Mondoo 8.11 is out!
🥳 Mondoo 8.11 is out! This release includes security journey planning with Mondoo Risk Actions and IoT security improvements!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Plan your security journey with Risk Actions
Security tools can often be overwhelming. When you turn on a few policies and add some assets, you may be faced with an overwhelming amount of red in the first scan results. This can be demotivating and may obscure important results once you become accustomed to seeing so many failed checks.
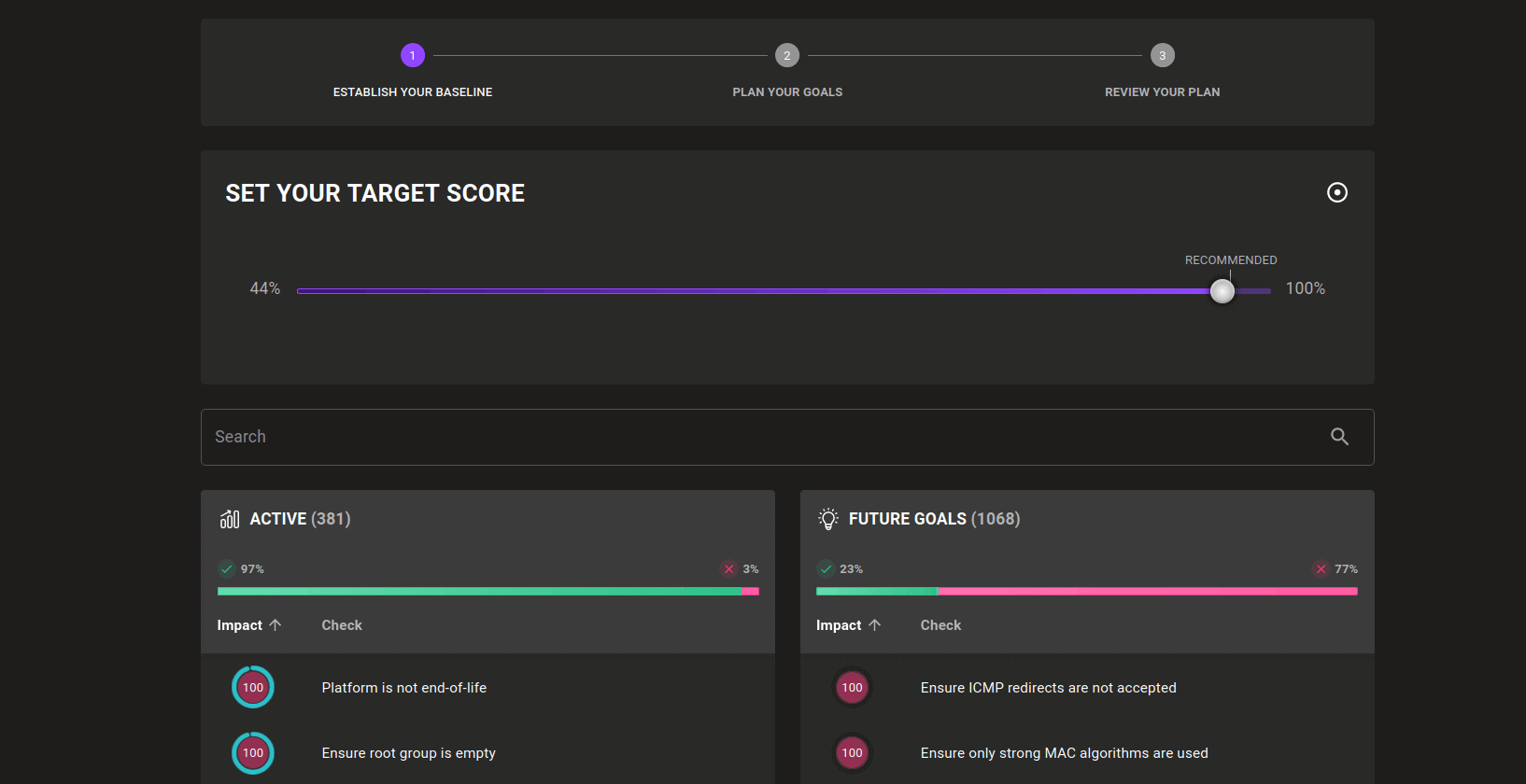
To help users create more actionable plans from their assessments, we are introducing Risk Actions. This new section in the dashboard can guide you in creating a baseline for your environments and planning remediation steps. It can improve your overall security reporting significantly:
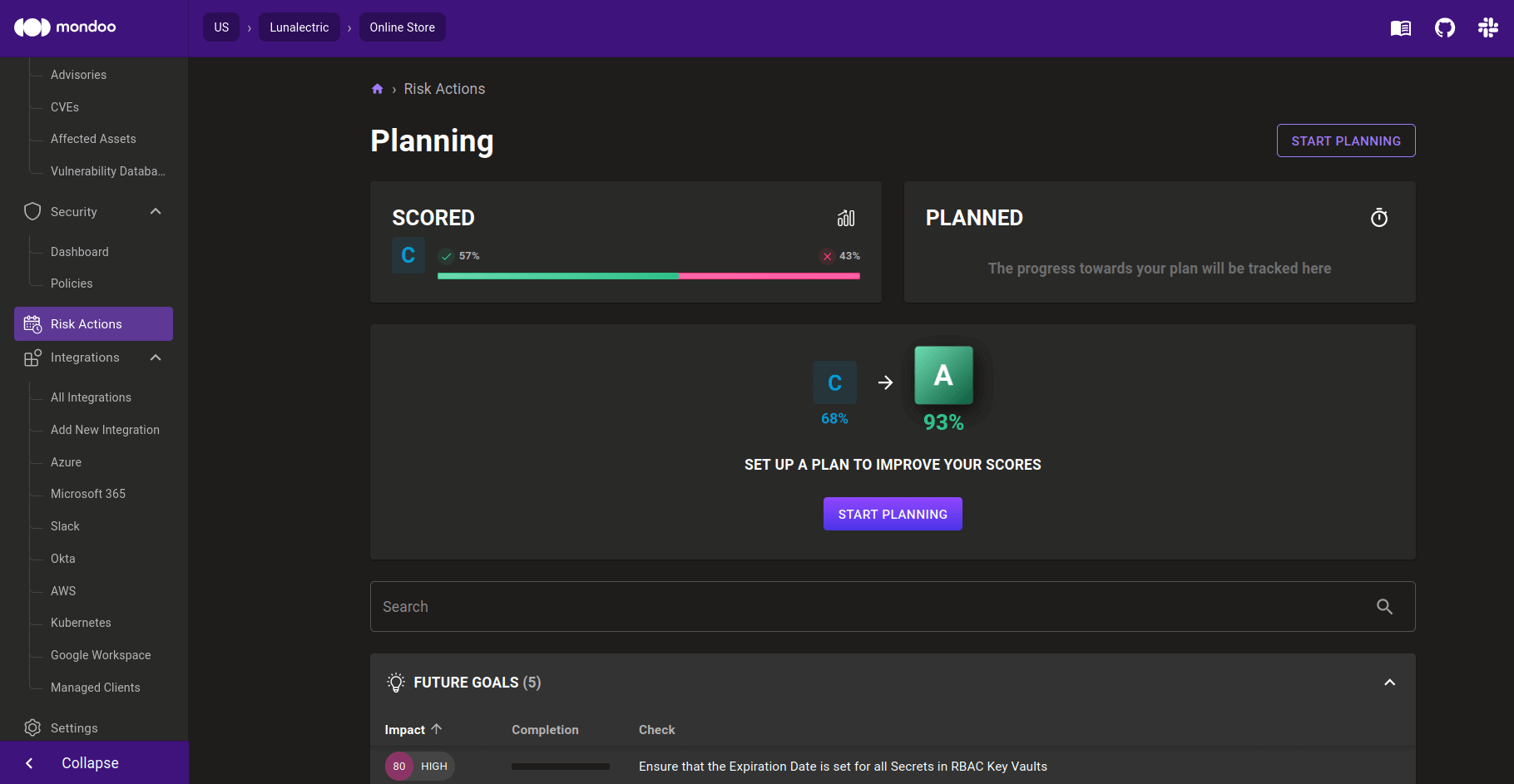
Risk Actions uses your current results across all assets to determine which areas are working well and which areas need improvements. The checks that are succeeding are turned into a baseline, reflecting where you are today and what is going well. If things deteriorate in this baseline, you will see these findings pop up. Everything else is turned into either goals or exceptions. Goals can be turned into future milestones to work towards. They are still evaluated, so you can see progress towards their completion. However, their score no longer impacts your asset score. All checks that are mostly failing today can be moved into goals, which stops them from showing up on dashboards and alerts every day. Everything else that you don't want to fix can be moved into an exception. It won't be evaluated, protecting the health of fragile systems, and it won't be reported anymore, giving you peace of mind.
Risk Actions also introduces justifications for these goals and exceptions. They help to communicate why checks are disabled or ignored and explain the reasons to auditors, leadership, and other internal teams.
We are in the process of heavily expanding on exceptions and the planning process with the upcoming release of the Compliance Hub in Mondoo. Stay tuned!
Examine OS images with filesystem mounts
Are you building IoT firmware and struggling to secure your devices before deploying them to the field? Now you can use cnquery and cnspec to evaluate your firmware images locally during development or within CI pipelines. Mount your image filesystem locally and then use the new filesystem provider fs to live query the image or scan it with Mondoo policies.
Shellcnquery shell fs /mnt/firmware/→ discover related assets for 1 asset(s)→ resolved assets resolved-assets=1___ _ __ __ _ _ _ ___ _ __ _ _/ __| '_ \ / _` | | | |/ _ \ '__| | | || (__| | | | (_| | |_| | __/ | | |_| |\___|_| |_|\__, |\__,_|\___|_| \__, |mondoo™ |_| |___/ interactive shellcnquery> asset { name version platform }asset: {version: "v3.1.17"platform: "poky-iot2000"name: "iot2000"}
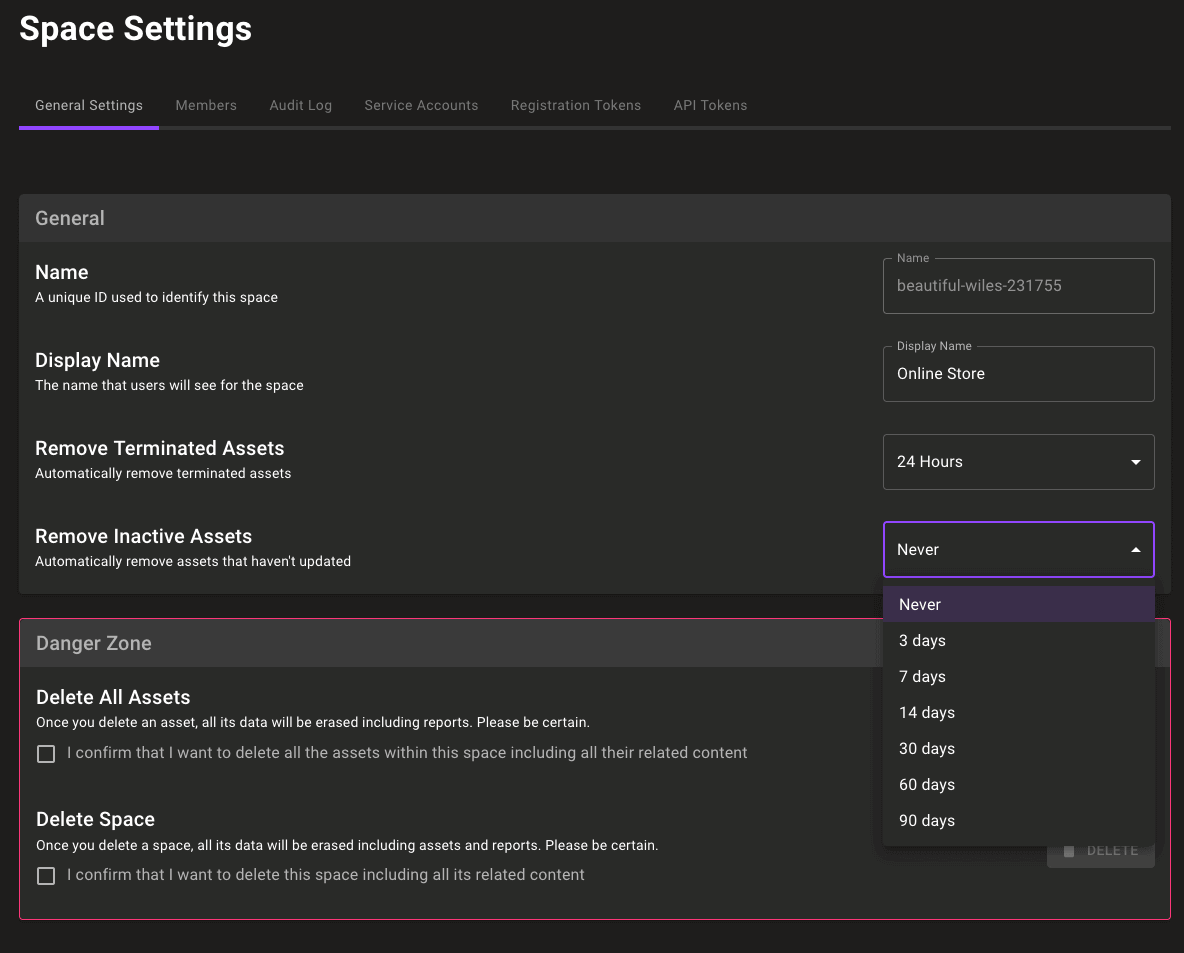
Automatically cleanup stale assets
Do assets that haven't checked in for weeks spark joy? Maybe it's time to toss them, and now you can do it automatically. We've added a new space setting to automatically clean up assets that haven't checked in:
🧹 IMPROVEMENTS
More frequent integration scans
Integrations that run directly from Mondoo Platform now scan your infrastructure every 4 hours, so you have up-to-date asset security and inventory data available at all times.
Improved query output when using the .all() MQL helper
Improved output in the MQL .all() helper makes it easier than ever to identify failures and resolve problems quickly. Previously any item that failed a query using the .all() helper would return just the ID of the failing object:
MQLResult:[failed] [].all()actual: [0: gcp.project.gkeService.cluster id = gcp.project.gkeService.cluster/7c50e440aa5c41cf8eff749a4f313953c4c974b985ab43d1b44871e7dbf3e9a7]
Now you'll see the default fields for the failing resource, giving you better context on the actual failing object:
MQLResult:[failed] [].all()actual: [0: gcp.project.gkeService.cluster {name: "test-cluster-2"}]
This helper is used extensively in Mondoo policies, so you'll see better query results throughout the platform. Thanks @multani for reporting this problem!
Support dicts with containsOnly in MQL
The containsOnly helper now allows you to find dicts within data. Given JSON data with a dict:
JSON{"string-array": ["a", "b", "c"]}
You can now query for the exact values "a", "b", "c" with:
MQLparse.json('my_json_data.json').params['string-array'].containsOnly(['a','c','b'])
Improve default resource values for AWS and Azure
Default resource values allow you to quickly navigate your infrastructure with cnquery and provide important failure context in your cnspec query results. We've updated many of our AWS and Azure resources to give you new and expanded default values, so you can better explore and secure your cloud environments.
platformDetails in the aws.ec2.instance resource
The aws.ec2.instance resource now includes platformDetails data from the AWS API, allowing you to identify the platform of systems without needing an EBS volume scan or client installation.
Use platformDetails to better understand MQL query results:
MQLcnquery> aws.ec2. instances .where( state == "running" ) { state region platformDetails } aws.ec2. instances .where:0: {platformDetails: "Windows"region: "us-east-1"state: "running"}1: {platformDetails: "Linux/UNIX"region: "us-east-2"state: "running"}2: {platformDetails: "Linux/UNIX"region: "us-east-2"state: "running"}3: {platformDetails: "Linux/UNIX"region: "us-east-2"state: "running"}
Improve opkg parsing for yocto-based Linux or openwrt
cnquery and cnspec now include improved support for the opkg package format found in Yocto Linux based IoT and networking devices like openwrt routers. We've improved detection of the opkg system and all available packages. You can now also statically analyze opkg data on firmware images using the filesystem (fs) provider in cnquery and cnspec:
MQLcnquery shell fs /mnt/firmware/cnquery> packagespackages.list: [0: package name="shadow-securetty" version="4.6-r3"1: package name="os-release-dev" version="1.0-r0"2: package name="iptables-module-xt-cgroup" version="1.8.4-r0"3: package name="libwebsockets-dev" version="4.0.1-r0"...]
Skip linting of policies before publishing
You can now skip the linting of policies before publishing them to the registry with the --no-lint flag:
Shellcnspec publish --no-lint ~/my_cool_policy.mql.yml
AWS Security and macOS Security policy updates
The AWS Security and macOS Security policies by Mondoo now include:
- Impact scores for all queries
- Improved failure output in queries
- More reliable queries
🐛 BUG FIXES AND UPDATES
- Fix a panic when analyzing Terraform HCL with parenthesis expressions. Thanks for reporting this @crcsmnky!
- Fix failures linting policies. Thanks for reporting this @kmf!
- Gracefully handle missing keypairs on AWS instances.
- Fix recording to work with
cnquery scan. - Fix
-o yamlto properly produce YAML output. - Only fetch AWS SNS tags when needed to reduce API usage.
- Fix the GCP group in the fleet page to list projects, not organizations.
- Add last scanned column in the Azure integrations page.
- Fix recording to work with
cnspec scan. - Expose the full failure messages when a plugin fails to load.
- Fix policies in the Security -> Policy page not loading correctly.
- Fix false positives in the CIS macOS FileVault checks.
- Fix
/etc/profilepermission checks in the CISEnsure default user umask is configuredcheck. - Fix CIS
Ensure shadow group is emptyfailures on Google COS. - Fix CIS
Ensure chrony is configuredfailures on Google COS. - Fix CIS
Ensure permissions on /etc/gshadow- are configuredfailures on Google CIS. - Update the CIS
Ensure system accounts are securedcheck to support/bin/falseas a valid shell. - Fix Azure SQL Database service server queries in Microsoft Azure Security policy to work with the latest cnspec.
- Improve remediation steps in Linux Security policy.
- Update asset pages to use the term "Annotations" instead of the legacy term "Tags".
- Don't run the first scan of an Azure integration until after the user has selected policies to enable.
- Improve the Windows install instructions on the Windows integration page.
- Add missing tooltips to CVEs in the organization dashboard to help with long CVE names.
- Rework the API Tokens tab interface in the space settings to make it simpler to setup new tokens.
- Fix the Danger Zone in space settings not always showing content.
- Fix the asset print view to print out policy data when using policy variants.
- Fix disabling policy checks when using Firefox