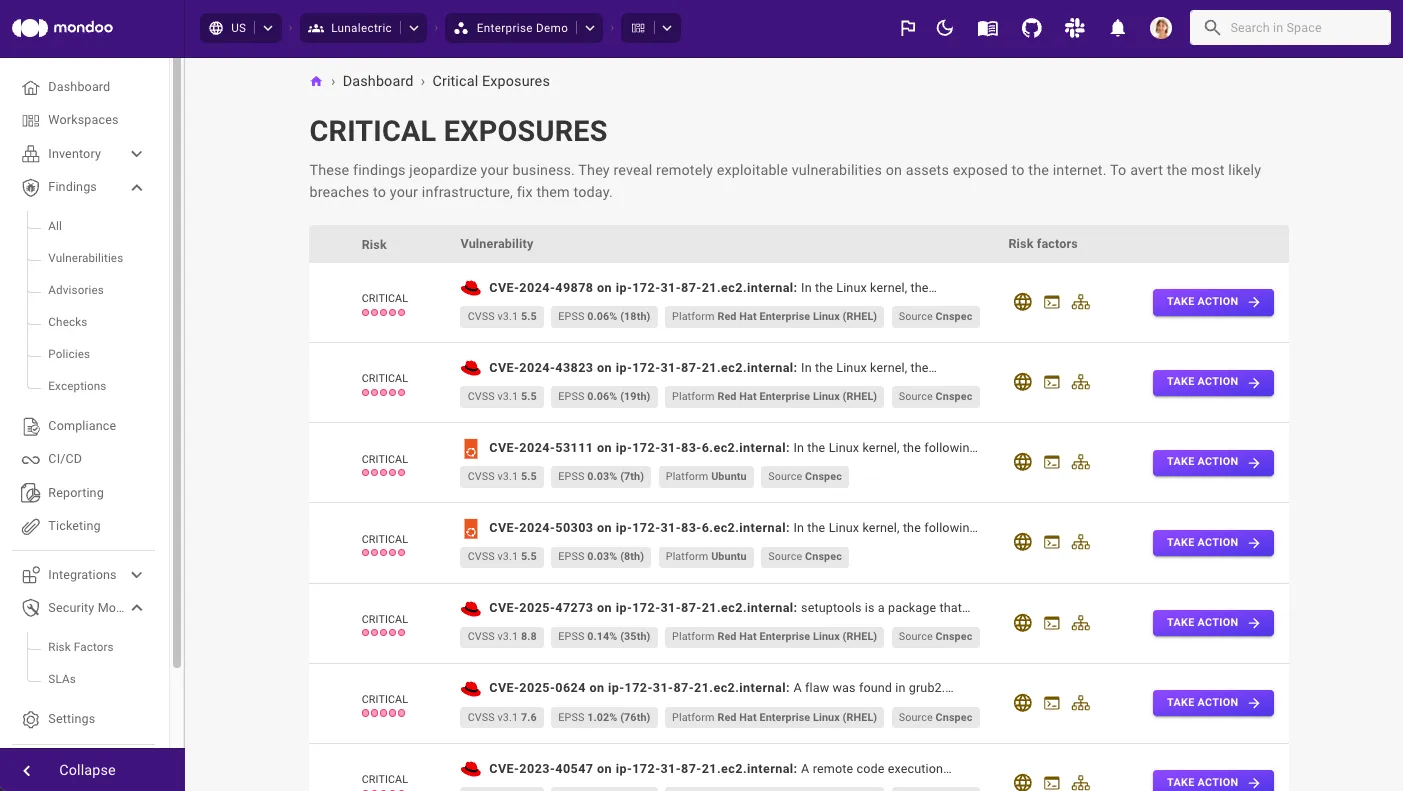
Since it’s impossible to protect against every cybersecurity event, CTEM (Cloud Threat Exposure Management) instead focuses on addressing the exposures that pose the greatest threat. Mondoo helps you do this by providing a prioritized view of your entire attack surface so you can optimize your security efforts for the biggest posture improvements.

The urgency
Attackers aren’t waiting to deploy Agentic AI, which means you can’t either. With the ever increasing volume of threats, growing complexity of infrastructures, and attackers moving faster than ever, traditional, human-led defense methods simply cannot keep pace. It’s time to start moving at machine speed.


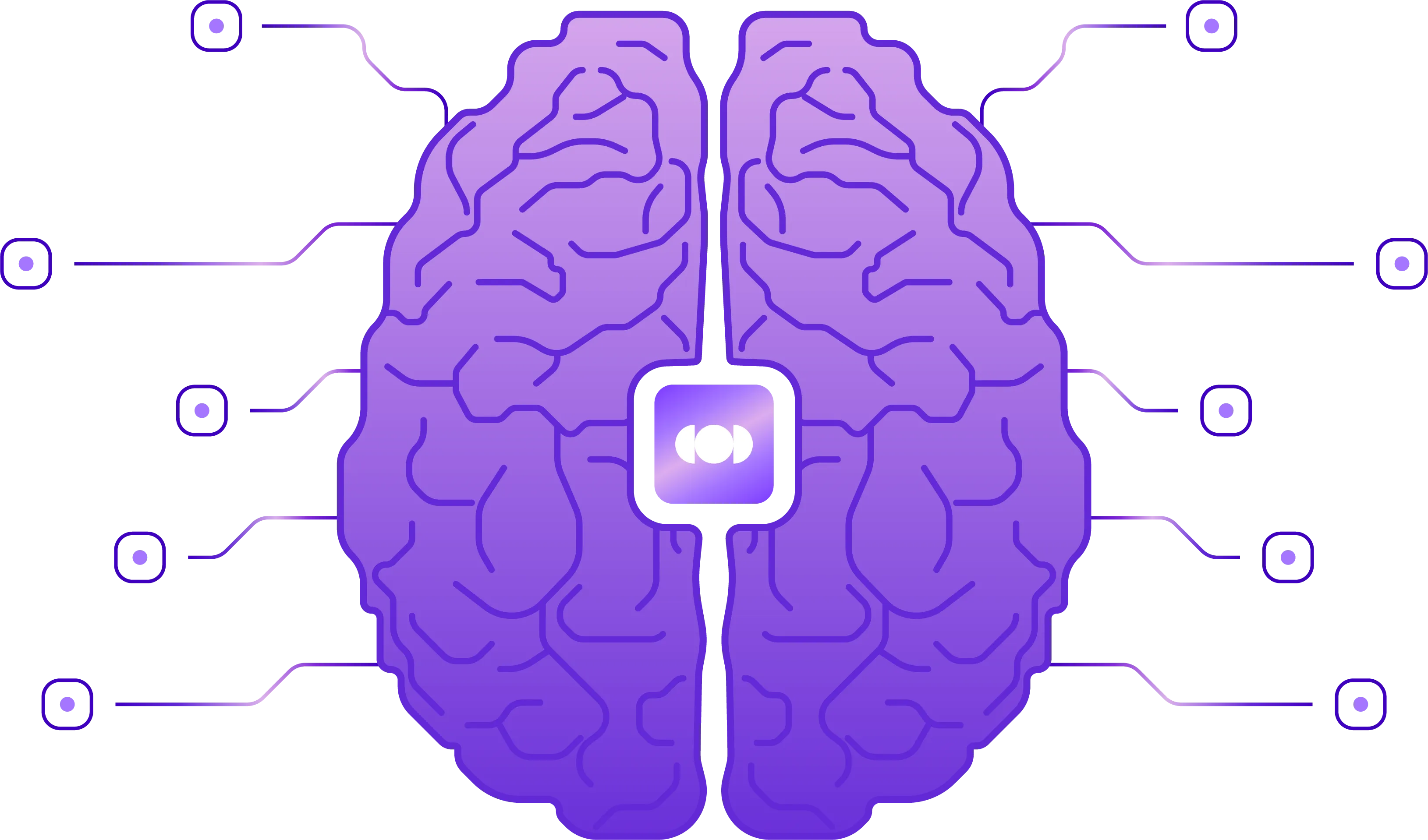
Why Mondoo Agentic AI?
AI is only as powerful as the data behind it. Mondoo’s patented AI-native security model provides our AI agents with unparalleled visibility across your entire IT ecosystem enabling them to make fast and accurate decisions. For all cloud and on-premises assets, Mondoo collects:

The Mondoo Flow


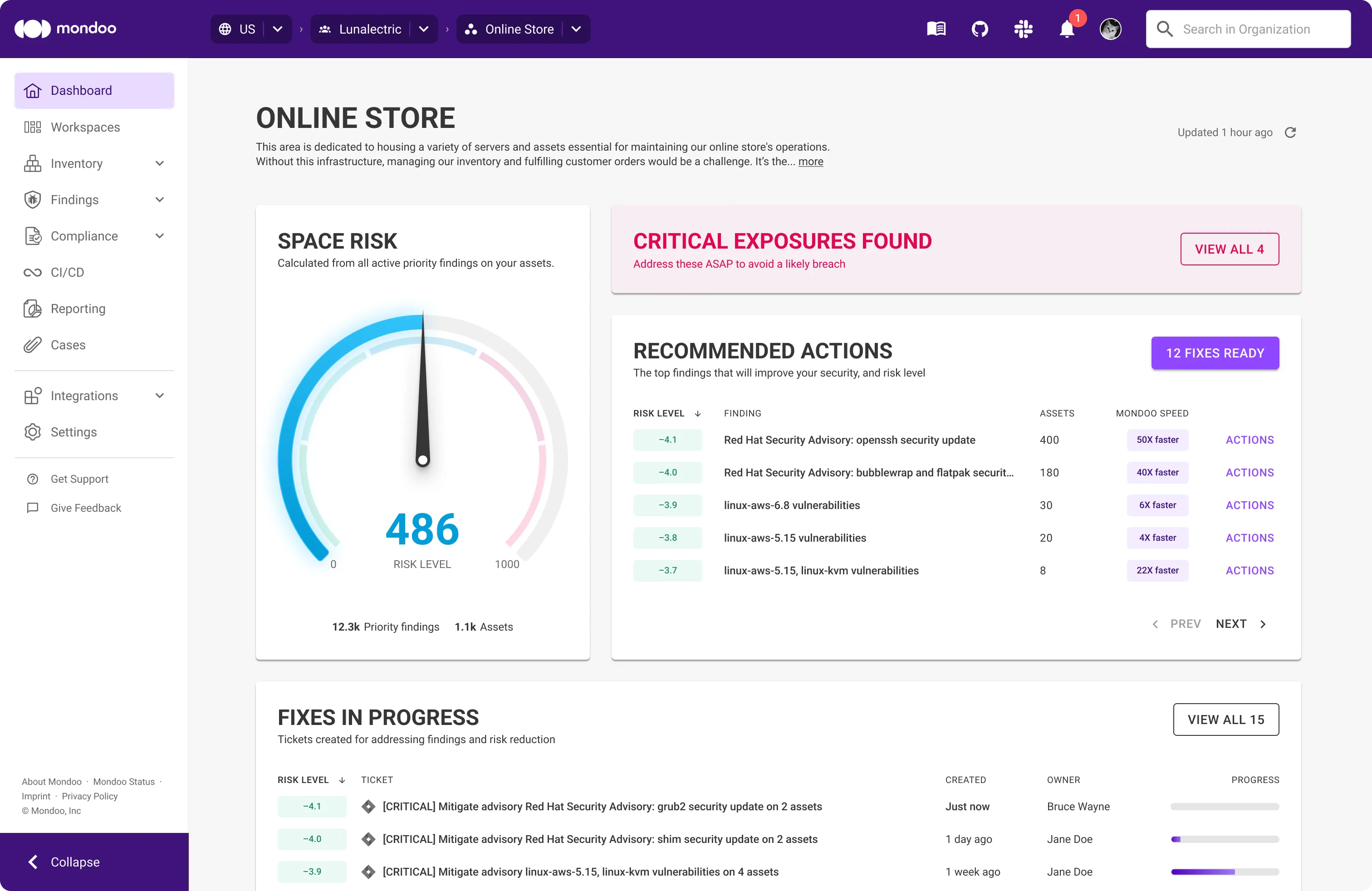
Guided and Agentic remediation
You choose: Guided remediation with pre-tested code snippets and configuration steps, or autonomous patching using the Mondoo security pipeline with humans in the loop. For both options, Mondoo agents can create tickets in ITSM systems, track them to completion, auto-close upon verification, and reopen tickets if drift occurs.

Easy and flexible deployment.
Agentless cloud snapshot and remote connectivity scanning for AWS, Azure, GCP, and OCI.
Lightweight agents for on-prem, containers and endpoints, across all OSs: Linux, Windows, Mac, BSD, and AIX.

Authenticated and unauthenticated scanning of assets.

Least-privilege and zero-trust deployments.