Mondoo Release Highlights January 2026
Introduction
Despite the cold temperatures, we hit the ground running in the new year: We added support for new OSes, updated and added new CIS policies, improved scoring for EOL assets, and more. Let's dig in!
Expanded vulnerability detection
To improve coverage and usability across modern environments, this month we added support for new platforms, enhanced Linux and Windows detection, and improved performance:
- Detect Windows Azure Editions and support hotpatching functionality
- Support Microsoft Exchange Subscription Edition (SE)
- Improved EulerOS vulnerability detection
- Support for Red Hat Enterprise Linux 10 Extended Update Support (EUS)
- RPM module vulnerability detection support for AlmaLinux and Oracle Linux
- Improved page load performance in spaces with a large number of vulnerabilities
Support for new OSes
Over the last few weeks we've added tons of new platform support to make sure you can use Mondoo to secure anything you might have. Mondoo is the only platform that provides 100% coverage of assets. No asterisk, no small print. This month we made the following additions and updates:
- CachyOS detection support
- Garden Linux detection support
- Windows Azure Edition detection
- NetBSD package and service detection support
- Solaris package and service detection support
- Azure Linux package detection support
- Improved hostname detection on BSD systems
- Improved asset overview information for network devices
Cloud resource improvements
The team has gone wild with improvements to our Azure, AWS, and M365 scanning capabilities, getting us ready for some exciting new CIS cloud benchmarks that will greatly expand the level of coverage Mondoo provides in the cloud. Many of these changes are small improvements across providers, but we've also added support for many new services. Stay tuned for policy updates next month!
- Azure Cloud Defender for APIs and CSPM
- AWS EC2 images in the account
- Azure Key Vault rotation policies
- Azure Storage blob versioning
- Azure Storage Account file service properties
- AWS ECS task definitions
- AWS Elastic Disaster Recovery (DRS)
- AWS ECS Services
- Azure Key Vault certificates
- Amazon FSx
- Azure Databricks
- AWS Secrets Manager Secrets are now detected as their own assets. Thanks @LittleSalkin1806!
New and updated policies
New policies
- CIS Debian Linux 13 v1.0
Updated policies
- CIS AlmaLinux 8 v3.0 -> v4.0
- CIS Google Container-Optimized OS v1.1 -> v1.2
- CIS Microsoft 365 Foundations v5.0 -> v6.0
- CIS Amazon Elastic Kubernetes Service (EKS) v1.7 -> v1.8
- CIS Google Kubernetes Engine (GKE) v1.7 -> v1.9
- CIS Azure Kubernetes Service (AKS) v1.7 -> v1.8
- CIS NGINX Benchmark v2.1 -> v3.0
- CIS Microsoft Azure Compute Services v1.0 -> v2.0
In addition to updates to CIS benchmarks, we simplified queries in GCP, AWS, and Azure policies to improve check page output and remove duplicate results. We also improved check impacts throughout policies to better prioritize the most important work first.
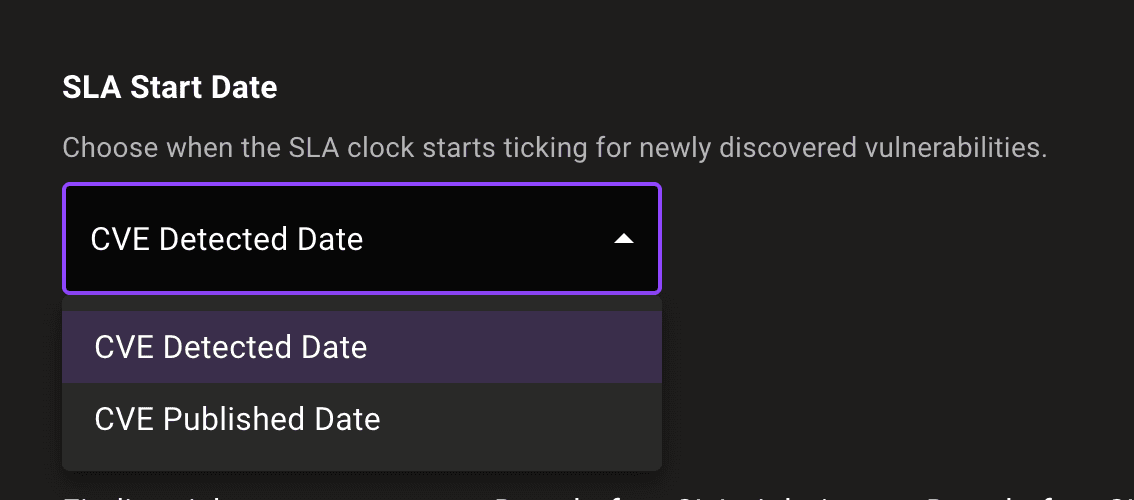
SLA start date selection
Users can now choose when the evaluation of an SLA starts. By default we start the clock at the time we first discover the issue, but now you can change to the time the vulnerability was published.
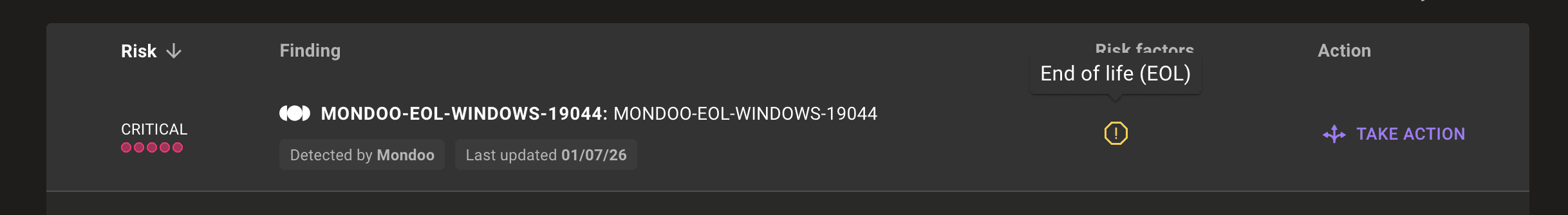
Improved scoring for EOL assets
The moment a system reaches End-of-Life (EOL), Mondoo scores its vulnerability risk at 100 because any new CVEs won't get patched by the vendor. We've now introduced gradual EOL scoring where the score will gradually increase from 0 to 100 starting a configurable number of months before EOL, to show the increased risk as the EOL date approaches. A new Mondoo EOL advisory also makes the why more apparent with a finding attached to the asset where an exception can be applied if necessary.
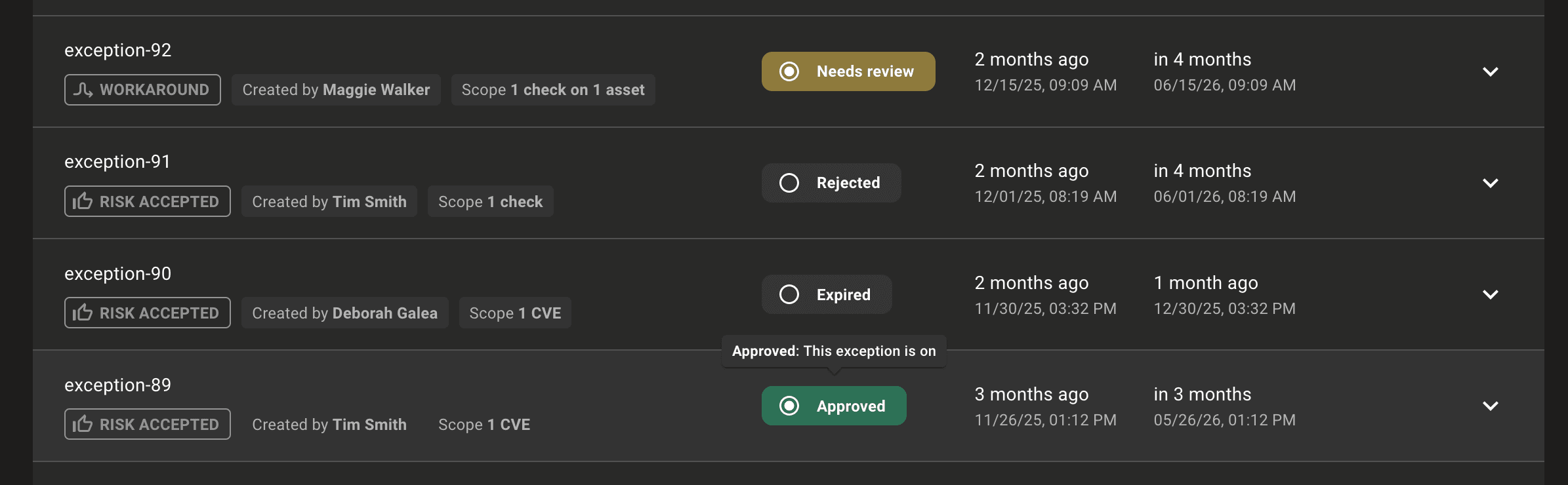
Improved exception status badges
We've added exception status badges to the console to give you clearer visibility into every stage of the exception lifecycle, so you can quickly understand which exceptions are pending review, currently applied, awaiting extension approval, or expired. This makes it easier to prioritize follow-ups, coordinate reviews across teams, and ensure exceptions don't linger unnoticed.
Improved CLI scanning results on GCP / AWS out of the box
cnspec now detects all resources as assets for GCP and AWS with simple command line scans. This means new users see the most robust scan results in the console without the need for special flags.
Detect application extensions
Browser and editor extensions are powerful productivity tools, but they can also introduce hidden security risks when left unmanaged. To help teams gain better visibility into this often-overlooked layer of their stack, we've added new MQL resources that expose installed extensions across popular desktop applications:
firefox.addonssafari.extensionsvscode.extensionschrome.extensions
Understand GitHub vulnerabilities in depth
Mondoo now brings your GitHub Code Scanning, Secret Scanning, and Dependabot alerts into a single place, giving security teams clearer visibility into code risks, exposed secrets, and vulnerable dependencies without jumping between tools. Centralizing this data makes it easier to prioritize issues, enforce standards, and act faster. Jump in today with custom policies, or stay tuned for new out-of-the-box functionality powered by these resources next month.
github.dependabotAlertgithub.secretScanningAlertgithub.codeScanningAlert
While we're talking GitHub, new fields on the github.organization resource expose critical settings to secure new repositories and lock down what organization members can do to repositories:
Dependabot and security settings:
dependabotAlertsEnabledForNewRepos- Whether Dependabot alerts are enabled for new repositoriesdependabotSecurityUpdatesEnabledForNewRepos- Whether Dependabot security updates are enabled for new repositoriesadvancedSecurityEnabledForNewRepos- Whether GitHub Advanced Security is enabled for new repositories
Secret scanning settings:
secretScanningEnabledForNewRepos- Whether secret scanning is enabled for new repositoriessecretScanningPushProtectionEnabledForNewRepos- Whether secret scanning push protection is enabled for new repositoriessecretScanningValidityChecksEnabled- Whether secret scanning validity checks are enabled
Member permissions:
membersCanDeleteRepositories- Whether members can delete repositoriesmembersCanChangeRepoVisibility- Whether members can change repository visibilitymembersCanDeleteIssues- Whether members can delete issuesreadersCanCreateDiscussions- Whether readers can create discussions
Deeper OS visibility without the work
Mondoo now provides additional operating system resources that expose critical configuration details for deeper security visibility. Resources like openBSMAudit, containerd, modprobe, and crontab make writing complex security checks easier by surfacing system-level data through straightforward queries, without the need for custom scripts or manual data collection. This simplifies how teams assess and monitor core OS configurations.
Other updates
- EPSS scores are now included in BigQuery data exports
- More than a dozen new vendor icons are included on the software page
- Debian 13 support in the Mondoo Ansible role. Thanks @elivlo!
- Improved Jira instance URL parsing in the Atlassian provider
- Improved performance discovering resources during AWS scans. Thanks @LittleSalkin1806!
That's a wrap for January 2026! We can't wait to share the many new exciting capabilities we have planned for next month. Check back soon!