Mondoo 10.8 is out!
🥳 Mondoo 10.8 is out! This release includes NIST CSF 2.0 compliance support, Okta and Entra ID SCIM, expanded policies, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Okta and Microsoft Entra ID SCIM 2.0 support
There's nothing worse than the endless stream of tickets to add, remove, or change user access to SaaS services. Now, with Okta and Microsoft Entra ID SCIM 2.0 support in Mondoo private instances, that's a thing of the past. Sync your users and groups automatically so the right users always have the proper access, keeping your auditors happy without a ticket in sight. Did that big budget increase finally allow you to expand your security team? Automatically provision access for your new team members as they start. Time to promote an engineer into management to wrangle your growing team? Automatically provide that employee with the appropriate administrative access to Mondoo spaces and organizations. Contact your support representative to learn more about enabling SCIM 2.0 support, including automated deployment options with the Mondoo Terraform provider.
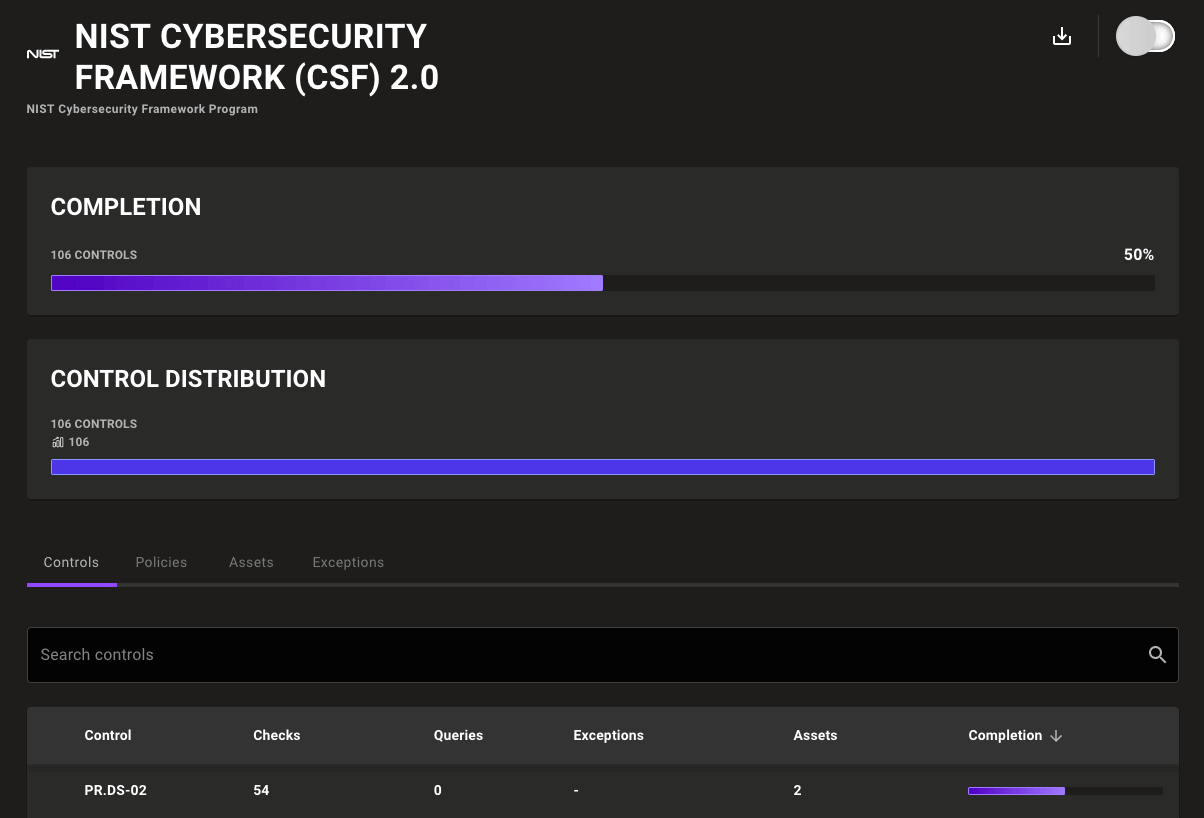
NIST Cybersecurity Framework (CSF) 2.0 support
Automatically track your compliance against the newly released NIST Cybersecurity Framework (CSF) 2.0. With CIS benchmark checks automatically mapped to the 104 new CSF 2.0 controls, you can enable policies and watch the results flow in showing where you stack up against these updated NIST recommendations.
🧹 IMPROVEMENTS
Resource improvements
gcp.project.computeService.attachedDisk
- Add a new
sourcefield.
AWS Resources
- Improve handling of integer values in AWS. Fields representing maximum/minimum values, such as
aws.cloudfront.distribution.origin.connectionTimeout, now return0when no value has been set. When a field represents a port value, such asaws.rds.dbInstance.port, Mondoo now represents unset values as-1.
Expanded CIS GCP Foundations policy
Catch security problems before they reach production without the need for multiple tools and security policies. New Terraform variants in the CIS GCP Foundations benchmark policy provide a single check for both running GCP assets and the Terraform code that generates those assets. Learn more about securing Terraform code using Mondoo in the Mondoo docs.
New CLI flags for inventory files
New simpler command line flags make it clearer how to use inventory files with cnspec and how to specify different inventory formats:
--inventory-file string: Set the path to the inventory file.--inventory-format-ansible: Set the inventory format to Ansible.--inventory-format-domainlist: Set the inventory format to domain list.
Additional package data in SBOMs
SBOM files generated with cnquery sbom now include each installed package's origin and architecture data.
Improved AWS instance naming / tagging
AWS instances scanned with SSM or through the Mondoo Platform AWS integration include new configuration information to make them easier to find and understand:
- Asset names now use the AWS instance name (if the instance has a name)
- New
mondoo.com/parent-id,mondoo.com/instance-id, andmondoo.com/ssm-connectionlabels display on each AWS instance asset.
Wolfi container package detection
Expose package information in Chainguard's Wolfi "un-distribution" with support for Wolfi's APK packages:
Shellcnquery shell container image cgr.dev/chainguard/caddy→ connected to Wolfi___ _ __ __ _ _ _ ___ _ __ _ _/ __| '_ \ / _` | | | |/ _ \ '__| | | || (__| | | | (_| | |_| | __/ | | |_| |\___|_| |_|\__, |\__,_|\___|_| \__, |mondoo™ |_| |___/ interactive shellcnquery> packagespackages.list: [0: package name="ca-certificates-bundle" version="1708982311:20240226-r0"1: package name="caddy" version="1710420294:2.7.6-r4"2: package name="wolfi-baselayout" version="1701735113:20230201-r7"]
🐛 BUG FIXES AND UPDATES
- Rename the spaces Overview page to Dashboard.
- Rename the Security and Vulnerability Dashboard pages to be Overview.
- Resolve failures scanning Amazon ECR.
- Add missing description and remediation step in
NSA PowerShell: Security Measures to Use and Embracepolicy. - Update searches on the space page to be case-insensitive.
- Improve reliability of queries in the CIS Azure Foundations and AWS Operational Best Practices policies.
- Remove any pending space invites if the inviter no longer has the necessary privileges to invite users.
- Fix failures loading software pages on an asset due to duplicate discovered packages.
- When an Ansible inventory file is malformed, display an error message instead of returning 0 assets.
- Support generating Ubuntu CPEs in SBOMs on the upcoming Ubuntu 24.04 release.
- Fix failures scanning AWS instances from the AWS integration.
- Improve checks for LAPS on Windows assets in CIS/BSI policies.
- Improve checks for anonymous pipe access on Windows assets to account for differences between domain controllers and domain member servers.
- Improve the descriptions and remediation text in the AWS Operational Best Practices policies.