Mondoo 7.17 is out!
🥳 Mondoo 7.17 is out! This release includes Amazon ECR/ECS scanning, new Amazon and Azure resources, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Continuous Amazon ECR and ECS scanning
Problem: You want to continuously scan Amazon Elastic Container Registry (ECR) registries and Amazon Elastic Container Service (ECS) containers using the Mondoo AWS integration.
Solution: You can now configure the Mondoo AWS integration to continuously scan your ECR and ECS infrastructure, providing security insight to your critical container infrastructure.
New azure.subscription.aks.cluster resource
Problem: You want to write policies to secure your Azure Kubernetes Service (AKS) clusters
Solution: A new azure.subscription.aks.cluster resource allows you to explore and secure the settings in your Kubernetes control plane.
To list all AKS clusters:
cnquery> azure.subscription.aks.clusters
azure.subscription.aks.clusters: [
0: azure.subscription.aksService.cluster name="aks-dev-cluster" location="westeurope"
]
To select particular fields for each cluster:
cnquery> azure.subscription.aks.clusters{name rbacEnabled kubernetesVersion powerState}
azure.subscription.aks.clusters: [
0: {
rbacEnabled: true
powerState: "Running"
kubernetesVersion: "1.24.9"
name: "aks-dev-cluster"
}
]
Detect and secure PLCnext programmable logic controllers
Problem: You need to secure Phoenix PLCnext programmable logic controllers to protect your physical infrastructure.
Solution: cnspec and cnquery now detect Phoenix PLCnext PLCs, and we've introduced a new community Phoenix PLCnext Security Policy that includes 22 security guidelines based on recommendations from PLCnext community.
cnquery PLCnext platform output:
platform: {
name: "plcnext"
build: "d755854b5b21ecb8dca26b0a560e6842a0c638d7"
title: "PLCnext"
version: "23.0.0.65"
}
New aws.ssm resource
Problem: You want to write policies to secure your AWS Systems Manager (SSM) instances.
Solution: A new aws.ssm resource allows you to explore and secure the settings in your AWS Systems Manager (SSM) infrastructure.
To query SSM data using cnquery:
cnquery> aws.ssm.instances { * }
aws.ssm.instances: [
0: {
arn: "arn:aws:ssm:us-east-1:185972261234:instance/i-0f58c727dc7ca1337"
platformName: "Microsoft Windows Server 2022 Datacenter"
ipAddress: "172.1.89.50"
instanceId: "i-0f58c727dc7ca1337"
region: "us-west-2"
pingStatus: "Online"
tags: {
Name: "test-win"
}
}
1: {
arn: "arn:aws:ssm:us-east-1:185972261234:instance/i-04680e19801302600"
platformName: "Amazon Linux"
ipAddress: "172.1.80.30"
instanceId: "i-04680e19801302600"
region: "us-west-2"
pingStatus: "Online"
tags: {
Name: "badssm"
}
}
...
Or write a query for a policy:
cnquery> aws.ssm.instances.all(pingStatus == "Online")
[ok] value: true
🧹 IMPROVEMENTS
Better integrations navigation menu
We received tons of great feedback on the new navigation menu we released last week with Mondoo 7.16. Many of you asked for a simpler integrations menu that better represented the integrations in your spaces. This week we reworked the integrations menu to only show the integrations you've already set up and to always include a link to add new integrations. Thank you, everyone, for all the great feedback.
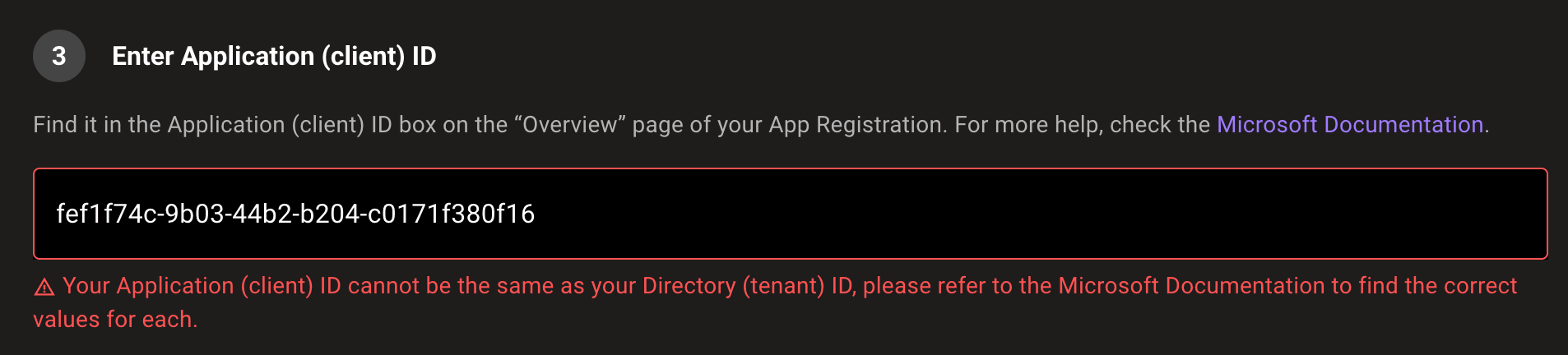
Input validation when setting up Azure and Microsoft 365 integrations
Securing your cloud can be difficult, but Mondoo shouldn't be. We've added example text and input validation to the Azure and Microsoft 365 integration setup pages to ensure you set up integrations with the correct values.
Immediately scan GCP, Azure, and Microsoft 365 after setup
Our GCP, Azure, and Microsoft 365 integrations now start scanning your infrastructure after setup so you can see results in minutes.
Improved platform names and grouping for cloud & SaaS assets
To make it easier to find your assets, we've renamed several platforms and added new groups in the fleet view. azure, slack, and okta assets are now azure-subscription, slack-team, and okta-org to better represent what they contain. The fleet view includes new Okta, Google Workspace, and Slack groups for filtering assets by SaaS service.
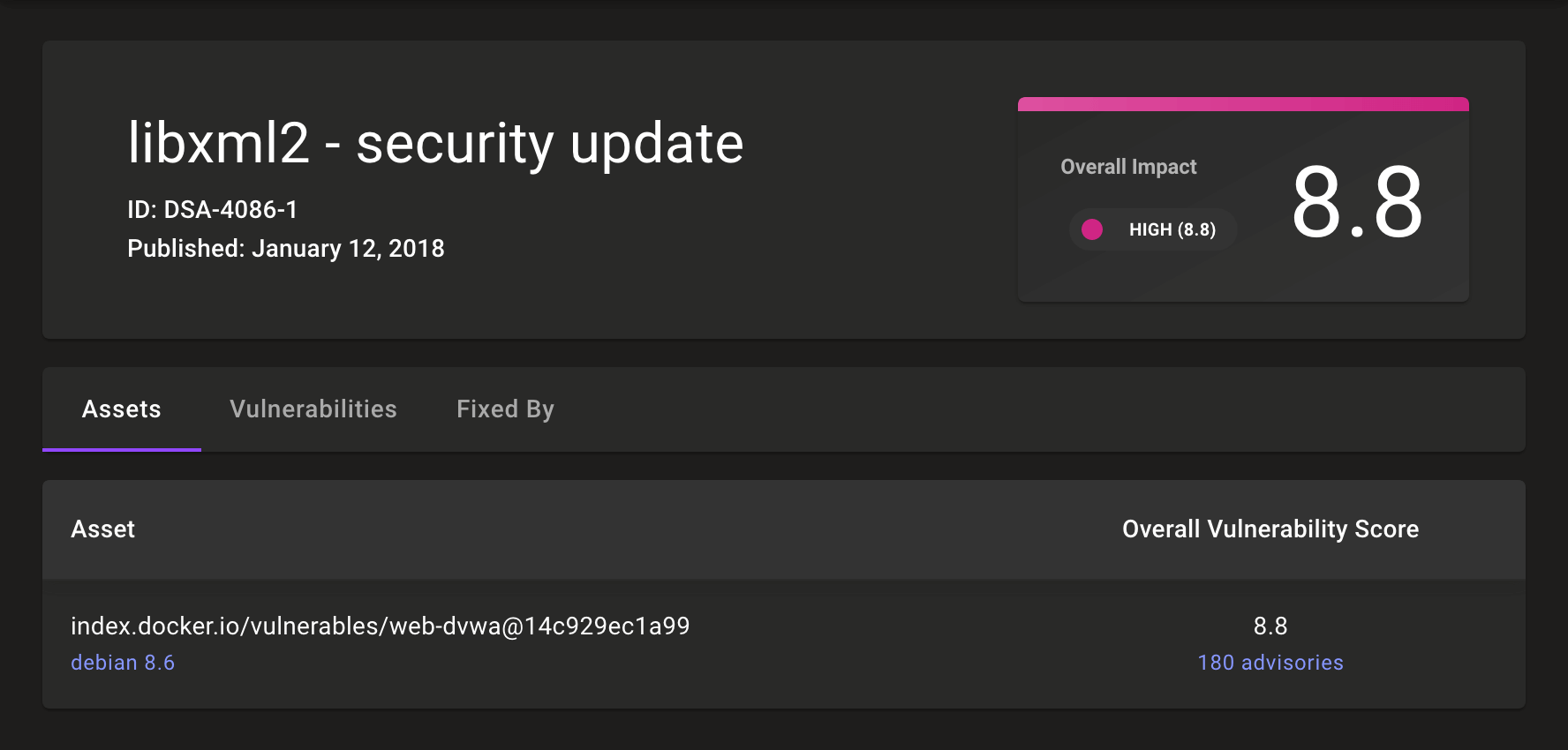
Show asset advisory counts in CVE views
CVE pages now show information on the asset score for each affected asset as well as the total number of advisories for each asset so you can better prioritize which assets to patch first.
Deploy cnspec with Chef Infra
The mondoo cookbook 0.5.0 is now available on Chef Supermarket. This updated release now configures systems to use the cnspec service. If your system was configured with the existing cookbook release, don't worry; this release will automatically update systems from the mondoo service to the cnspec service.
Improve Google Workspace command
googleworkspace is a tricky one to read so we renamed the Google Workspace provider to google-workspace. Now you can scan Google Workspace with the cnspec scan google-workspace command. Don't worry though; the old command still works to maintain backwards compatibility for automation.
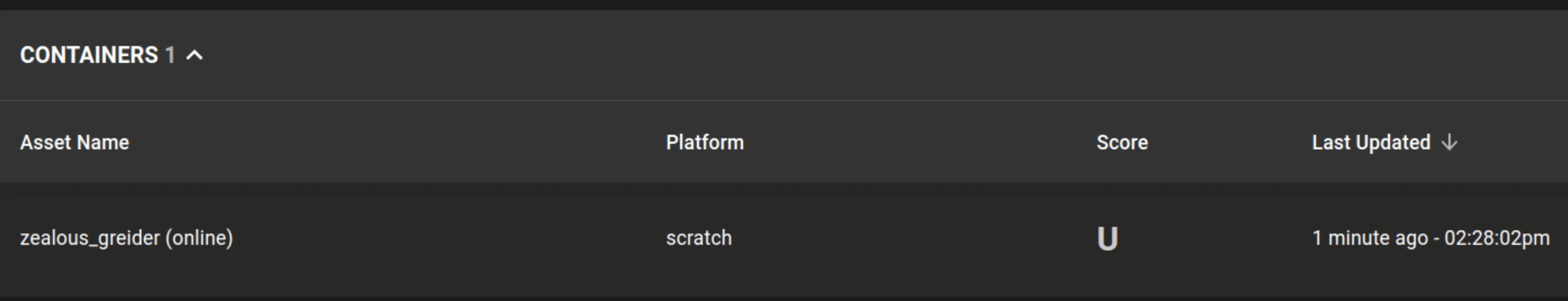
Identify scratch containers
cnspec now detects the platform and architecture of containers built from scratch. Many projects, including Kubernetes, use scratch-built containers.
🐛 BUG FIXES AND UPDATES
- Allow showing asset utilization even if billing is not configured.
- Improve the reliability of CIS GCP Foundation benchmark results.
- Update help and errors for cnspec and cnquery Azure commands to make it more clear you can use both a .pfx and a .pem certificate file.
- Fix parsing of certificate data on Linux with
ports.listeningresource. - Fix parsing of IPv6 data with the
ports.listeningresource. - Fix discovery of Google Workspace assets.
- Fix a remediation step typo in the AWS Security by Mondoo policy.
- Add a tooltip to the
Get Supportlink in the navigation menu. - Fix links to ChatOps integrations in the navigation menu.
- Fix errors running some Google Workspace resources.
- Improve help for GitHub resources.
- Improve the error message when Okta API requests fail.
- Fix a cnspec panic when using the
-o outputreporter when all results produce an error. - Show errors when scanning systems with cnspec.
- Show asset names with cnspec when using the
-o reportreporter.