Mondoo 11.9 is out!
🥳 Mondoo 11.9 is out! This release includes Windows filesystem scanning, expanded IaC reporting, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Windows filesystem scanning
Need to inspect a Windows system, but don't have access to install cnquery on the system? Now you can attach the drive, or a snapshot of the drive, to another Windows system and run cnquery shell complete with access to all of Mondoo's Windows MQL resources.
Run cnquery shell against a drive by serial number:
Shell./cnquery.exe shell device --serial-number 123455
Run cnquery shell against a specific LUN:
Shell./cnquery.exe shell device --lun 2
🧹 IMPROVEMENTS
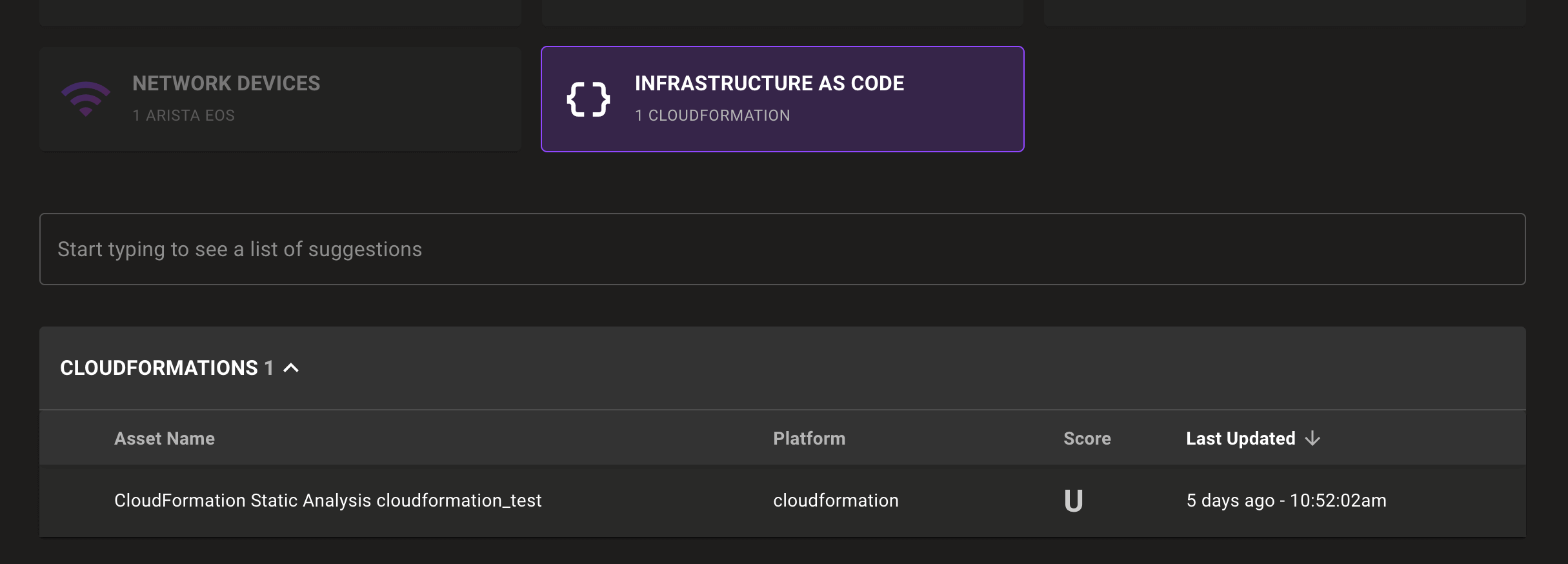
Infrastructure as code inventory group
Find Mondoo scanned Infrastructure as Code (IaC) files quickly with a new Infrastructure as Code asset group in the Mondoo Console inventory page:
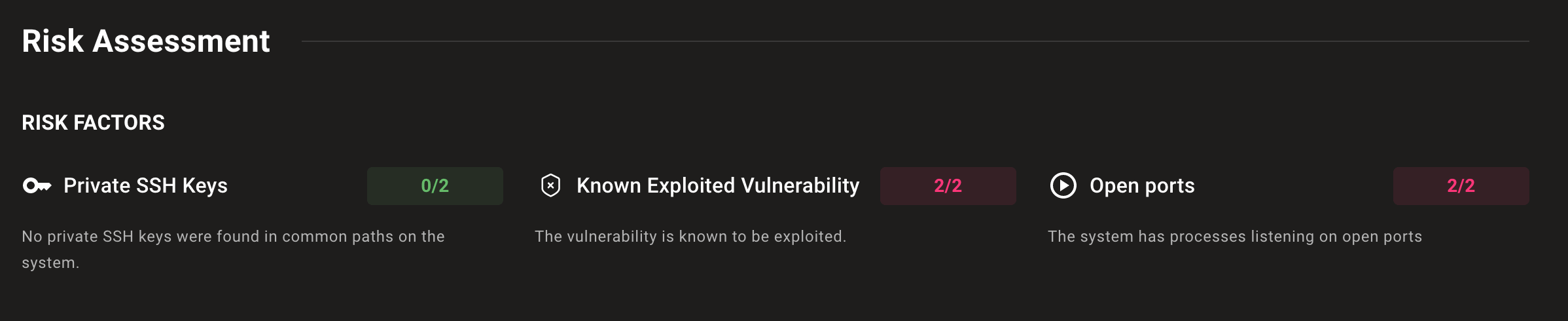
Improved risk factor display
We improved the risk assessment view on CVE and advisory pages so you can better understand which risks apply to assets and which don't.
Expanded Endpoint Detection and Response (EDR) policy support
The Mondoo Endpoint Detection and Response (EDR) policy now detects systems running Windows Defender with up-to-date definition files.
Kubernetes service discovery
Expand visibility into your Kubernetes cluster with discovery of Kubernetes services as assets in the Mondoo Console.
Find files by permission
Use the expanded files.find MQL resource to find files containing specific permissions across entire filesystems or specific paths. Pass in standard UNIX octal permission values to find files containing those permissions. Note: This is not an exact match. Searching for '0001' returns all files with execute on other, even if they also have read and write on other.
MQLcnquery> files.find(from: "/etc", type: "file", xdev: false, permissions: 0001)files.find.list: [0: file path="/etc/periodic/daily/999.local" size=712 permissions.string="-rwxr-xr-x"1: file path="/etc/periodic/monthly/999.local" size=606 permissions.string="-rwxr-xr-x"2: file path="/etc/periodic/weekly/999.local" size=620 permissions.string="-rwxr-xr-x"3: file path="/etc/security/audit_warn" size=1326 permissions.string="-r-xr-xr-x"
Resource updates
aws.account
- New
tagsfield. Thanks for this contribution, @Pauti!
gcp.project.computeService
- New
enabledfield.
🐛 BUG FIXES AND UPDATES
- Better handle nil values for
deprecatedAtorcreatedAtfields in theaws.ec2.imageresource. - Add
asset.runtimevalue to CloudFormation assets. - Fix large numbers of advisories or vulnerabilities not displaying correctly on assets.
- Don't show unknown cloud asset inventory information for containers.
- Improve the performance of macOS asset inventory gathering.
- Report unknown serial numbers when OEMs have not set a serial number.
- Fix a failure when scanning Microsoft 365 tenants without a Teams protection policy.
- Fix false negatives for Azure PostgreSQL flexible server checks in the CIS Azure Foundations benchmark policy.
- Fix cancelling jobs for AWS serverless integrations.
- Improve reliability of container pulling checks in both CIS and Mondoo Kubernetes policies.
- Improve reliability of ephemeral container checks in the Mondoo Kubernetes Cluster and Workload Security policy.
- Fix duplicate vulnerability data in S3 exports.
- Improve wording in risk factor descriptions.
- Fix duplicate software displaying on the asset software tab.
- Group Shodan scans under the Network Devices inventory category.
- Improve performance fetching AWS EFS filesystem data.
- Better handle AWS rate limiting when fetching AWS IAM Credential Report information.
- Fix a failure fetching
networkConfiginformation within thegcp.project.gke.clusterresource. - Fix failing integrations not displaying as failing.
- Fix failures scanning larger AWS accounts using the serverless AWS integration.
- Don't allow clicking the update integration button in the Kubernetes integration form if nothing has changed.
- Improve reliability of EOL risk factor in the affected assets page.
- Add EOL date for openSUSE 15.5.
- Improve formatting in generated package vulnerability remediation scripts.
- Display the complete product name of "Azure SQL Database Server" for "azure-sql-server" platform assets in the console.
- Fix vulnerability scanning on RPM-based systems when using EBS snapshot scanning.
- Fix the Mondoo-hosted AWS integrations not scanning cloud resources as individual assets.
- Fix incorrect coloring for the Known Exploitable Vulnerability risk factor badge.